Recently, a somewhat more elaborated phishing has caught our attention at Lab52, it consists on a malicious office document of a real article from Samaa.tv published on 07-10-2019, one of the most important media in Pakistan. The article used in this campaign is related to the current rise of tension in the geopolitical Indian-Pakistani conflict with Kashmir. The headline of the article is: “India to become center of extremism under Modi: AJK PM” ([1]).

The document, with name “India’s_Extremisms_Under_Mobi.docx” and hash “167062593cb9e42a404dc9c8a0347e74888712a1256731724417e6f1d411cbbb” was written in English, an official language for both countries. The startling headline selected in the campaign tries to attract the attention and interest of the Pakistani and Indian people through the social fear. So the main target would be more focused to the Pakistani victims to download the malicious document. At the moment, Delhi and Islamabad claim the control of the whole Kashmir area. However, each public administration manage a concrete area of the region ([2]) ([3]).
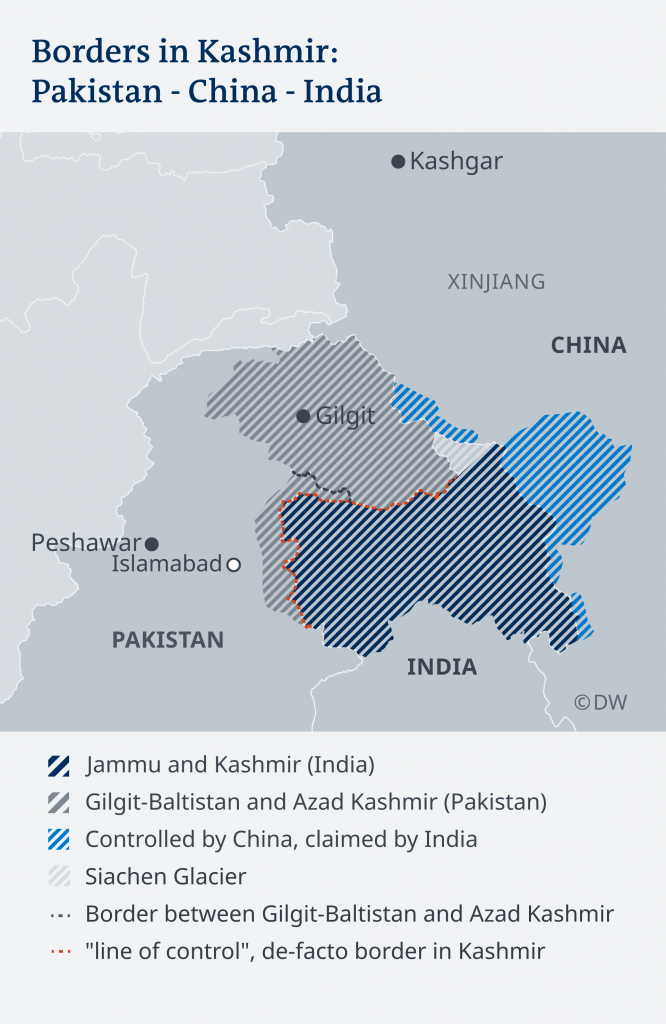
China is also involved in this geopolitical scenario as China is carrying out an important investment in Pakistan, especially in the “China-Pakistan Economic Corridor”. A public officer from Beijing declared that if there is any unacceptable geostrategic movement from India, China would defend the legal right of Pakistan in the Kashmir’s area ([3]).

The economic and trade geopolitical interests of China in Pakistan are highly relevant. Currently, it is relevant the investments of China in Pakistan to keep developing the China & Pakistan economic which will join to the OBOR’s route until the Gwadar and Karachi Port ([4]). The Indian claim to control of the whole Kashmir area, means an important approach of India to the Economic Corridor of China-Pakistan, this geopolitical situation provokes discomfort to both partners as their logistical project would be in danger to be disrupted. As it is showed; China, Pakistan and India are showing more interests in the Kashmir area.
