The S2 Group’s intelligence team has identified through adversary tracking a new phishing campaign by Snake Keylogger, a Russian origin stealer programmed in .NET, targeting various types of victims, such as companies, governments or individuals.
The campaign has been identified as using spearphishing emails offering oil products. These emails will contain a zipped attachment that uses the legitimate jsadebugd.exe binary and the Sideloading Dll technique to load Snake Keylogger into the legitimate InstallUtil.exe binary. jsadebugd is a legitimate Java utility used for debugging processes. However, its malicious use has recently been observed, something that has not been documented before.
Snake Keylogger is distributed via a Malware-as-a-service (MaaS) model, previously used by different groups against different targets. One example is its use in campaigns against Ukraine by UAC-00411 or TA558.2
The increase in geopolitical tensions in the Middle East, with the conflict between Iran and Israel and the recent US involvement, could have a direct and global impact on logistics and oil prices.
This element could be used within social engineering phishing as has been detected in this case. This could be an indicator that the target of the campaign could be against organisations in the oil sector. On the other hand, they could exploit this theme due to the growing fear that is being generated in the Middle East regarding the possible increase in the price of oil and possible logistical problems in the event of a hypothetical closure of the Strait of Hormuz.
Within the body of the email it can be seen that it is intended to impersonate one of Kazakhstan’s main oil companies: LLP KSK PETROLEUM LTD OIL AND GAS. Kazakhstan is one of the largest oil producers in Central Asia and a major gas producer.2
Analysis
The campaign will use spearphishing emails offering oil products with a malicious attachment containing a zipped file.
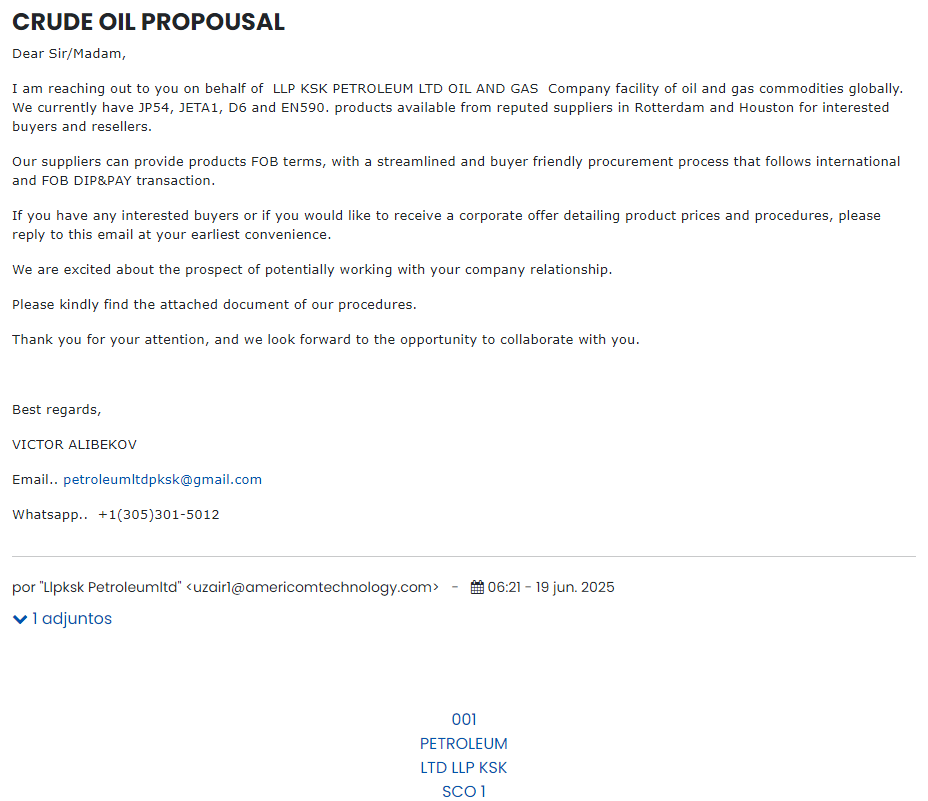
This archive will contain a number of binaries, including the legitimate executable jsadebugd.exe vulnerable to the Sideloading Dll technique which will have been renamed to ‘001 PETROLEUMLTD LLP KSK SCO 1 ORIGINAL (1).exe’. When executed by the user this executable will load the malicious DLL jli.dll.
