Turla is an APT group allegedly linked to the intelligence service FSB (Federal Security Service) from the Russian Federation. This threat actor is specifically in the Center 16 unit, which carries out the collection of radio-electronic intelligence on communications facilities. Moreover, the Center 16 is in charge of intercepting, decrypting and processing the electronic message and the technical operation of compromising foreign targets.
Turla’s activity dates back as far as 2004. This actor often carries out exploitation campaigns against organizations from the former Soviet Union countries. Turla usually targets organizations from several sectors as: governments, research centers, embassies, energy, telecommunications and pharmaceutical among other sectors.
This research has resulted in a set of samples which have been found in VirusTotal during early 2024. Below is a timeline of the publicly known samples.
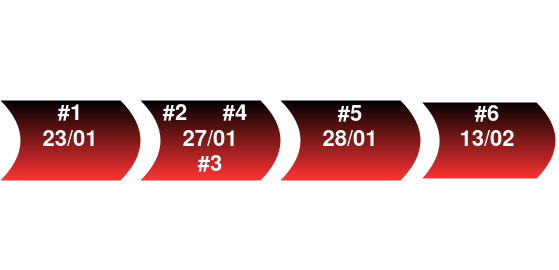
In particular, in this article, one of the samples used in one of the latest campaigns (sample #6). This investigation reveals how Turla is using a new wrapper of Kazuar as part of their infection chain. The most prominent aspects of the analysis leading to the extraction of Kazuar and the peculiarities of the identified sample compared to others previously seen in the field are detailed below.
Infection Chain
As will be detailed later, the attack is quite targeted, so it is possible that the actors have deposited this piece of malware on the computer after a previous infection.
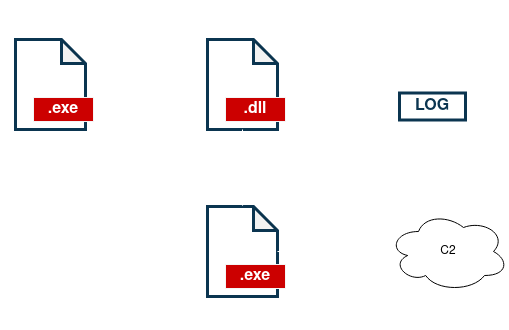
In order to hide the malware, the actors make use of the Sideload DLL technique, spoofing legitimate libraries related to “SkyTel“, “NVIDIA GeForce Experience“, “vncutil” or “ASUS“.

As a result, when the legitimate application is executed, the malicious Dll (We’ve dubbed it Pelmeni Wrapper) is loaded and the infection continues. The resulting infection chain would be as follows :
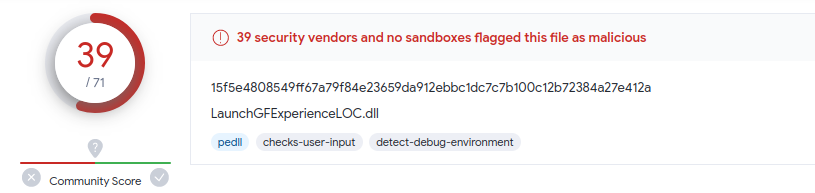
For the analysis we will use the most recent sample we have found in public sources, where it has up to 39 detections.
| LaunchGFExperienceLOC.dll | 15f5e4808549ff67a79f84e23659da912ebbc1dc7c7b100c12b72384a27e412a |
The DLL does not provide much information since most of its content is encrypted. The most interesting thing is the name of its exported functions that appear to be randomly generated.
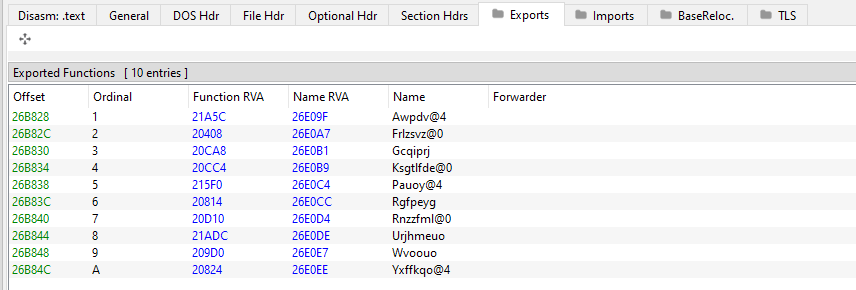
Pelmeni Wrapper (Wrapper DLL)
Through the analysis of LaunchGFExperienceLOC.dll, we see at the EntryPoint, 3 main functions that will guide the program.
