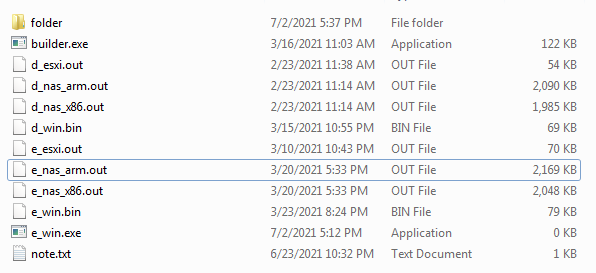
Last week, the builder for the Babuk ransomware family was leaked online. Lab52 has obtained and analyzed this builder sample determining that it is very likely to be authentic. After their recent official move from Ransomware as a Service to data leaks extortions, someone uploaded to virusTotal the ransomware builder for unknown reasons, and it […]
Literature lover targeting Colombia with LimeRAT
In the middle of the current brouhaha in Colombia, besides the intense hacktivism activity, some actors might be trying to take their move. Several campaigns aimed to Colombia have been detected, but today we will talk about one with a couple interesting details in their kill chain. This actor is starting the infection via email […]
Updates on OwlProxy malware
During the analysis of some malicious artifacts collected from an incident, we have recently detected a sample that has caught our attention, the sample was deployed on a server exposed to the Internet and was packed with “VMProtect”. After analyzing this malware sample we could see that it was a recent version of a tool […]
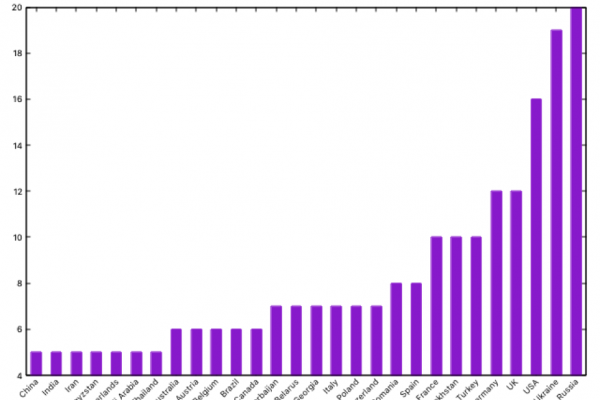
Exploiting APT data for fun and (no) profit
Acquisition and processing When attending to talks about APT -or when giving them- sometimes you hear sentences like “most threat actors are focused on information theft” or “Russia is one of the most active actors in APT landscape”. But, where do all those sentences come from? We have spent a whole night exploiting APT data […]
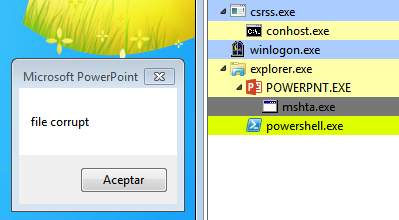
A twisted malware infection chain
Recently, a malware dropper received by mail has caught our attention as we have detected different samples sent to multiple targets in Spain, Portugal, Italy and Norway, although it has probably reached many more European countries. Firstly, it is characteristic that it lands on the victim in PPT format, while it has been much more […]
IOC are dead, long live IOC!
An indicator of compromise (IOC) can be defined as a piece of information that can be used to identify a potential compromise of the infrastructure: from a simple IP address to a set of tactics, techniques and procedures used by an attacker during a campaign. Although when we think about IOC in our mind are […]