For any incident, please contact us
+34 902 882 992
What is an APT?
APT is the acronym for Advanced Persistence Threat. It is the name a hacking group receives, usually sponsored by a Nation-State or a cybercriminal group to carry out cyberattacks on a specific organizations which are considered targets by the threat group and the State which is sponsoring it.
Frequently asked questions:
| 01. Why should we use this service? |
Lab52 offers you a personal and high qualified cyber-intelligence feed. Through the Lab52 open service we can keep you updated and secured from the most relevant Advanced Persistence Threat groups and their cyber-attacks. The service's main goal is to show your organization the most relevant IOCs (Indicators of Compromise). Our service stores an important IOC data base to protect your organization from important APT cyber-attacks.Moreover, it keeps the most updated IOCs as our service is in constant development and we are constantly researching new cyber threats and new ways to keep our customers well protected.Furthermore, Lab52 considers intelligence analyses and geostrategic researches as fundamental tools to anticipate APTs. Therefore, this service keeps you well informed about the most relevant changes around the world. With the IOC and our permanent geostrategic review, your organization will always be well protected from the worst cyber threats and prevent you from becoming a victim.
|
| 02. What kind of companies can be threatened by APTs? |
Currently, all kinds of organizations could be an APT target. The most precious comodity in an organization is the information stored in their IT systems and, in operative terms, the proper running of the same. It does not matter how big the targeted organization is or how significant it is in its sector, as there are several records of all kinds of sabotage and espionage cyber-attacks. All the private information of an organization is relevant for an APT. These threat groups usually seek to steal technical and corporate classified information to gain an advantage in the private market against the targeted organizations or perhaps a Nation State looking for an advantages against other countries. |
| 03. How can we protect our company from APTs? |
One the most effective method to be protected is to identify cyberattacks through the IOC. The Lab52 service regularly sends the most recent APT IOCs, which is the most valuable information for identifying a cyberattack in a host or on the web. These Indicators of Compromise are composed of domains, IP and hashes. The Lab52 team is permanently providing new IOCs which are the result of compromised system cases. All threat groups design and develop new ways to cyberattack their targets. In order to carry that out, they have to create new attack infrastructure, which once disclosed, the potential victim may identify and neutralize the cyberattack.

|
| 04. How can we be infected by an APT malware? |
In general terms, an APT cyberattack procedure would have several ways to carry out the attack and compromise the IT systems of the victim. Threat groups usually the following steps:Firstly, threat groups choose their strategy and victim (organization, group or person) target. The APT group decides which kind of information would be worth collecting or even which kind of operation systems would be interesting to sabotage.Secondly, the APT group starts collecting information about their victims from open sources and other tools. E.g. Social media, newspapers or from HUMINT processes.When the threat group has gathered enough information about their victims, it begins the “hook” phase by using, for example, a spear phishing email with a "bait" with the aim to persuade the victim to download the document or to click on the link with the malware.In this phase the downloaded malware compromises the IT systems of the victims and begins to spread it into the internal network systems subsequently detecting the targeted information to be stolen by the threat group.In the last phase, the malware begins the data extraction from IT systems and transfers it to the threat groups’s Command and Control.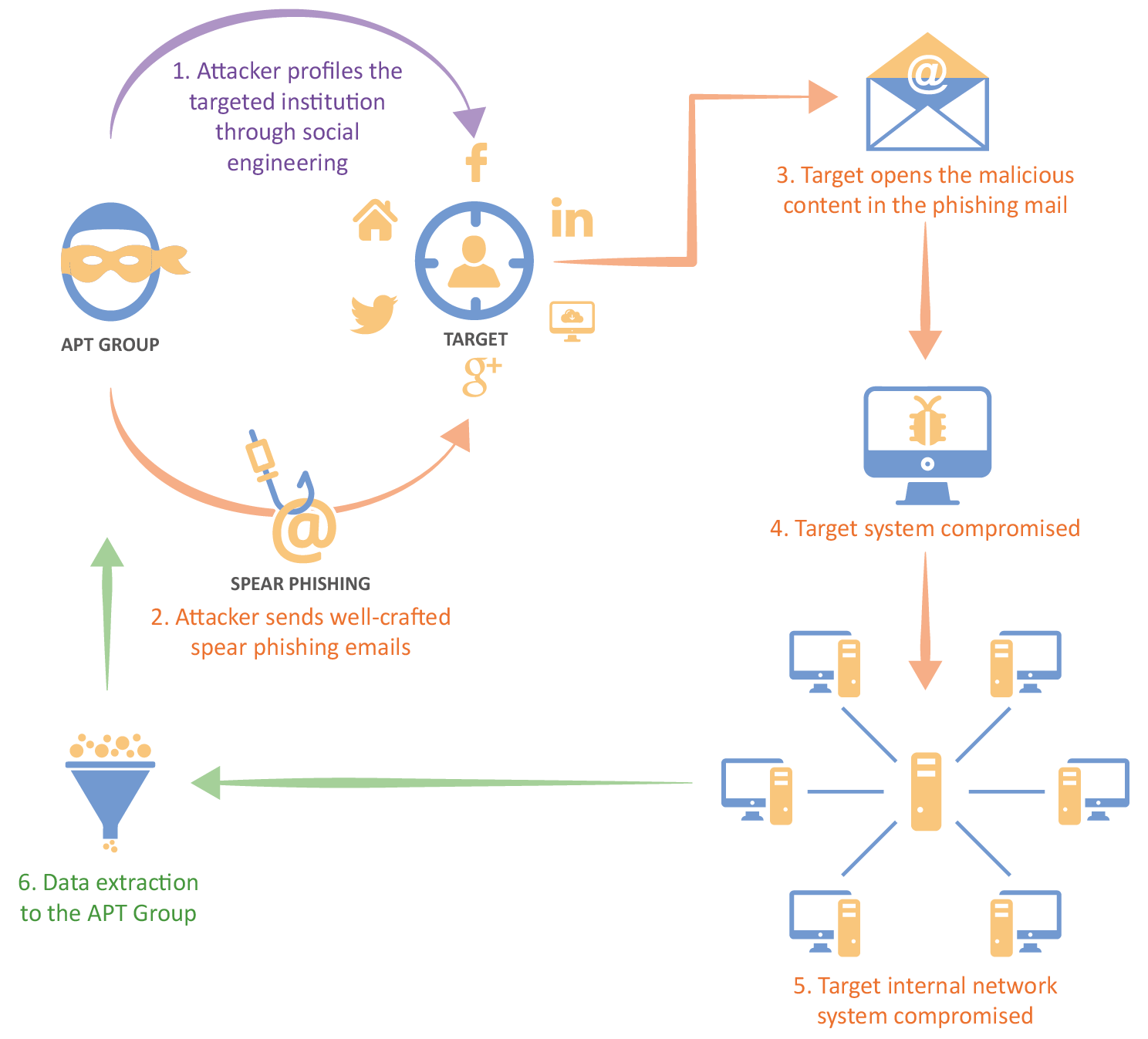
|
| 05. Why should we subscribe to the service? |
Our free feed service allows you to be forewarned about the most recent global changes and the latest threat groups which could target your organization. To improve your cybersecurity, new IOCs will be sent to you automatically, keeping your organization protected and safeguarded from them. Furthermore, Lab52 will update you about the most significant geostrategic and political changes that could affect the cybersecurity of your organization. |