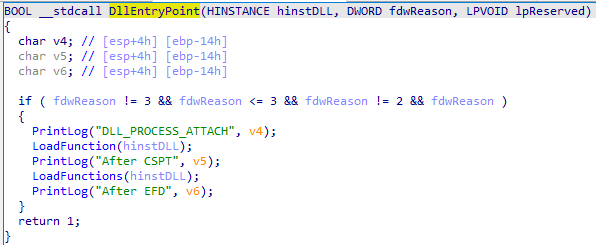
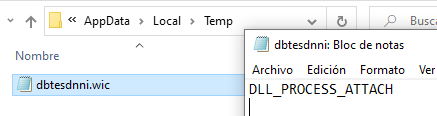
The first function “PrintLog” is in charge of creating a file in the %TEMP% folder that prints what it is doing. This file has a random name and extension, decoded using an XOR algorithm.
At this point it would print “DLL_PROCESS_ATTACH” because the executable has loaded the DLL.
The next EntryPoint function is “LoadFunction” which is responsible for executing one of the exported DLL functions.
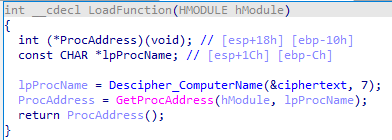
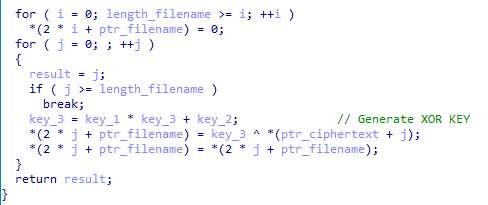
To decrypt the function name, the malware uses a hash generated by the victim’s “ComputerName” xored by a constant. The algorithm used to hash the computer name is Jenkins’ one_at_a_time. This hash will be used as a seed in the pseudorandom number generator algorithm ranqd1. The generated values will be used to decrypt the function name.
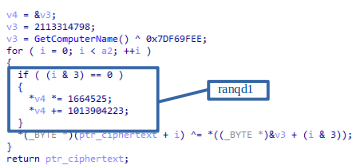
The execution continues with the “Wvoouo” method that goes through all the threads of the running process and suspends them, except for the current thread. After this, Pelmeni prints “After CSPT” in the log, which could be a reference to “Check Suspend Threads”.
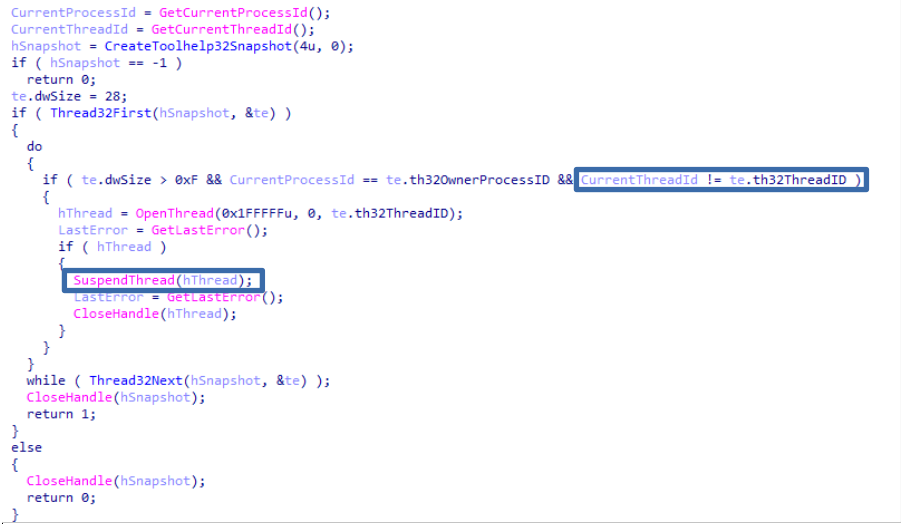
After this the program executes “LoadFunctions” which loads and executes 3 functions as before.
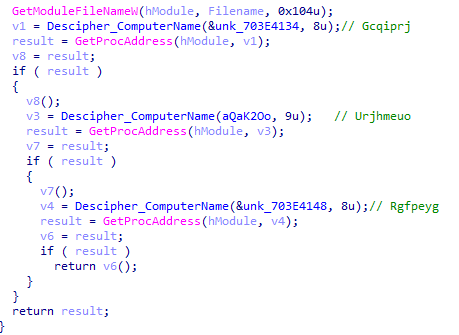
In the first function “Gcqiprj” we can see how, by means of CreateThread(), it creates a thread that will continue with the execution of the wrapper.
