From Lab52, we are very aware that in the fight against ransomware, we must not focus solely on the final artifact but must pay attention to every phase of deployment. Unfortunately, it will not always be possible to accurately identify the entire infection chain, as highlighted in the latest statistics by Coveware.
The objective of this post is to contribute to early detection by sharing relevant parts of the observed infection chain in two ransomHub cases. In a recent post of Unit42 (Paloalto), a new variant of this ransomware is mentioned. In our case, one of the samples (sample2.exe shown bellow) appears to be intermediate between the published version and previous versions of this ransomware.
General characteristics
The hashes for both samples are provided in the following table. sample1.exe was analysed months ago, while sample2.exe has been seen in the field during june 2024.
| Name | Sha256 |
|---|---|
| sample1.exe | fb78afe826a14d4e0cc883fcdb6fe339e45a3fe728e575137b231aec6418a18f |
| sample2.exe | 3dabecacc40e2904beba9372e95cf25cec8bb021c080f5d892fbf2eeb0e97006 |
Command-line arguments
Both samples can be executed with options specified via the command line. However, sample1.exe includes, by default, the shutdown of virtual machines. This can be seen during its execution, and there is no option to avoid this behaviour.
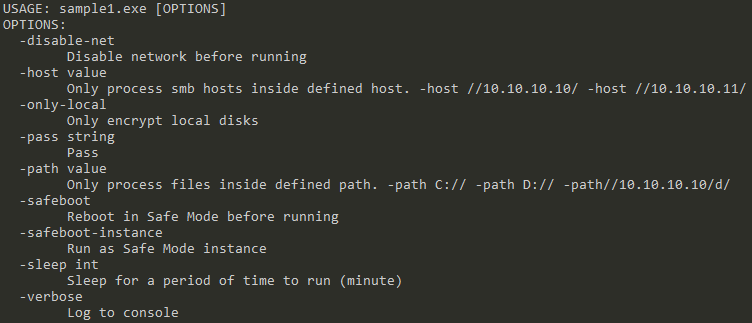
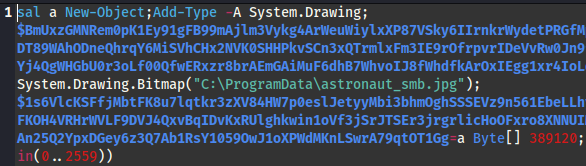
Sample2.exe includes this option, along with the “fast encryption mode”:
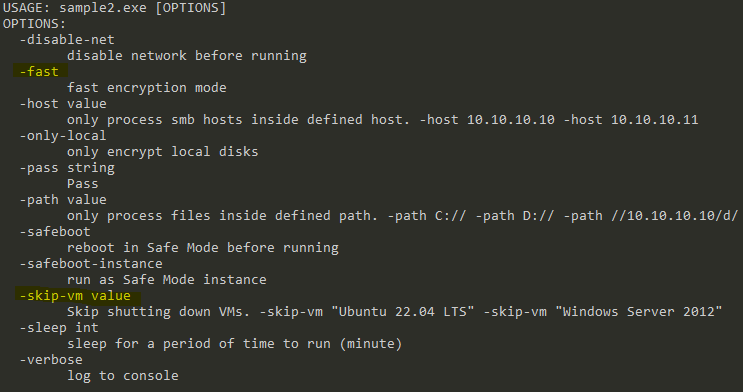
Both samples require a password in order to execute. Moreover, both samples are protected to avoid the static analysis, using obfuscation methods.
Obfuscation methods
RansomHub is developed in Go. It uses an open-source obfuscator called Garble, which hinders analysis in two ways.
The first is by removing module names and replacing some with random character strings. To recover some module names, the GoReSym tool can be used, with usage instructions available on its respective GitHub page.
The second method is by obfuscating the executable strings. To decrypt them, the script described in the OALabs report can be used. It is important to note that this script does not decrypt all the strings, as some functions are optimized, causing the pattern to stop working.
Infection chain
The samples were deployed using different tactics. In case of sample1.exe, the actors behind the attack used tools such as Advanced Port Scanner and ScreenConnect between others, in order to discover devices to be infected.
