Due to the recent warning published by the FBI about Cuba ransomware (original FBI warning no longer available online for unknown reasons), from Lab52 we decided to publish some information about this ransomware family. Despite the fact that the ransomware has been named Cuba, there is no clear evidence linking the country to the implementation or perpetration of this type of attacks.
Nonetheless, the geopolitical analysis has revealed a few details of strategic interest. Firstly, the fact that most of the countries attacked, according to a McAfee report, correspond to those located in Latin America, North America and Europe. Of these, the most targeted were: Spain, Colombia and Germany. However, when looking at the possible link between the countries attacked and the sectors compromised, it has not been possible to identify a clear interest in the attack, since although Colombia is a US ally in Latin America and a NATO observer state, and Spain is a member of the European Union and NATO with a good geostrategic position, none of them stand out among the critical sectors that have been attacked.
Secondly, it has also been observed that the profile of the countries attacked is common to apt groups that share certain ideological lines, which may be contrary to those of the countries that have been targeted. However, this has not yet allowed us to identify the link between this ransomware and any specific country or APT group.
For this post, we have analyzed a recent public sample, which has a compiler timestamp dated from August 23rd, 2021:
936119bc1811aeef01299a0150141787865a0dbe2667288f018ad24db5a7bc27
In this sample, we have observed some changes from the version described by McAfee in April 2021, which is the only and most recent published analysis about this ransomware family.
Firstly, the process retrieves the Input Locale identifiers (formerly called Keyboard Layout Handles) corresponding to the current set of input languages in the infected system. In case of finding the Russian language identifier (0x19) among the obtained list, the process terminates. Otherwise, it starts with its main activity.
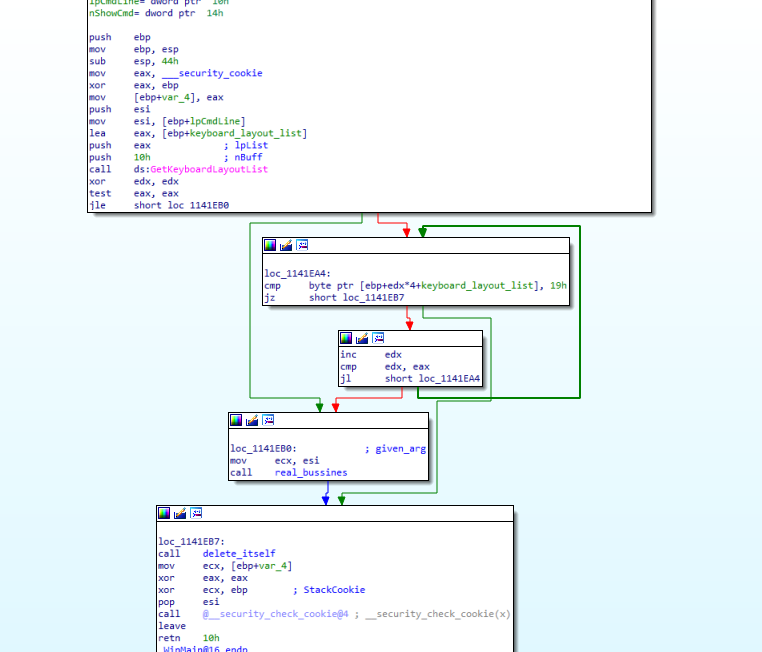
Since the program accepts one argument, the main activity will start by parsing the given argument, looking for either “network”, some IP address, “local” or a specific path to encrypt. Thus, the usage of this sample by an operator would be as follows:
cuba.exe [ network | [IP_addr] | local | [specific_path] ]
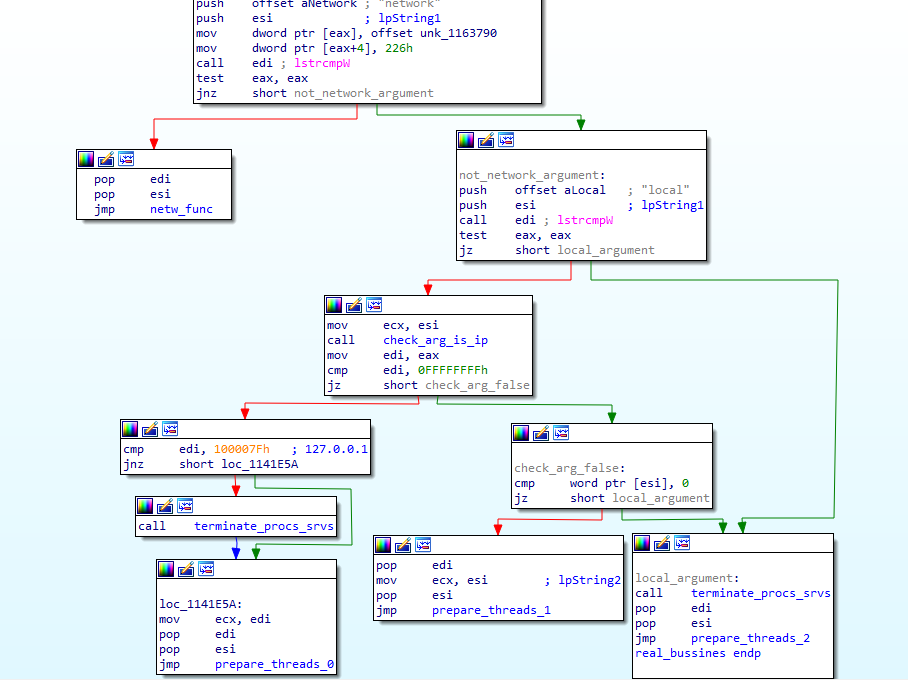
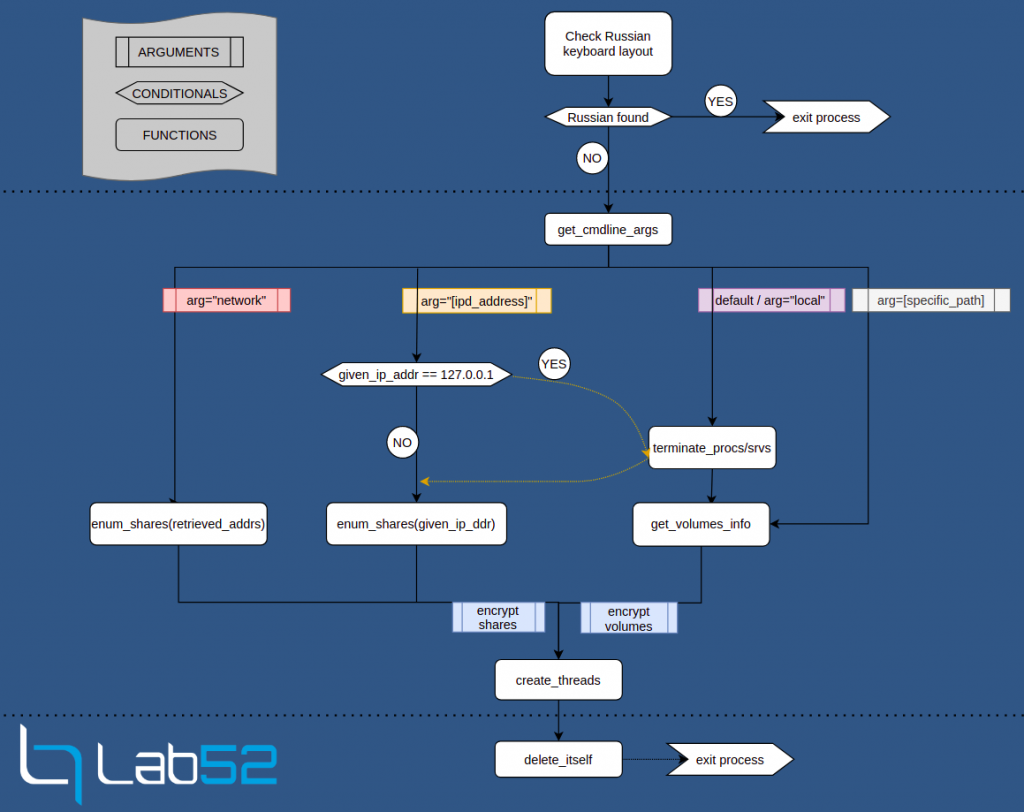
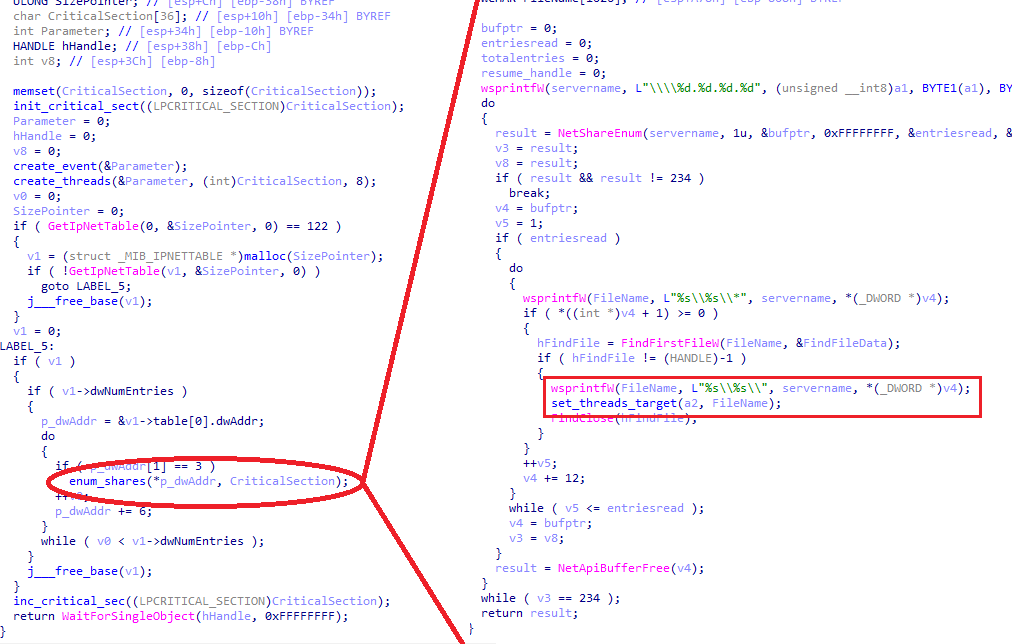
According to this, we could distinguish between two network modes and two local modes. The network mode triggered by the “network” argument will call the windows API GetIPNetTable in order to obtain the ARP table and call NetShareEnum using each IP as the serverName parameter for this second API call. In the case of specifying an IP address, it will just enumerate the shares of that specific address.
The default (no argument given) or “local” argument mode will enumerate the volumes by their Device IDs in the system. If a path is specified as the argument, the ransomware will only encrypt that specified path.
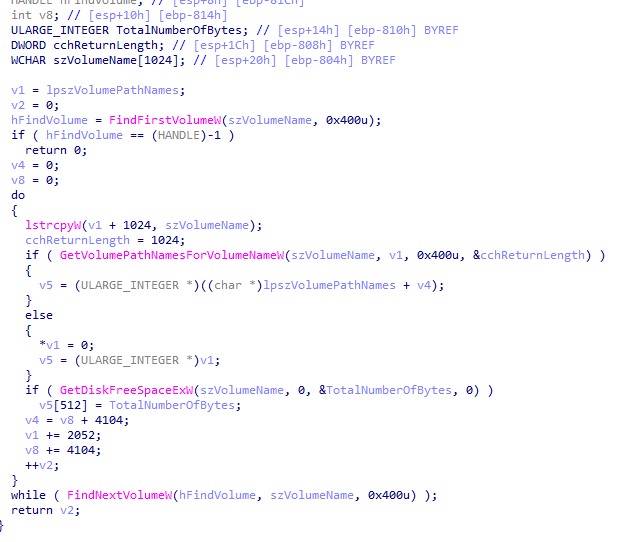
Depending on the case there will be between 2 and 4 threads encrypting the information, which will be created by the same function, for which a different target will be given also depending on the initial argument.