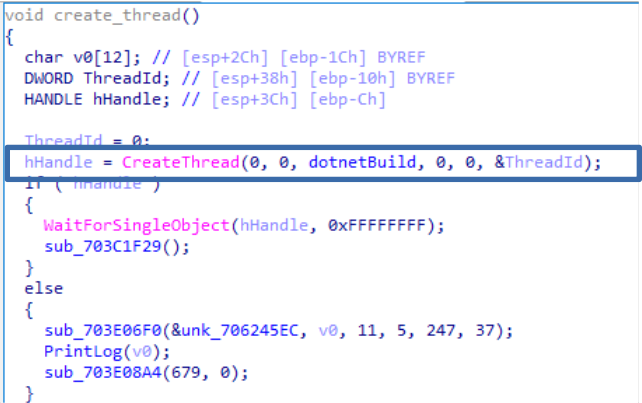
However, instead of executing that part of the code, it saves its address (0x703C1785) to later redirect the execution flow to it.
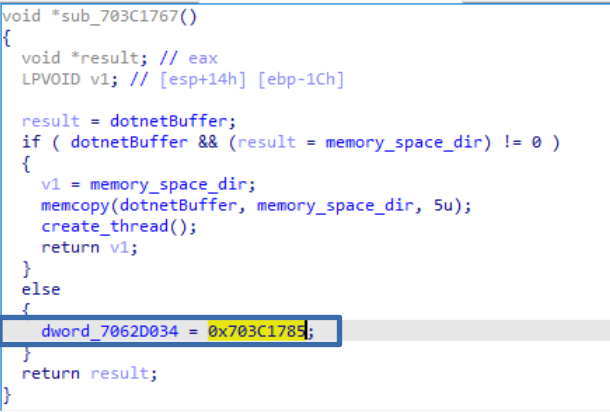
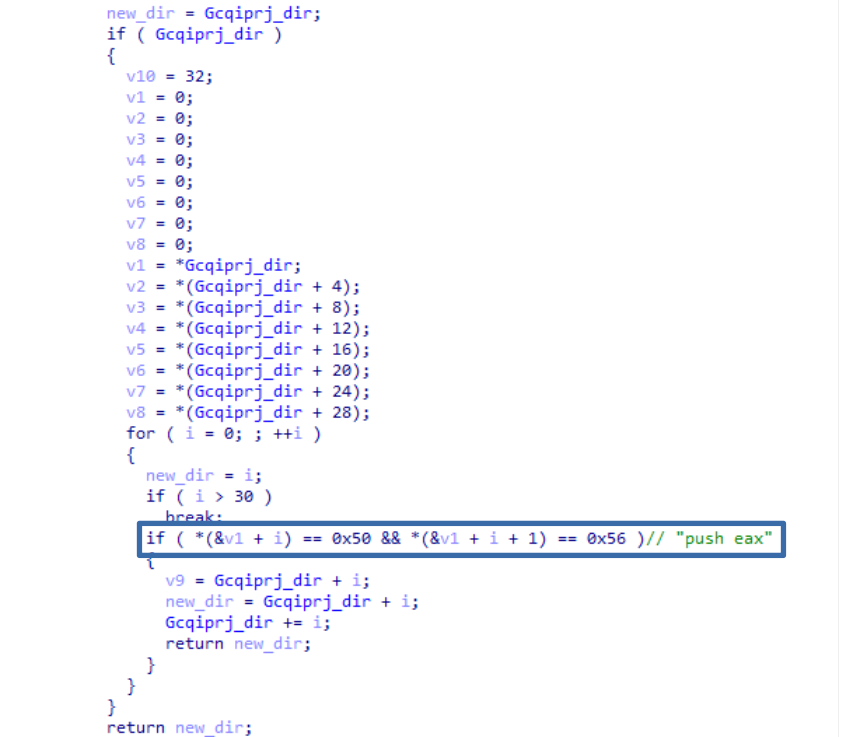
The next function ”Urjhmeuo” accesses the contents of that address (0x703C1785) and copies the entire contents to another memory space, which it will execute. In addition, it adds the instruction “push eax” (0x50 x56) at the beginning to keep the state of the stack correctly. of the stack.
