APT is the acronym of Advanced Persistent Threat. This is the name that a group of attackers receives which is usually related to a Nation-State to carry out cyberattacks on specific organizations that are considered targets by the threat group and the State which is sponsoring it.
APT groups usually develop cyberattacks to disrupt the IT systems, steal data and sabotage the operations systems of the victim. The way an APT could develop their cyberattacks may depend on each campaign. There are phishing email campaigns that are designed to be very personalized to their targets, however, sometimes the campaigns are completely generic and the APT tries to spread their cyberattacks indiscriminately, attempting to collect information in a massive way.
In general terms, there are two main goals for all the APT when they execute a cyberattack: On the one hand, the APT execute a operation to steal classified information from the targeted organization through their cyberattack. Also, the APT groups could try to disrupt some victims’ operations or even destroy some critical infrastructure that could be fundamental for the normal running of the organization.
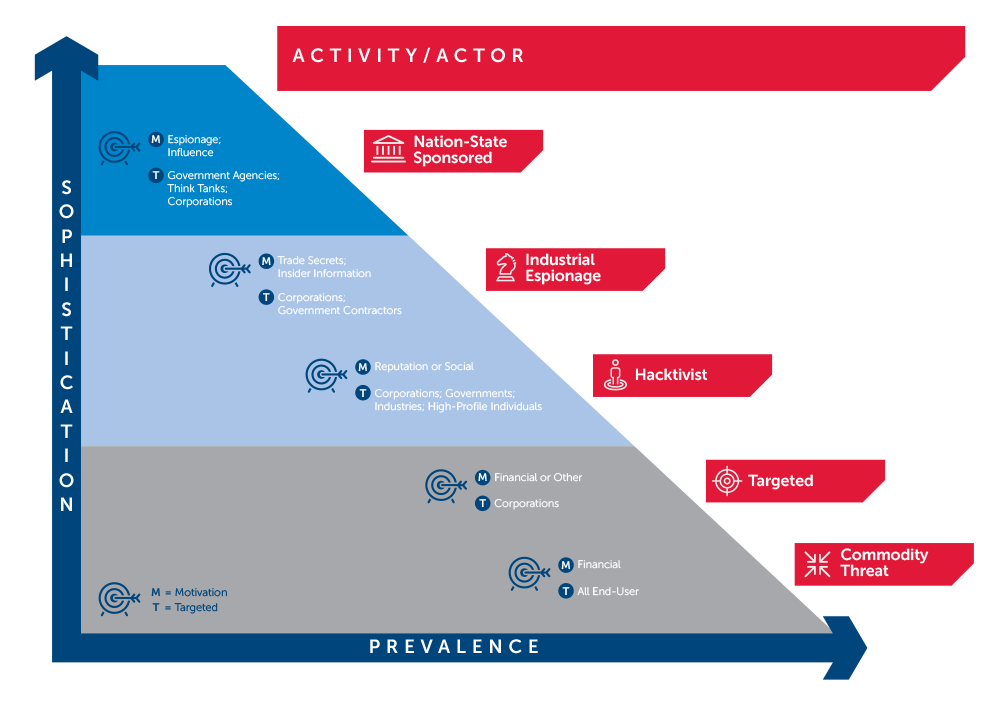
As the graphic shows, an APT is managed and sponsored by a Nation-State. Consequently, its motivations are focused to develop cyber espionage operations to collect classified information. Moreover, the APT can execute cyberattacks with motivations and targets related to stealing trading secrets, disrupting operations systems and damaging the reputation of a company or State.
The main goal of the Nation-States which are sponsoring APT is to get relevant influence in international relations and in worldwide international trading . As can be seen on the graphic, APTs are on the top of the ranking cyber-threats.
Is it necessary to be a big company to become a target for an APT?
Not at all. All kind of organizations would be relevant for the interests of an APT. There are several records from a lot of researches which prove that the threat groups are very interested in stealing relevant and classified information. The worth of the company will not be so significant for the APT as the worth of the information the organization holds. Also, it is not necessary to be the CEO of the company to be the target of the threat group. In several occasions the APT is looking to steal technical or corporative information that is managed by technical positions in the organization. Everybody would be a target for an APT.
How could I find out if I am an APT’s target?
Lab52 designed an easy-going and free tool to check if you would be a potential target for the most relevant worldwide APT groups. The main goal of this tool is to identify whether a specific APT would be interested in cyberattacking your organization. You just have to provide some information about your organization and we will match that input with our data base and cyber-intelligence records.
Once the main threat groups are identified, Lab52 offers you the IOC (Indicators of Compromise) to apply a defensive strategic plan against the main threat groups which are targeting your company.
How could I be saved from these APT groups?
Our tool is able to give you a significant quantity of IOC related to cyberattacks executed by the APT which would be a potential threat for your organization. Through the “framework open IOC” we can identify the behaviour of the APT’s malware. Its XML files will allow you to verify if your organization’s IT system has been compromised. If you detect that you have been compromised, you should apply the “IOC finders” to analyse if the rest of VLAN devices are infected as well. In the last stage, we recommend getting in touch with us by email for any questions or threat identification after applying this procedure. We would be glad to advice you about how solve your incident.





Leave a Reply