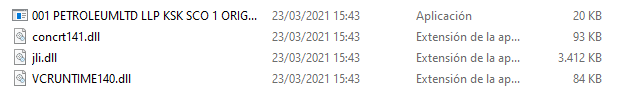
The Snake Keylogger binary will be stored inside the file ‘concrt141.dll’. To evade detection by security tools, binary data will have been added to the beginning of the file, just before the MZ header.
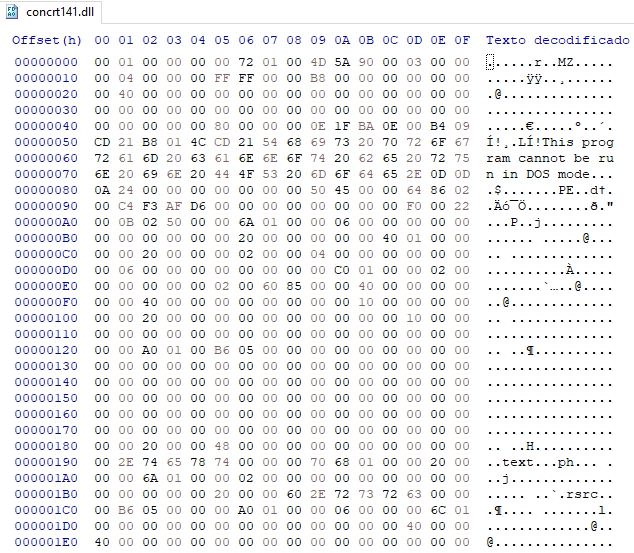
This binary will be injected into the legitimate InstallUtil.exe process. As a form of persistence, the contents of the compressed file will be copied to the folder “%USERPROFILE%\SystemRootDoc”. The persistence key “SOFTWARE\Microsoft\Windows\CurrentVersion\Run\001 PETROLEUMLTD LLP KSK SCO 1 ORIGINAL (1)” will then be created with the command “cmd.exe /C start “” /D “%USERPROFILE%\SystemRootDoc” “%USERPROFILE%\SystemRootDoc\001 PETROLEUMLTD LLP KSK SCO 1 ORIGINAL (1).exe”.
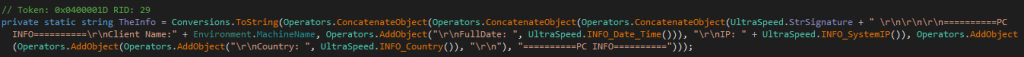
The SnakeLogger malware will send the IP of the computer along with the country of origin using legitimate websites such as reallyfreegeoip.org and checkip.dyndns.org.
Snake Keylogger will also exfiltrate passwords from various applications and browsers.
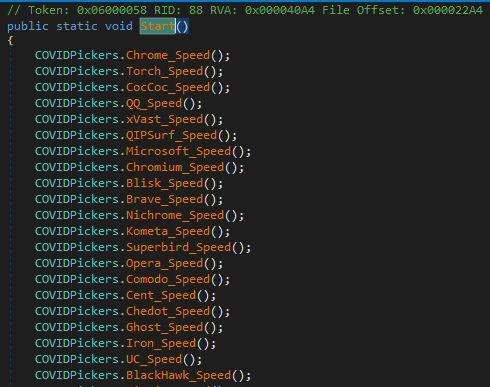
Below is the complete list of browsers from which data was collected by the sample.