Before starting the encryption there are two different cases where the binary will first terminate some harcoded processes or services. As shown in the elaborated flow diagram, this will happen only if no argument or “local” is given, or if the specified IP address is 127.0.0.1.
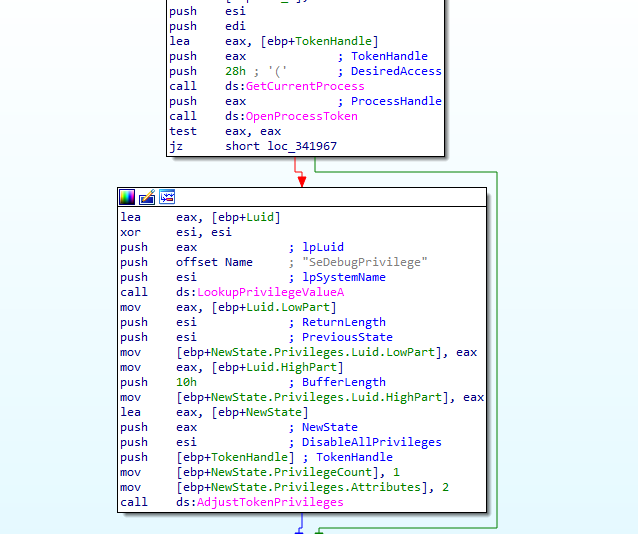
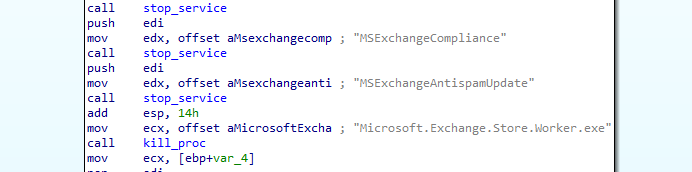
Just like the previous versions, this sample will use SeDebugPrivilege in order to obtain the necessary rights to terminate processes and services, in this sample they only added one new process to terminate: the Store Worker Process (Microsoft.Exchange.Store.Worker.exe), responsible for executing RPC operations for mailboxes on a database.
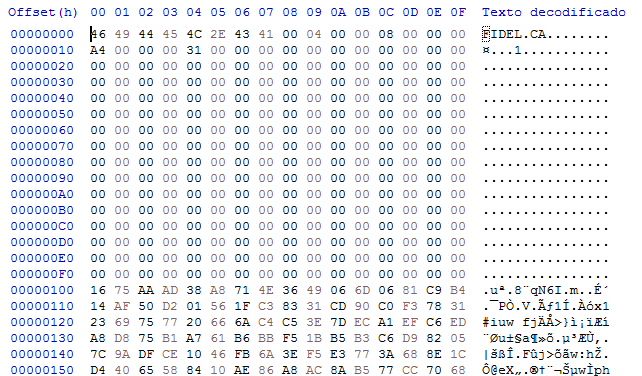
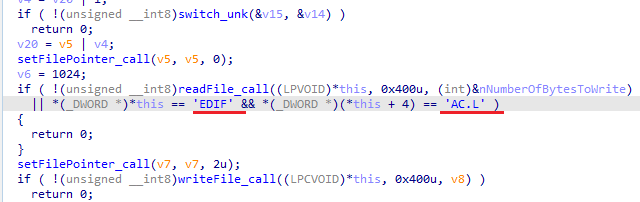
Unlike the majority of ransomware families, two different instances of the same process could be executed at the same time, which could cause interferences between each other. However, to avoid double cyphering, the RANSOMWARE still adds to the encrypted file a 240 bytes header, with nothing but the string “FIDEL.CA” and four extra values in the consecutive words. Before encypting a file, the presence of this “file signature” will be checked.
