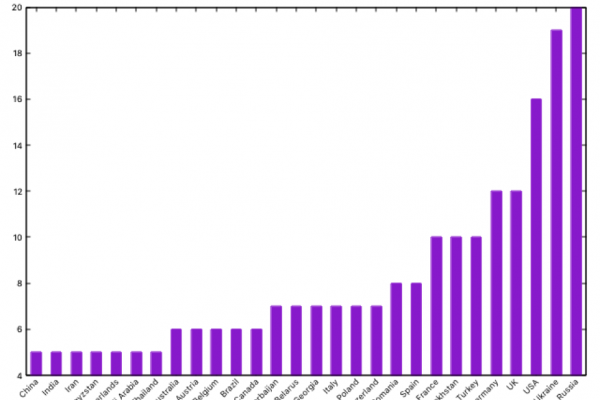
Acquisition and processing When attending to talks about APT -or when giving them- sometimes you hear sentences like “most threat actors are focused on information theft” or “Russia is one of the most active actors in APT landscape”. But, where do all those sentences come from? We have spent a whole night exploiting APT data […]
IOC are dead, long live IOC!
An indicator of compromise (IOC) can be defined as a piece of information that can be used to identify a potential compromise of the infrastructure: from a simple IP address to a set of tactics, techniques and procedures used by an attacker during a campaign. Although when we think about IOC in our mind are […]
The energy reserves in the Eastern Mediterranean Sea and a malicious campaign of APT10 against Turkey
Energy reserves in the Eastern Mediterranean Sea and the “MEDEAST” gas pipeline: The Mediterranean Sea has become an increasingly relevant geostrategic topic for the Ministries of Foreign Affairs of Turkey, Greece, Cyprus, Israel and even China due to the controversies generated during the last decade for the discoveries of natural gas resources located in the […]
How Lab52 free service can protect your organization
Advanced Persistent Threats (APT) represent a risk to organizations, but they can not be deal with the same tools as generic malware. The main difference lies in the financial support they have (for example, governments or organized crime) Among the activities of the APT, one could highlight both espionage that provides strategic and political advantage […]
The role of China in the Persian Gulf and potential cyberthreats:
After the rise of tensions between the US and Iran due to the US military operation that ended the life of the Iranian General Qasem Soleimani and the Iraqi Commander Abu Mahdi al-Muhandis ([12]), Iran carried out an attack with missiles against two US military bases located in Iraq ([13]). These events have generated a […]
CNA tactics: a first approach
Today’s post is a doctrinal and metaphysical one… really, it’s a pain. You’ve been warned 🙂 While talking about Computer Network Operations (CNO) we consider three capabilities or actions: CND, CNA and CNE (Defence, Attack and Exploitation respectively); while CND is obviously about technological defence of IT infrastructures against also technological attacks -not about a […]