- Google Chrome
- Google Chrome Canary
- Chromium
- Brave
- Vivaldi
- Comodo Dragon
- Blisk
- Torch
- Cốc Cốc
- QQ Browser
- xVast Browser
- QIP Surf
- Microsoft Edge
- Nichrome Browser
- Kometa Browser
- Superbird
- Opera
- Cent Browser
- Chedot
- Ghost Browser
- SRWare Iron
- UC Browser
- BlackHawk Browser
- Citrio
- Uran Browser
- Falkon
- Sputnik Browser
- CoolNovo (ChromePlus)
- Sleipnir
- Kinza
- Amigo
- Epic Privacy Browser
- 360 Browser (English)
- 360 Browser (China)
- XPom Browser
- Orbitum
- Iridium Browser
- 7Star Browser
- Mozilla Firefox
- SeaMonkey
- Comodo IceDragon
The full list of applications collected by the sample is shown below.
- Mozilla Thunderbird
- Microsoft Outlook
- Foxmail
- FileZilla
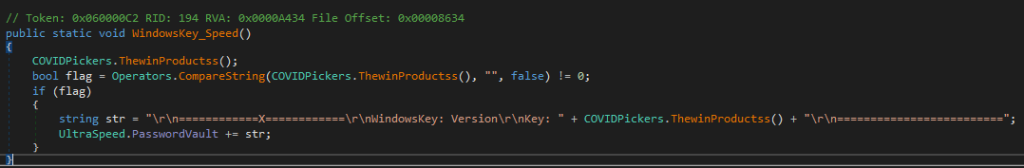
In addition the malware will collect the Windows product key of the device.
All this information will be exfiltrated through the SMTP protocol by sending mails from the account serverhar244@gpsamsterdamqroup[.]com to harrysnakelogger@dklak[.]cam.
In addition to the analysed sample, 29 others have been identified that also make use of the legitimate jsadebugd.exe binary. This behaviour has not been observed previously and seems to be characteristic of this specific campaign. All the samples have been attributed to the same group, as they deploy variants of the Snake Keylogger family, which reinforces the hypothesis of a coordinated operation led by the same actor.
Conclusion
This article analyzes how the actors behind Snake Keylogger take advantage of the current geopolitical situation, in the context of the recent conflict between Iran and Israel and the possible closure of the Strait of Hormuz, to extend its reach and infect new targets. In addition, the group behind this campaign is reportedly using jsadebugd, a legitimate Java executable vulnerable to the DLL sideloading technique, the use of which for malicious purposes has not previously been observed. This suggests an evolution in the group’s tactics, aimed at evading established detection mechanisms.
The current situation of uncertainty in the Middle East could lead to increased interest from international energy companies in looking for new viable options to buy or sell oil products. In this case, this campaign could seek to take advantage of this profile of energy organisations.
References
- [1] SOC Prime, FormBook and Snake Keylogger information stealers massively distributed via email using RelicRace and RelicSource malware, available online at https://socprime.com/blog/formbook-and-snake-keylogger-information-stealers-massively-distributed-via-email-using-relicrace-and-relicsource-malware/
- [2] Packetlabs, TA558 “SteganoAmor” uses steganography targeting unpatched MS‑Office apps, available online at https://www.packetlabs.net/posts/ta558-steganoamor-uses-steganography-targeting-unpatched-ms-office-apps/