In the version analyzed by McAfee, they found that their sample could take a different list of arguments such as /min, /max, /dm, /net, or /scan. However, the sample we analyzed only accepts one of the arguments described above. This means that for this version THERE IS NO POSSIBILITY THAT the ransomware operator CAN specify a maximum or minimunm file size to encrypt. Though, large files will only get encrypted their first MB for EVERY 9MB.
Most likely in order to avoid system failures, the ransomware will not encrypt files with extensions .exe, .dll, .sys, .ini, .lnk, .cuba, and it will ignore paths containing “\windows\”.
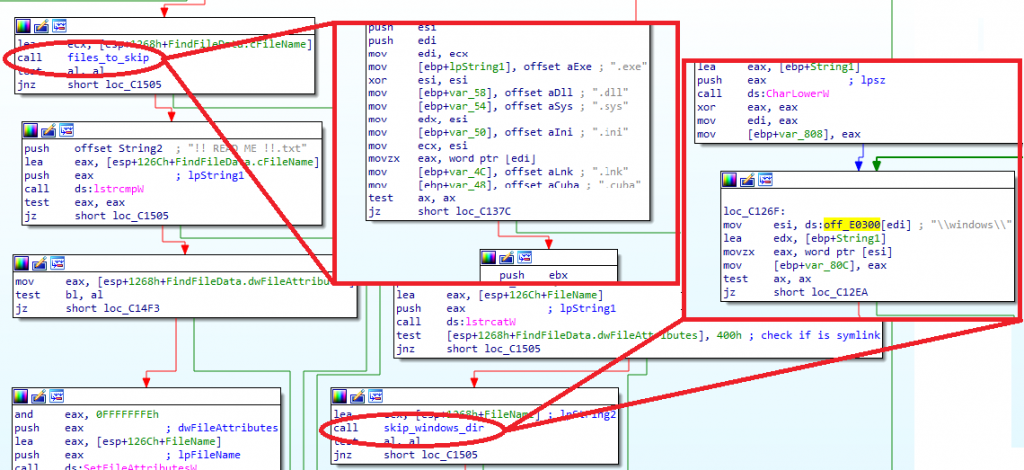
Once the threads have finished the cyphering task, the function to delete itself from disk will be called, INDEPENDENTLY FROM the argument provided, unlike the McAfee sample, where they affirmed that this function would be called when giving the “/dm” argument. For this, the sample will call the Windows API CreateProcessW with “\\system32\\cmd.exe” as the ApplicationName and ” /c \del [exe_path] >> NULL ” as command line arguments.
The complete list of stopped processes and services is shown in the following tables:
| MySQL | MSExchangePOP3BE |
| MySQL80 | MSExchangePop3 |
| SQLSERVERAGENT | MSExchangeNotificationsBroker |
| MSSQLSERVER | MSExchangeMailboxReplication |
| SQLWriter | MSExchangeMailboxAssistants |
| SQLTELEMETRY | MSExchangeIS |
| MSDTC | MSExchangeIMAP4BE |
| SQLBrowser | MSExchangeImap4 |
| vmcompute | MSExchangeHMRecovery |
| vmms | MSExchangeHM |
| MSExchangeUMCR | MSExchangeFrontEndTransport |
| MSExchangeUM | MSExchangeFastSearch |
| MSExchangeTransportLogSearch | MSExchangeEdgeSync |
| MSExchangeTransport | MSExchangeDiagnostics |
| MSExchangeThrottling | MSExchangeDelivery |
| MSExchangeSubmission | MSExchangeDagMgmt |
| MSExchangeServiceHost | MSExchangeCompliance |
| MSExchangeRPC | MSExchangeAntispamUpdate |
| MSExchangeRepl |
| sqlagent.exe | sqlbrowser.exe |
| sqlservr.exe | vmwp.exe |
| sqlwriter.exe | outlook.exe |
| sqlceip.exe | vmsp.exe |
| msdtc.exe | Microsoft.Exchange.Store.Worker.exe |




Leave a Reply