The document appeared in public sources around 15-10-2019 and the internal data of the document dates from the 12-10-2019 so it seems a recent campaign. When the document is opened, the MSOffice Word editor process is constantly suspended and acts in an unstable way. Analyzing in depth the document, it can be observed that it contains a file called image1.eps that corresponds to a Flash element of the document that exploits the adobe Flash vulnerability known as “CVE-2017-0261”.
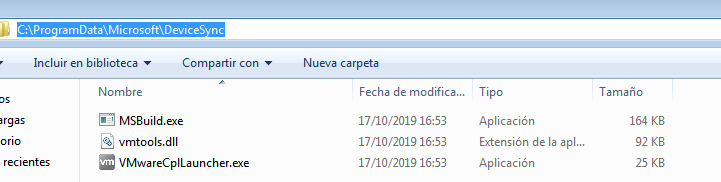
The exploit executed by the document contains a shellcode that dumps into the folder “C:\ProgramData\Microsoft\DeviceSync” 3 executable files, two of them related to VMWare, and one named “MSBuild.exe”. After creating these files, the shellcode runs the binary named “VMWareCplLauncher.exe”..
As described in this Unit42 report [6], the executable “VMWareCplLauncher.exe” is a signed binary from VMWare and the DLL is also a legitimate part of VMWare, which is automatically loaded by the executable, and has been modified to create in this case two scheduled tasks:
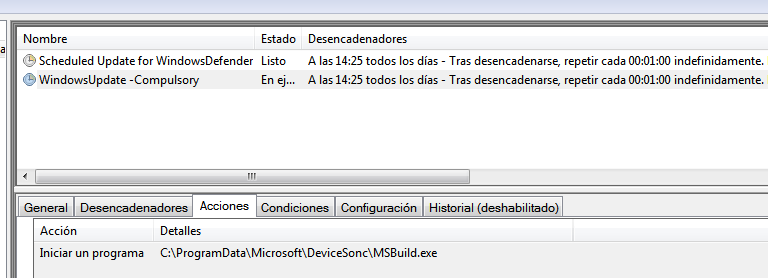
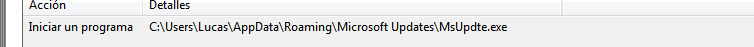
The first task, points to the yet seen executable “MSBuild.exe” and the second to a binary that isn’t generated at any time of the infection and that could point to a next stage of infection that may be downloaded after a “recon” of the infected machine made by this fist stage. After a minute, the task programmed with the name “Windows Update…” launches the MSBuild.exe binary, which consists of a first stage trojan, with a multitude of capabilities described below.
This sample contacts the domain “yetwq.twilightparadox.com” through the HTTP protocol to which constantly sends information collected from the victim computer, together with the parameter “crc=e3a6” which is “hardcoded” in its logic.
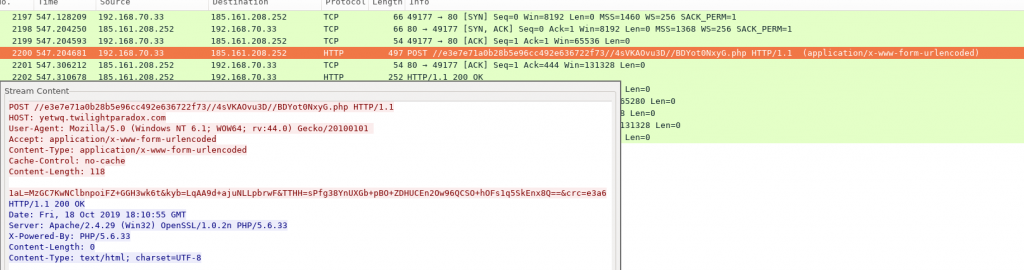