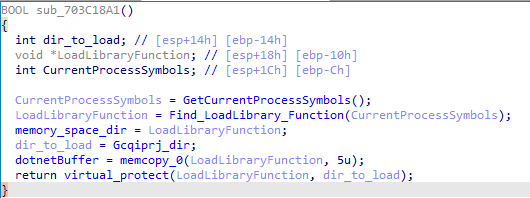
The last function “Rgdpeyg” traces the execution stack to find the “LoadLibrary” function and load the new address, to completely change the execution flow. Finally, Pelmeni prints in the log file “After EFD” which could stand for “Execution Flow Deviation”.
At this point, the malware will execute the thread it had previously prepared. This thread will decrypt a .NET assembly and execute it from memory. Additionally, while Pelmeni runs .NET in the background, it checks the connection by making requests to Google.
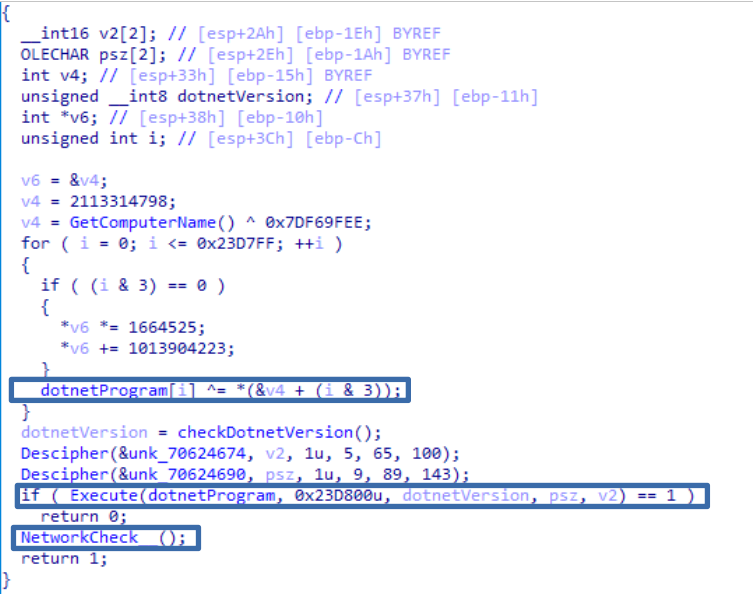
As seen the attack is totally targeted, as if the malware is executed on an other machine, it will not be able to continue the infection. Fortunately, the algorithm used to to decrypt the payload and the one used to decrypt the exports is the same, which makes it vulnerable to brute force attacks.
The following section describes the analysis of the .NET binary extracted.
Kazuar (DotNET)
Analyzing the code, we observe that it is obfuscated and encrypted. The algorithm used is a substitution algorithm reminiscent of the one used by Kazuar (Turla backdoor). The hypothesis is confirmed when comparing our sample with the sample analyzed in the Unit42 article.
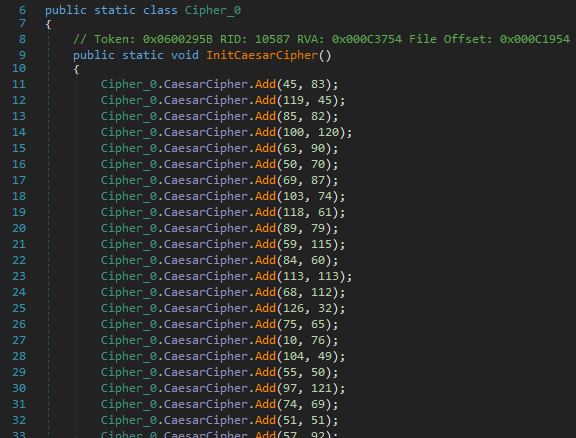
Kazuar is a mutiplatform trojan used by Turla and discovered in 2017, it is often seen in infections targeting specific objectives, with the sample tailored to the targeted entity.
Considering the Unit42 article, in this case the backdoor shows two differences detailed bellow:
- New protocol used for exfiltration
- Different log’s folder
Exfiltration methods
Up to now, it was publicly known that Kazuar supports 5 protocols for exfiltration. The version of Kazuar described here allows the exfiltration of data using socket.
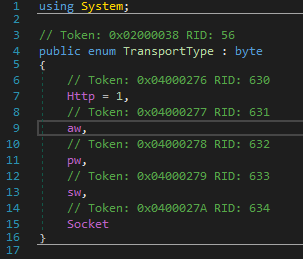
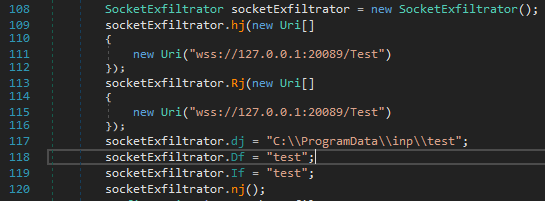
Based on this, it wouldn’t be unreasonable to think that other variations of this sample might also include additional protocols.
