The Lab52 team has analysed a cyber campaign in which attackers deploy a new variant of the PlugX malware. Both the infection chain and the various artefacts used in the cyberattack share multiple similarities with the SmugX campaign, attributed to threat actors Red Delta and Mustang Panda, allegedly linked to the Chinese government.
This time, the actors deploy an MSI file on victim machines containing a legitimate executable (OneNotem.exe), a malicious DLL (msi.dll) and a DAT file (NoteLogger.dat). The legitimate executable loads via DLL side-loading the malicious DLL and the malicious DLL decrypts and loads the DAT file into memory, which is the PlugX malware. However, this new campaign shows variations compared to previous campaigns. The main differences are:
- The malicious DLL is written in the Nim programming language.
- This new variant uses its own implementation of the RC4 algorithm to decrypt PlugX, unlike previous versions that use the Windows Cryptsp.dll library.
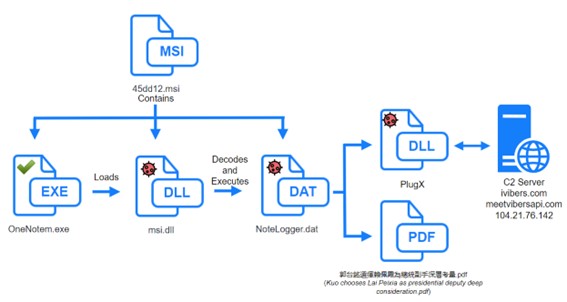
Killchain
The installer file 45dd12.msi contains the files msi.dll, NoteLogger.dat and OneNotem.exe and, on user execution, it copies them to the directory “C:\UsersersuserAppData“.
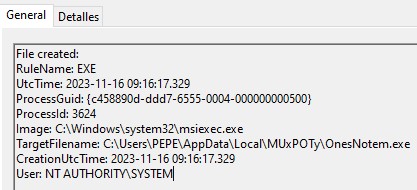
Right after, the MSI file copies OneNotem.exe to one of the following folders:
- C:\Users\<username>\VirtualFile
- C:\Users\Public\VirtualFile
- C:\Users\<username>\SamsungDriver
- C:\Users\Public\SamsungDriver
- C:\Users\Public\SecurityScan
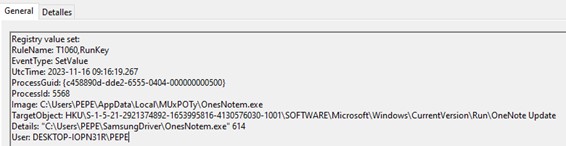
In order to obtain persistence on the infected machine, the registry key “HKEY_LOCAL_MACHINE/ SOFTWARE/ SOFTWARE/ Microsoft/ Windows/ CurrentVersion/ RunOneNote Update” is added, which executes the legitimate OnesNotem.exe binary followed by a numeric parameter.
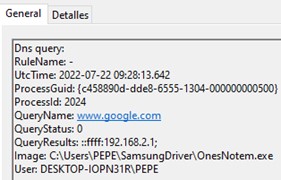
The malware then creates the process OneNotem.exe that will first contact with www.google.com to check if the computer has internet connection and then contacts the C2 domains ivibers[.]com and meetvibersapi[.]com. The OneNotem.exe process also creates a mutex to prevent the execution of a second instance.
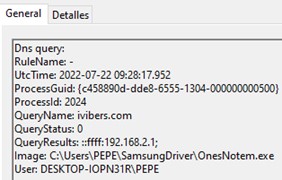
Moving forward, Lab52’s team has analysed each of the various artefacts contained in the MSI file to discern their specific roles or purposes.
MSI.DLL
This DLL contains two malicious functions, the NimMain function and the MsiProvideQualifiedComponentW function.