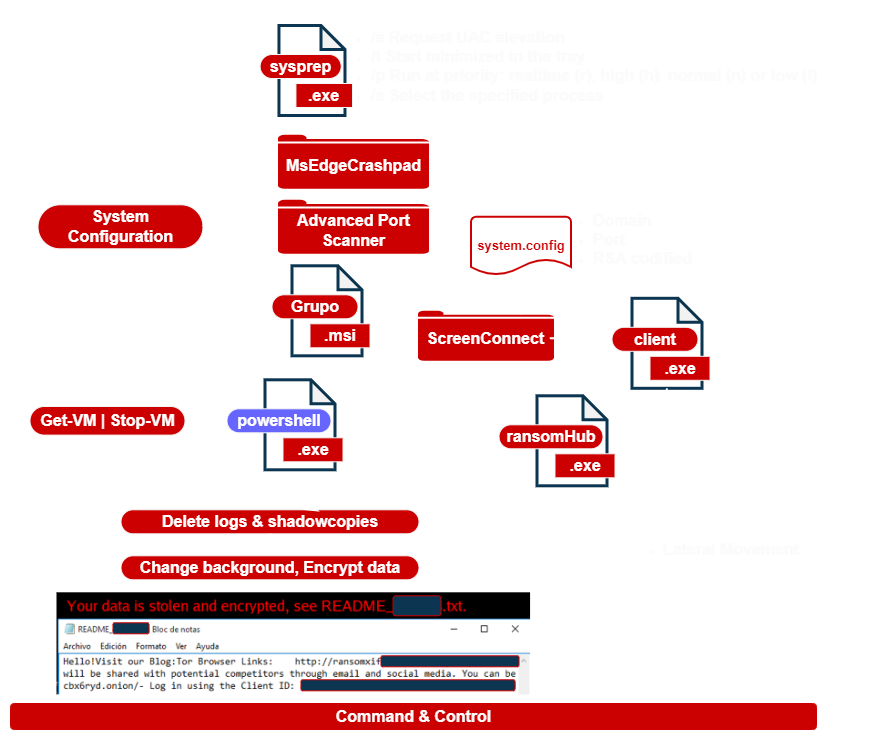
During the deployment of sample2 the cybercriminals used obfuscated PowerShell scripts with execution delay.
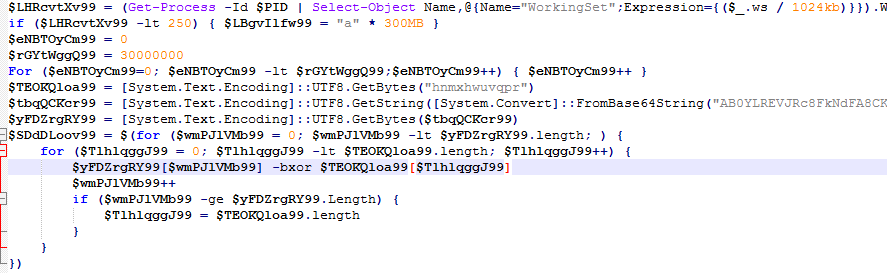
The script can be successively deobfuscated until a dependent file is revealed, whose name change in different deployments.
About RansomHub
RansomHub is a Ransomware-as-a-Service (RaaS) group emerged in 2024, although its code has been linked to the code of Knight ransomware (for sale on underground forums in February 2024), according to Symantec researchers.
This RaaS group made headlines after BlackCat affiliates, who had previously involved in the attack on Change Healthcare, targeted the organization again, this time with RansomHub. Therefore, this group has been seen as an alternative to other groups whose popularity may have been negatively affected in recent months.
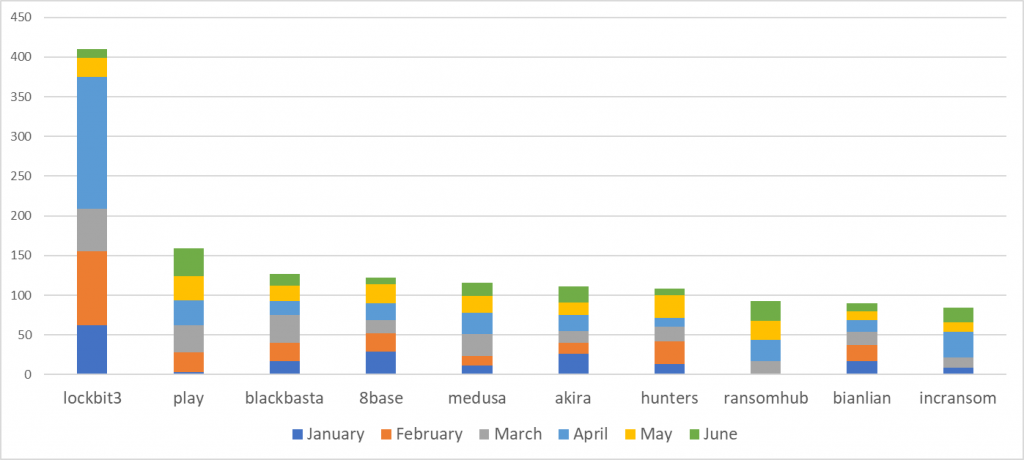
During the month of June, RansomHub has been one of the ransomware groups with the most impact globally, according to public sources processed by Lab52. The next graph shows the approximate number of victims by month.