- [3] Trade.gov, Kazakhstan – Oil and Gas Equipment and Services, available online at https://www.trade.gov/country-commercial-guides/kazakhstan-oil-gas-equipment-and-services
Indicators of Compromise (IoC)
Network indicators
| serverhar244@gpsamsterdamqroup[.]com | Sender |
| fiber13.dnsiaas[.]com | Sender server |
| harrysnakelogger@dklak[.]cam | Receiver |
Samples
| f099cb320a26b6284e9ca24b352b19d2109bb3df0beeded3c34377c9b934ed3 b | 001 PETROLEUMLTD LLP KSK SCO 1 ORIGINAL (1).zip |
| 9dae36cf2664e4bd348b1c7bcd9e886243fdd86e04d854e9a49e80ce358aa868 | concrt141.dll |
| 18e3d1542d9d375f2e1d4631e03e9874fca9a1655ee6d01121d0c94e138be17 4 | jli.dll |
| 76618263ac3d71779c18526c5ecc75a025ad0c78212b6a2bc089b22a1b8ca567 | jsadebugd.exe (Legit) |
| 2b7602cc1521101d116995e3e2ddfe0943349806378a0d40add81ba64e359b6 c | Vcruntime140.dll (Legit) |
Related samples using jsadebugd.exe
- 0171212441aef19491692062218aaa6fba9684f59e162691ab056a7369569ad9
- 07dd7611034b2199726f006f93f144751d1f94e596908f8c5c2f5dcd245530af
- 0877f1e39454438733df34bfec11fc23023a449c6ece07f0d15a852d140e64c5
- 132ac2a27f43b1a830986c6d74b1e5cc855b248c93fa69893421c79d73a21fdb
- 19c4eac334c6218e8a9fae3c0bae8a28beb75c474780f3a567974e96f94cf35a
- 2e52628677cd6615c58b99ba3a85b3e41f60d752e2651293dcddcb814b9f6d18
- 3d0df3b1329d9f7dae79678325e3855734a0f31f995c32fe2ec6632d5043e40c
- 4855d6832e2889cfb0047e515b761c365bf8792ff30a84571ace896b7903f702
- 54468a4c1261c1c3f4136854c29a50080be77416d040b083ac51776c957a1182
- 5739aa1e1e86c11fb29cc40451bd55a06f3b8a98a58d364525a571d6b3c5c44c
- 6d7158bf300a5a8769d106500a60141e63436bfc35cab1d24e047aad1dc880ce
- 7cc53ec159a15cb2eacb8db7de25b35f2ef0e7aef0f3aa712c13560de16ddc20
- 7daf0aa227d0e846edd1229cd744e3afd8ca3898e12836605d8f08038ef34203
- 830703e20378110b1db917fcd498fa731aafed37fb1055c002693662053ad13c
- 9f092c5069fdf376163326428b27d3f44283f6a5cc7fc6e57b5f8584919b7d8b
- abec75593c542693e475be1d3b6e51cffcb599acaa5089ea578f13f30316d628
- b33d93e82b4a964c1306d40b054e6a2703e050357a513ab8873651dd4d669f4b
- c9065f726d9bce286d1df97516f7fa04004fa4fea0719933926a58b8cb93b9a0
- ccde5a1ae465a65b483f8f97e3d4b97957fc869cc4aca8b4fdd02a821aaf45a8
- d244fede5f1b101146f733ec426fc7bb604ee4a7ab51ee88d8055b6866c7f708
- d3ca4ed0a462c73c55d3aed4cfa5a969eacfdde152f67437fe3bb14fefb17612
- d44bae3e448d78cdb976b7f811be53f32efb28d0d2ba964d09edd79a95dcc4b3
- dbf6d6a302e7c9f7ef1bbc32e4efd61ded782e08ef16ad86a7a4858b4e1e9d9d
- e31eda04b9ee78bb41c990eca89554ffadab27a5c47d5efd66f11f5947958dde
- eb56af5727614192c73d71b8a7c22933872076cb9e62380320dfe09937d4f052
- f099cb320a26b6284e9ca24b352b19d2109bb3df0beeded3c34377c9b934ed3b
- f44877b93c347c93a38c05c9144030d144a4af7c243a57957479448c23b081cd
- f4cc2b43480778392d4ea48e6af1ac47f646b3c3f295797752be2be20d13067e
- f57ac8aa79dbe0a7a746f8de245361d912fe1f59f43d5cde835e94a2dbf0cfdb
- fe223090ea59abc54312c48ed89765ea5c8821df78134adc094cd799973dde39




Leave a Reply