The DllMain function has been modified to add the call to NimMain which will be executed when the library is loaded by the OneNotem.exe process.
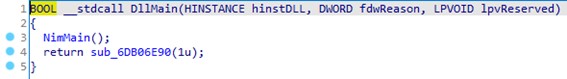
This will load the functions necessary for the execution of the malware. This technique is used to reduce the number of exported functions to make the analysis and possible detection of the malicious library more difficult.
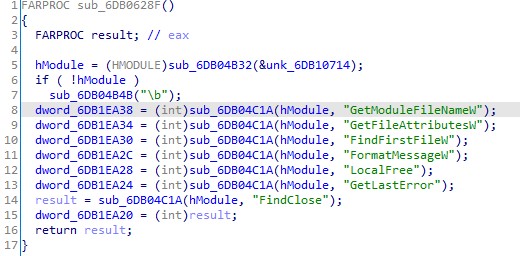
When the legitimate executable calls the MsiProvideQualifiedComponentW function it will load the NoteLogger.dat file with the CreateFileW function.
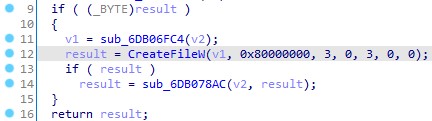
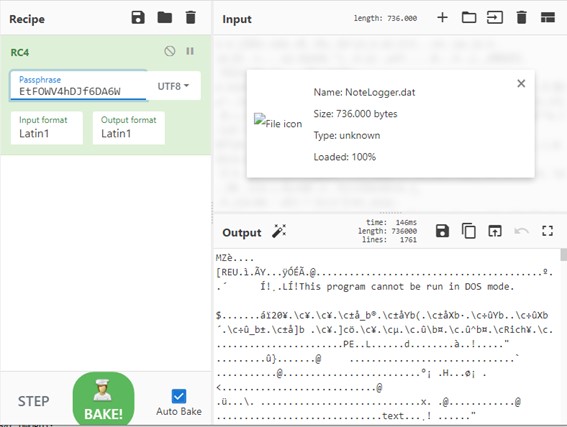
The malware will then copy the contents to a memory section and use the RC4 algorithm and the key EtFOWV4hDJf6DA6W to decrypt a DLL contained in the NoteLogger.dat file, which is a PlugX malware variant.
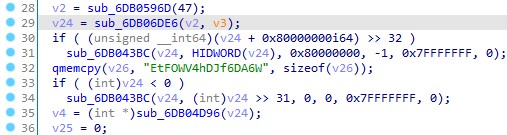
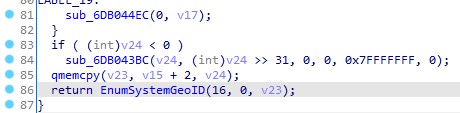
Finally, the DLL will be executed at location 0x00 in the memory page where it resides using the EnumSystemGeoID callback.
NoteLogger.dat
This file contains an encrypted malicious DLL, a PlugX variant, containing in position 0x00 a small shellcode that will call the only function it exports. The execution of this shellcode is indispensable for a correct execution of the malicious DLL.
The malware will decrypt the configuration, which is located in the “.data” section, similar to other samples from the SmugX campaign.

The following is the decipher configuration.
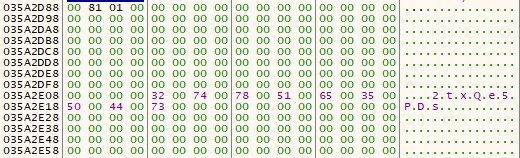
{
"str_one": "",
"str_two": " 2txQe5PD",
"campaign_id": "tw",
"document_name": "郭台銘選擇賴佩霞為總統副手深層考量.pdf",
"ips": [
{
"ip": " ivibers.com",
"port": 443,
"is_https": 1
},
{
"ip": " ivibers.com",
"port": 443,
"is_https": 1
},
{
"ip": " meetvibersapi.com ",
"port": 443,
"is_https": 1
}
]
Decoy PDF
The name and content of the lure used by the attackers seem to indicate that the targets of this campaign are no different from those seen so far in the SmugX campaign (diplomats and government entities). The lure uses the upcoming Taiwanese presidential election in January 2024 to capture the interest of its victims. The document refers to Terry Gou’s announcement in September this year declaring his independent candidacy for Taiwan’s presidential election, with Lai Peixia as his right-hand man.
Terry Gou – who was founder and CEO of the Taiwanese multinational electronic components company -one of the largest suppliers to the United States, Europe and Japan and part of the semiconductor manufacturing cluster along with TSMC, or MediaTek- is running to bring down the current Taiwanese government, to reduce geopolitical tension and to stabilise the situation.
Lai Peixia is a singer, activist and politician with dual US-Taiwanese citizenship known for defending human rights. It seems that the attackers have used a decoy that addresses an event of high interest to political, diplomatic and governmental figures in Taiwan, as the presentation of the presidential candidacy of Terry Gou and Lai Peixia, that is particularly relevant because of the links these two political figures have with the Western bloc, the effect that their figure as president could have on Taiwan’s trade relations with China, the United States, Europe and Japan and their impact on the technology race in both blocs.

Indicators of Compromise
| c7ec098093eb08d2b36d1c37b928d716d8da021f93319a093808a7ceb3b35dc1 |
| 651c096cf7043a01d939dff9ba58e4d69f15b2244c71b43bedb4ada8c37e8859 |
| 908ff3a80ef065ab4be1942e0d41583903f6aac02d97df6b4a92a07a633397a8 |
| c6ef220d0c6e9015bdfb7977ff15e7f2c4c0dbfcd3b28ffb3066fe6d21251322 |
| 8af3fc1f8bd13519d78ee83af43daaa8c5e2c3f184c09f5c41941e0c6f68f0f7 |
| 45dd12.msi |
| msi.dll |
| NoteLogger.dat |
| 郭台銘選擇賴佩霞為總統副手深層考量.pdf |
| ivibers[.]com |
| meetvibersapi[.]com |



Leave a Reply