During 2020 Leonardo analysts discovered and published a very in depth analysis of a threat known as Penquin, attributed to the APT group Turla. 32-bit samples of this threat had been detected and analyzed by Kaspersky before, but the analysis in this most recent publication was focused on a new 64-bit sample. It firstly caught […]
TokyoX: DLL side-loading an unknown artifact (Part 2)
As we mentioned in the previous post, we have performed an analysis of the threat which, lacking further information, we have not been able to identify it as a known threat. Thus, for the moment, we will keep referring to it as TokyoX. This threat can only be found in memory, since it is encrypted […]
Updates on OwlProxy malware
During the analysis of some malicious artifacts collected from an incident, we have recently detected a sample that has caught our attention, the sample was deployed on a server exposed to the Internet and was packed with “VMProtect”. After analyzing this malware sample we could see that it was a recent version of a tool […]
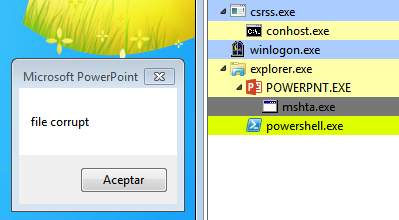
A twisted malware infection chain
Recently, a malware dropper received by mail has caught our attention as we have detected different samples sent to multiple targets in Spain, Portugal, Italy and Norway, although it has probably reached many more European countries. Firstly, it is characteristic that it lands on the victim in PPT format, while it has been much more […]
Recent FK_Undead rootkit samples found in the wild
Malware that works at Ring0, generally known as rootkit, is one of the most concerning in many environments because it shares privileges and capabilities with antivirus and EDR solutions, which greatly complicates its detection as far as they can tamper and/or hide the data that allows its detection with relative ease. One of these examples […]
Mustang Panda Recent Activity: Dll-Sideloading trojans with temporal C2 servers
Recently, from Lab52 we have detected a recent malware sample, using the Dll-Sideload technique with a legitimate binary, to load a threat. This particular sample has a very small DLL, that loads an encrypted file, which after being decrypted consists of a sample of the PlugX Trojan. This technique, and final threat together, consists of […]