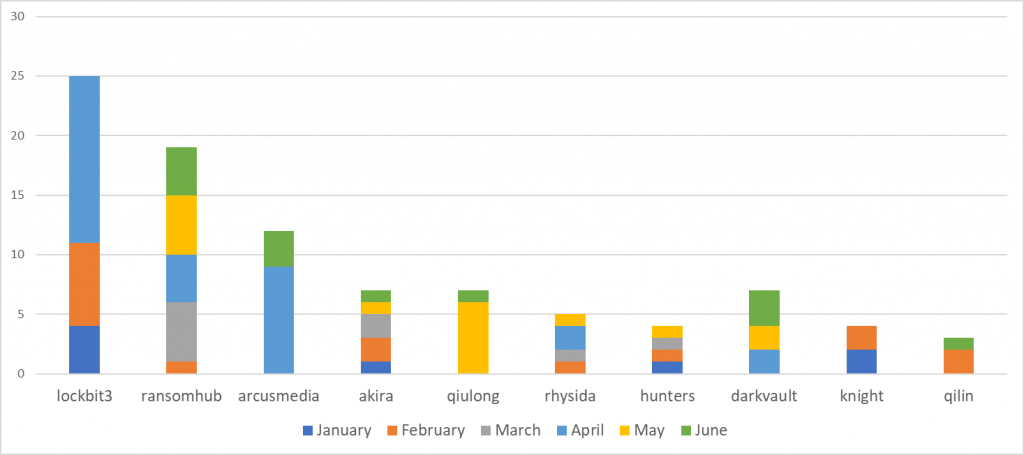
The impact of RansomHub in Latin America was documented in the latest ransomware report for Q1 2024 conducted by the Lab52 (S2 Grupo) team. In this case, during the last quarter this group reaches the second position mong the groups with the greatest impact in the region.
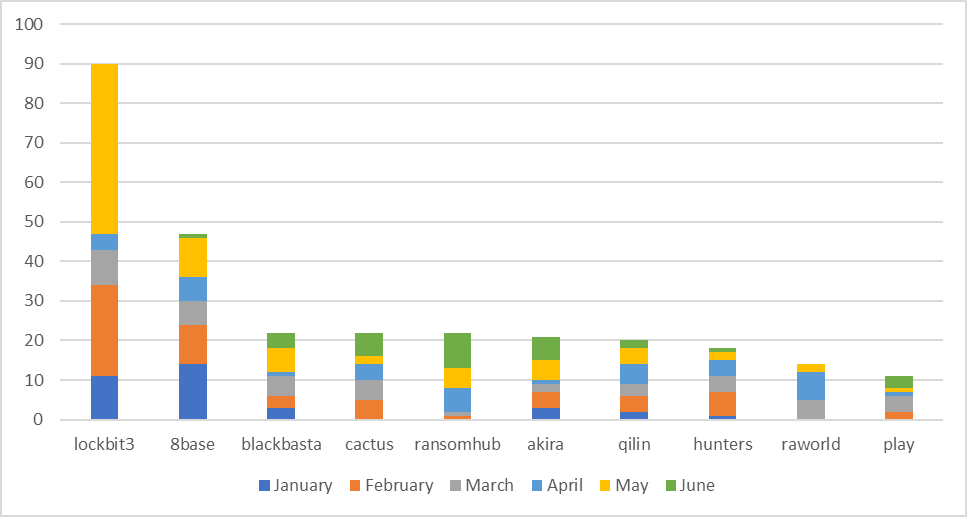
Considering Europe, this group reaches during june the fourth position in June, and was the group with the highest number of known victims.
Therefore, both globally and regionally, it is evident that the impact of this group has increased during the last quarter and could continue to rise. However, this will also depend largely on the deployment tactics employed by the actors behind the ransomware and the capabilities of the ransomware itself to facilitate achieving their goals.
Tactics, Techniques and Procedures (TTP)
- T1190 Exploit Public-Facing Application
- T1133 External Remote Services
- T1016 System Network Configuration Discovery
- T1082 System Information Discovery
- T1588.006 Vulnerabilities
- 1057 Process Discovery
- T1562.009 Safe Mode Boot
- T1562 Impair Defenses
- T1018 Remote System Discovery
- T1105 Ingress Tool Transfer
- T1562.001 Disable or Modify Tools
- T1219 Remote Access Software
- T1090 Proxy
- T1560.001 Archive via Utility
- T1041 Exfiltration Over C2 Channel
- T1587 Develop Capabilities
- T1587.001 Malware
- T1486 Data Encrypted for Impact
- T1657 Financial Theft
Indicators of Compromise (IoC)
Hashes
| Name | Sha256 |
|---|---|
| sample1.exe | fb78afe826a14d4e0cc883fcdb6fe339e45a3fe728e575137b231aec6418a18f |
| sample2.exe | 3dabecacc40e2904beba9372e95cf25cec8bb021c080f5d892fbf2eeb0e97006 |


Leave a Reply