The information that has come to light in recent months, especially Mueller’s accusation, has identified different tactics and techniques of the GRU, some of them previously known – and in many cases linked to APT28 – and others that, although we could all imagine, no one had previously confirmed. These TTPs are summarized in the following table, based on an adaptation of the tactics and techniques published by MITRE in its ATT&CK framework:
| TACTICS | TECHNIQUE |
| Recognition | OSINT |
| Recognition | Recognition activo |
| Intrusion | Relationships of trust: exploitation of third parties to reach the final objective |
| Intrusion | Use of valid credentials, obtained in some cases thanks to spearphishing attacks |
| Intrusion | Spearphishing through harmful links in emails, with URL shorteners |
| Intrusion | Spearphishing through harmful attachments (MS Office) |
| Intrusion | Close Access |
| Execution | Exploition of vulnerabilities at the client’s |
| C2 | Use of proxies to hinder communications tracing |
| Discovery | Tracking and searching for files and directories |
| Acquisition | Automatic collection of information, both technical -from the victim’s infrastructure – and of intelligence interest through public tools |
| Acquisition | Capture of data entered by the user, for example via keylogging |
| Acquisition | Capture of emails directly from Microsoft Exchange servers |
| Acquisition | Acquisition of endpoint files, via forfiles |
| Acquisition | Screenshots of victims |
| Exfiltration | Data compression prior to exfiltration, using public tools |
| Evasion | Deletion of files to avoid detection or extraction of technical intelligence, with CCleaner |
| Evasion | Deletion of records in compromised systems, to avoid detection or extraction of technical intelligence, using wevtutil (wevtutil cl System and wevtutil cl Security) |
| Persistence | Theft of credentials through public tools and proprietary development |
| Destruction | Encryption and deletion of objects |
As we mentioned before, most of the previous techniques had previously been attributed to the GRU, specifically to APT28 (a good detail can be obtained in [1]), and they fall within those considered “normal” in any NEC operation; nevertheless, of all of them there is one that officially was NOT associated with this group – it does not even appear in Mueller’s accusation -, and therefore with the GRU, until now: close access operations, which although they have been carried out for years by the intelligence services had not been documented in the case of APT28. In 2018, it was confirmed that the GRU deals with proximity operations: of the four members of the Service detained in Holland, two belong to Unit 26165, but the other two do not. One of them, MININ, is identified as a member of Unit 22177: the “Conservatory”, the Military Academy of the Russian Ministry of Defense where intelligence officers are trained. In this way, and always apparently, the two officers of Unit 26165 would be in charge of the technological aspects of the operation, while MININ and SOTNIKOV of the HUMINT and support aspects. These close access operations of the GRU are similar to those executed by the US Special Collection Service: CIA and NSA operatives working together to deploy in hard-to-reach sites./p>
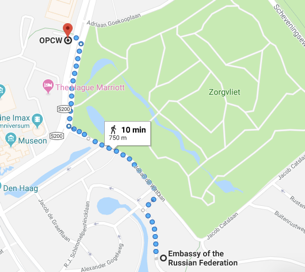
Why does the GRU decide to undertake an operation of this kind to compromise the Organization for the Prohibition of Chemical Weapons? Perhaps the OPCW was a tough target, difficult to compromise with purely cyber techniques (spear phishing, watering hole…) and that motivated the Service to move four people to Holland for the operation. Or perhaps they will take advantage of a security inspection of the Russian embassy in the Netherlands, very close to the OPCW headquarters, as the image shows, to try to compromise this Organization. Or simply the four members of the GRU were, in fact, doing a security inspection, an official alibi but less likely hypothesis if we look at the analysis of seized devices … In any case, the poor operational security measures suggest that the GRU agents at no time considered the operation as risky or imagined that they could be arrested and expelled, as finally happened.
Analysts are also interested in pure CNA activities against Ukraine; if we stick to the tactics exposed by MITRE we should include these actions in the field of “execution” tactics, also exploiting vulnerabilities in compromised systems but not to persist, elevate privileges or exfiltrate information, but to destroy the objectives. But as the relations that MITER exposes are not complete (it is, like almost everything, an excellent work in continuous process), to be technically correct we would be talking about a new tactic, for example “destruction”: the GRU – or APT28, as we prefer – executes blind destructive actions, which do not require persistence or command and control and therefore do not fall within the “standard” tactics of threats aimed at information theft (CNE scope); and the GRU techniques to deal with this destruction go through the non-reversible deletion or encryption of files. Let’s remember again that the GRU is a military intelligence service, so it is not surprising to execute pure destructive operations, independent of information theft, against a target./p>
References
[1] Paul Pols. Modeling Fancy Bear Cyber Attacks. Fox IT Cyber Security Academy. December, 2017.




Leave a Reply