Log’s folder
Another variation in this sample compared to previous reports is the directory used for logs, as shown in the following image.
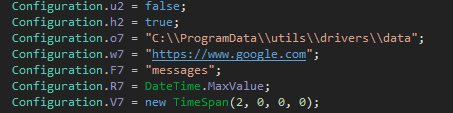
However, this should be considered a minor variation that could be seen in other samples.
Conclusions
This article analyzes a new sample used in Turla campaigns. The sample employs a wrapper that we’ve nicknamed Pelmeni, and deploys the Kazuar malware, with some peculiarities different from those seen in previous articles about this type of sample.
There are samples of the malware available in public sources, although their content is encrypted, which can hinder identification. In the case at hand, the differences of this new threat are shown, and indicators of compromise are provided to aid in its possible detection.
Additionally, in the IOCs summary, the IOCs values highlighted during this post are included. But, also, the hashes for the samples used in the “samples timeline” are provided.
IOCs
Sample #6 [13/02/2024]
| LaunchGFExperienceLOC.dll (Pelmeni Wrapper) | 15f5e4808549ff67a79f84e23659da912ebbc1dc7c7b100c12b72384a27e412a |
| Relapsed.exe (Kazuar) | 7ae9768b79a6b75f814a1b7afaf841b1a4b7ba803b3d806823e81d24a84fd078 |
| Pelmeni Wrapper’s log file | %TEMP%\dbtesdnni.wic |
Kazuar folders
| C:\\ProgramData\\utils\\drivers\\data |
| C:\\ProgramData\\inp\\test |
Sample #5 [28/01/2024]
| asio.dll (Pelmeni Wrapper) | cccd6327dd5beee19cc3744b40f954c84ab016564b896c257f6871043a21cf0a |
| Sobroutine.exe (Kazuar) | 6559d6cb2976334776ded3e7f8ce781c0e6fbaa69edbb0f16b902d06b5d8d8d9 |
| Pelmeni Wrapper’s log file | %TEMP%\iiuiajmujrca.zso |
Sample #4 [27/01/2024]
| vncutilLOC.dll (Pelmeni Wrapper) | 2164d54c415b48e906ad972a14d45c82af7cab814c6cf11729a994249690ed97 |
| Humanity.exe (Kazuar) | 564b2a3083e55933e4ce68b87c5e268c88d58f7ab41839e5a6e0c728a58e9cf2 |
| Pelmeni Wrapper’s log file | %TEMP%\ktynlijyog.dyg |
Sample #3 [27/01/2024]
| SkyTelLOC.dll (Pelmeni Wrapper) | 00256c7fd9a36c6a4805c467b15b3a72dbac2e6dbd12abe7d768f20ce6c8f09f |
| Inroad.exe (Kazuar) | 1a3cc19345737bc76bcf61005ad6afeeea78540bddc627db052cede7a4c0d8e5 |
| Pelmeni Wrapper’s log file | %TEMP%\oayvonjwivaq.vjg |
Sample #2 [27/01/2024]
| vncutilLOC.dll (Pelmeni Wrapper) | ebf10222bdd19bd8f14b7e94694c1534d4fe1d1047034aee7ffe9492cad4a92f |
| Denigrating.exe (Kazuar) | c91891c297971f46c470ea3b1934e5fb76f683776ba3edcdc1afe4f5398fc016 |
| Pelmeni Wrapper’s log file | %TEMP%\jecvxqyvdbri.olc |
Sample #1 [23/01/2024]
| vncutilLOC.dll (Pelmeni Wrapper) | 9b97e740b65bc609210f095cd9407c990a9f71f580f001ea07300228c5256d62 |
| Arches.exe (Kazuar) | 0e8cedf69e0708f77b8d8c7c9b96bf9386f0ec66c48b973bfa9718915ed260e9 |
| Pelmeni Wrapper’s log file | %TEMP%\wcijgmcpyn.ctl |
C2
| hxxps://altavista[.]rs/wp-includes/ID3/PerceptionSimulation/ |
| hxxps://m6front.sam-maintenance[.]com/wp-includes/customize/assembly/ |
| hxxps://bibliotecaunicef[.]uy/catalog/notices/tags/ |
| wss://127.0.0.1:20089/Test |




Leave a Reply