Actor Background and Tool Distribution
A new offensive OT framework has been identified and offered for sale on a platform accessible via the TOR network, promoted by the “APT IRAN” channel. The administrators have indicated that this is the most extensive industrial and military control network framework to date within the Black Industry (BI) ecosystem.
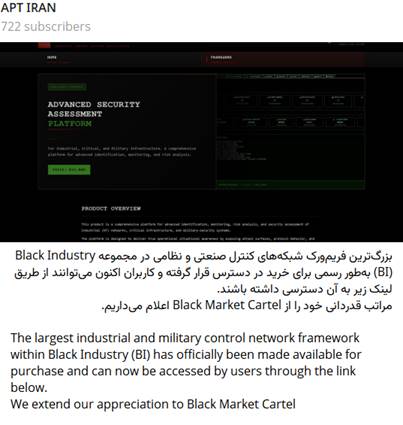
The tool can be purchased through the TOR network and is being promoted in a portal called “Black Market Cartel”; however, the published purchase link seems currently broken. The day before the message was posted, APT Iran stated that they would release a demo primarily focused on “the insecurity of the United States of America.”
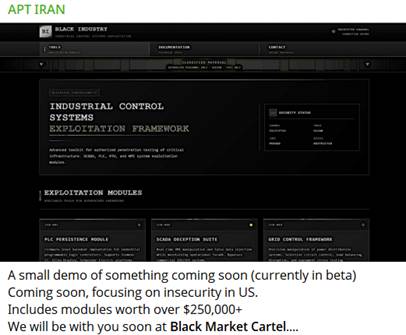
The site hosts the promotion and sale of an alleged offensive framework targeting critical, industrial, and military infrastructure (OT).
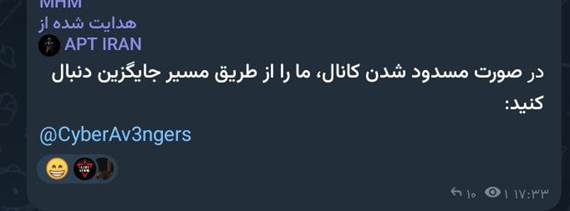
APT Iran is closely linked to CyberAv3ngers, to the point where it is widely believed to be a rebranding of this hacktivist group, as much of their activity overlaps. The message in the following image translates to, “If the channel is blocked, follow us via an alternative link.”
CyberAv3ngers, in turn, is closely linked to the Islamic Revolutionary Guard Corps (IRGC). United States intelligence agencies document that the group works closely with an IRGC Cyber Command (IRGC-CEC). It is worth noting that there are even some sources who claim that APT Iran is, in essence, a subdivision of the IRGC-CEC.
It is important to note that on January 26, 2026, the “APT Iran” channel was deleted, along with most prior mentions of Black Industry on Telegram. In contrast, a new Telegram channel called “Cyber4vengers” has been created.
Identified Capabilities
The following is a list of the tools and modules explicitly mentioned in the web page, detailing their functionalities according to the promotional text and visible system logs. The information gathered from the images and descriptions on the website was used to comment on the capabilities.
ADV-PLATFORM-01 (Security Assessment Framework)
This is the only tool marked as “AVAILABLE FOR PURCHASE”.
General purpose: Advanced platform for identifying, monitoring, and analyzing risks to industrial and military infrastructure.
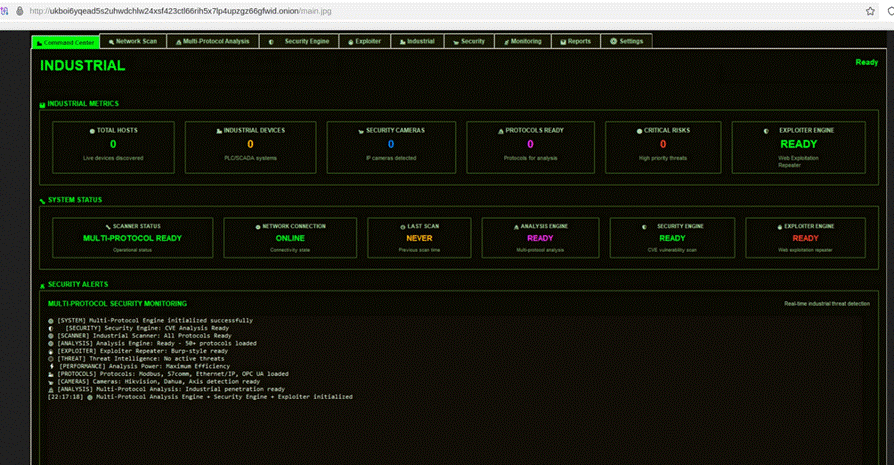
Technical capabilities:
- Network scan
- Multi-Protocol Analisys
- Security Engine
- Exploiter
- Industrial
- Security
- Monitoring
- Reports
- Settings
The logs load modules that suggest OT and other IT-specific scanning and exploitation capabilities such as:
- Exploiter Repeater: Burp-style ready. This suggests the ability to intercept and manually resend packets (Replay attacks) similar to Burp Suite, but focused on industrial protocols.
- Multi-Protocol Scanning: Loaded support for Modbus, S7comm, Ethernet/IP, OPC UA.
