After the rise of tensions between the US and Iran due to the US military operation that ended the life of the Iranian General Qasem Soleimani and the Iraqi Commander Abu Mahdi al-Muhandis ([12]), Iran carried out an attack with missiles against two US military bases located in Iraq ([13]). These events have generated a […]
Intelligence operation against targets in Indonesia
Lab52 has detected malicious activity targeting Indonesian victims. This activity could be linked to an intelligence operation. We have been tracking this activity since December 27th of 2019 The main tools of this threat actor, are built as DLL files, and launched with this commands: “C:\Windows\System32\rundll32.exe” shell32.dll,ShellExec_RunDLL regsvr32 /s C:\ProgramData\pubpool.dll /i:process104.dll “C:\WINDOWS\system32\regsvr32.exe” /s C:\ProgramData\pubpool.dll /i:process104.dll […]
APT-C-36 recent activity analysis
From Lab52 we have been tracking during the last months the activity of the group APT-C-36. This group was named and publicly introduced by the Company 360 [1] last year. In this article is highlighted as the main objective of the group, the companies located in Colombia. If you don’t know APT-C-36, we recommend the […]
APT27 ZxShell RootKit module updates
Within the toolset of the different APT groups, one of the most interesting elements and the one that generally worries the most, are their capabilities in Ring0, generally RootKit/Bootkit type threats that act with the maximum level of privileges. An example of this type of threats is the RootKit module of ZxShell RAT used by […]
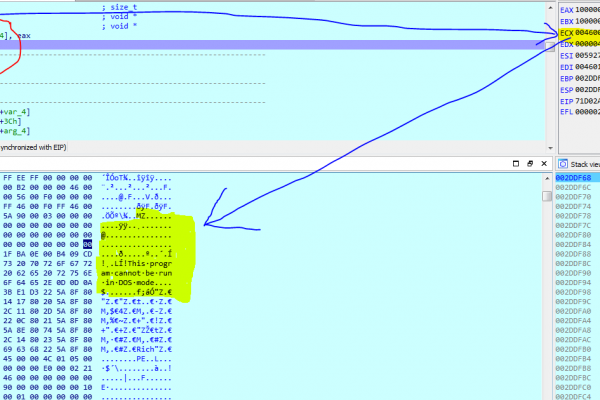
TA428 Group abusing recent conflict between Iran and USA
Recently, a suspicious document has caught our attention due to its recent creation date (06-01-2020) and its title “How Swuleimani’s death will affect India and Pakistan.doc” which is directly related to recent political events between Iran and the USA. The document is in RTF format, and has an OLE object related with the Equation Editor. […]
CNA tactics: a first approach
Today’s post is a doctrinal and metaphysical one… really, it’s a pain. You’ve been warned 🙂 While talking about Computer Network Operations (CNO) we consider three capabilities or actions: CND, CNA and CNE (Defence, Attack and Exploitation respectively); while CND is obviously about technological defence of IT infrastructures against also technological attacks -not about a […]