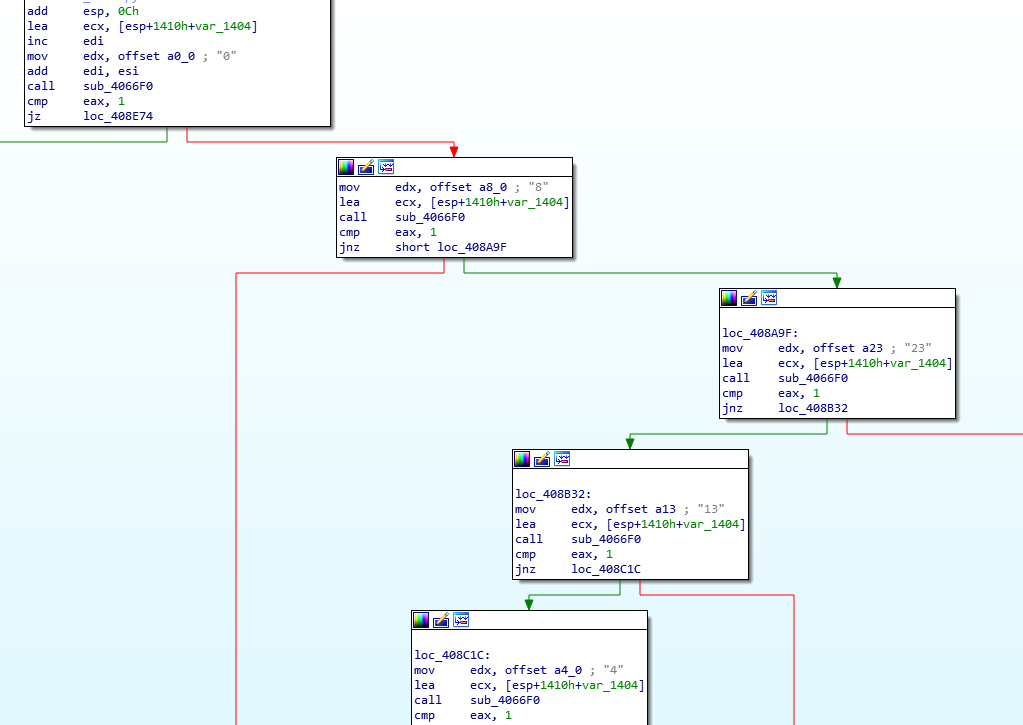
The response of the server is checked in its logic, in search of one of the following numbers “4, 5, 8, 13, 23, 33” which correspond to different commands related to the download and execution of other binaries, keyboard monitoring, sending screenshots to the command and control server or theft of files with the following list of extensions: “doc:docx:pdf:ppt:pptx:jpg:jpeg:png:rtf:txt:7z:rar:zip:docm:msg:wps:xps:pptm”.
Both its capabilities and its code are practically the same as those described by Unit42 in reference to the BadNews threat. In the same way, the TTPs of the entire infection chain coincide with those described in several reports in relation to campaigns that have been attributed to the Patchwork group also known as “Dropping Elephant” or “APT-C-09”.
Furthermore, due to the characteristics of the campaign and the current geopolitical scenario in the area, it seems that its main targets could be located in Pakistan and would be linked to the Chinese-Pakistani Economic Corridor (CPEC) route.
IOCs:
| 167062593cb9e42a404dc9c8a0347e74888712a1256731724417e6f1d411cbbb |
| 6b656dc98773255cbc3592122db6487326e39b8e01966cca174dde87e72f82ec |
| 5f5a1af57872610aa692ee3d0fba4a0171c2ec1a8cc3cf45f21f52caa2ab9041 |
| 31c913899d50d78f2d7d9657e7534bd36819ec9571566216f1c963bf605417f7 |
| yetwq.twilightparadox.com |
| 185.161.208.252 |
References:
[1] https://www.samaa.tv/news/2019/10/india-to-become-center-of-extremism-under-modi-ajk-pm/
[2] https://www.bbc.com/news/world-asia-india-49737886
[3] https://www.dw.com/en/pakistan-thanks-china-for-support-on-kashmir-issue/a-50745277
[4]https://www.dw.com/en/belt-and-road-forum-is-the-china-pakistan-economic-corridor-failing/a-48473486
[5] https://attack.mitre.org/groups/G0040/
[6] https://unit42.paloaltonetworks.com/unit42-patchwork-continues-deliver-badnews-indian-subcontinent/




Leave a Reply