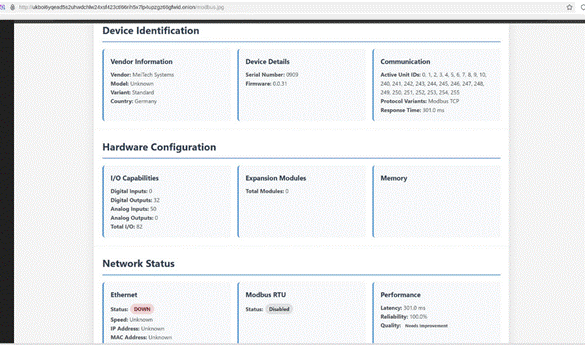
- CCTV Recognition: Specific detection module for IP cameras from Hikvision, Dahua and Axis brands.
- Vulnerability Engine (CVE): The system status displays SECURITY ENGINE: CVE Analysis Ready, suggesting an integrated database of known vulnerabilities.
In addition, it is stated that it has the following Operational Capabilities:
- Zero-Footprint: Designed to leave no forensic traces on compromised systems.
- Air-Gap Penetration: Refers to specialized modules for physically isolated systems.
- Mission Impact Analysis: Mapping the attack surface based on mission criticality (not just open ports).
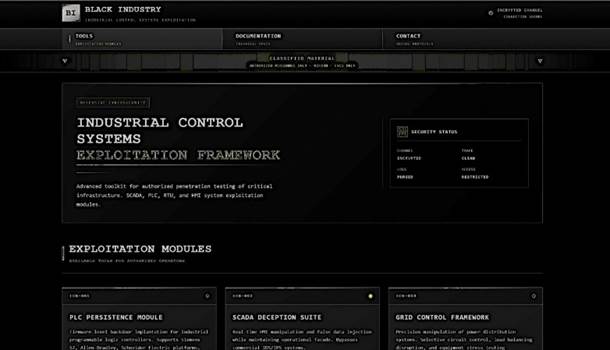
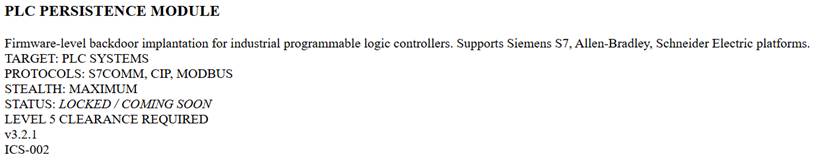
ICS-001 (PLC Persistence Module)
Marked as LOCKED / COMING SOON. Access requires “Level 5 Clearance”. The method for increasing clearance is unknown, though it likely depends on earning the group’s trust.
- General purpose: Implementation of firmware-level backdoors in Programmable Logic Controllers (PLCs).
- Target Platforms: Siemens S7, Allen-Bradley, and Schneider Electric.
- Protocols: S7COMM, CIP, MODBUS.
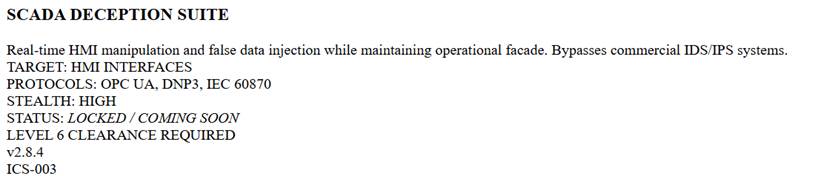
ICS-002 (SCADA Deception Suite)
Marked as LOCKED / COMING SOON. Accessible only with “Level 6 Clearance”.
- General purpose: Real-time manipulation of HMI (Human-Machine Interface) and data injection.
- Evasive Capability: Designed to bypass commercial intrusion detection systems (IDS/IPS).
- Protocols: OPC UA, DNP3, IEC 60870.
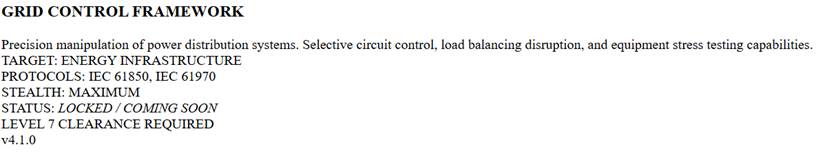
ICS-003 (Grid Control Framework)
Marked as LOCKED / COMING SOON. Accessible only with “Level 7 Clearance”.
- General purpose: Precise manipulation of electrical distribution systems.
- Functionalities: Selective circuit control, load balancing disruption, and equipment stress testing.
- Protocols: IEC 61850, IEC 61970.
Conclusions
It cannot be confirmed that the tool’s web resource is not a honeytoken-style decoy designed to identify potential adversaries, several factors suggest it is a functional tool. These include its hosting on an onion network, its publication by the APT Iran group, which is linked to the IRGC, the level of detail provided in the tool’s description and the removal of its sale from the internet. Collectively, these elements indicate that the tool is actively used by hacktivist groups and nation-linked actors associated with Iran, demonstrating that this group’s capabilities and organizational structure are more sophisticated than previously expected.
Finally, although the goals behind this sale are unknown, the tool may be intended to support the group’s financial objectives. It is, however, more likely motivated by other considerations, such as obstructing attribution or contributing to broader destabilization efforts.




Leave a Reply